Top news of the week: 22.10.2022.
Fine for Shein! Fashion site hit with $1.9 million bill after lying about data breach
The parent company of women's fashion site Shein has been fined $1.
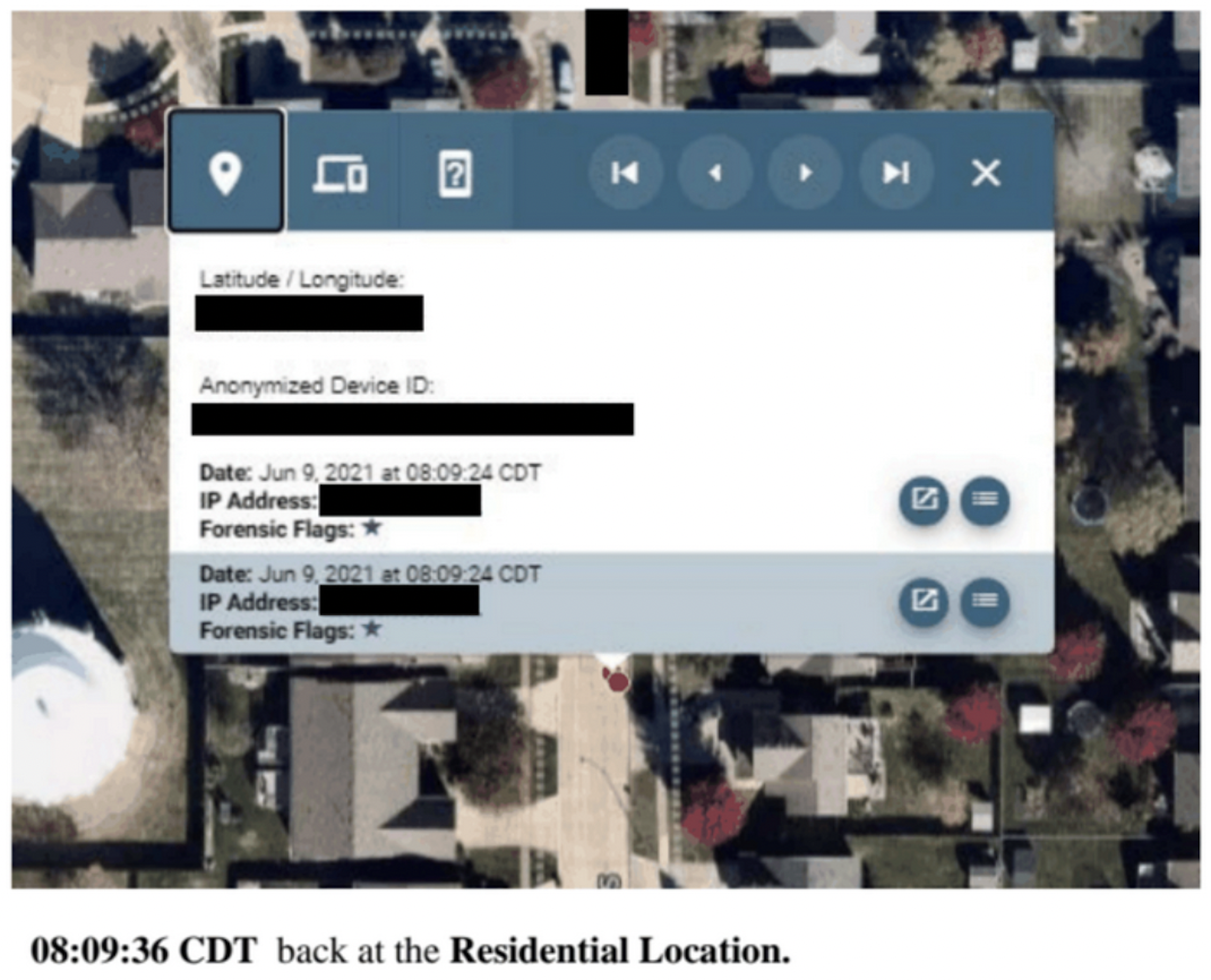
What is Fog Reveal? A legal scholar explains the app some police forces are using to track people without a warrant
Some US law enforcement agencies are using a commercial app that tracks people all day long via their phones – without a court order or oversight.
These cybersecurity tips from a former hacker can make you 98% less vulnerable: ‘You’re raising the bar’
Kevin Mitnick is a former hacker, turned prominent cybersecurity consultant. He offers tips for evading hackers, starting with managing your passwords.
App-layer cryptographic primitives for secure storage of user data
In this blogpost we explore the cryptographic primitives and design decisions we made building our Data Vault module. Our service is a globally replicated, field-level encrypted, data store ...
Chat Control or Child Protection
8 For a survey of UK datasets, see Kairika Karsna and Liz Kelly, “The scale and nature of child sexual abuse: review of evidence”, csacentre.org.uk, 2021; they note ‘no estimate …
Nasdaq_CyberUpdates_Review_092022
For example, 27 government entities in Costa Rica were under attack in April-May 2022, and some of the worst affected included the Ministry of Finance and its two portals, the …