Top news of the week: 26.06.2020.
#cyberattacks #Coronavirus #mobilesecurity #securitynews #infosecurity #CISO #cybersecuritynews #EU #hospitals #Chinese
Threats And Attacks
"Security professionals have less visibility and control over WFH environments... so any evaluation of mobile security should be based on several fundamental criteria" - @anandramanathan via @helpnetsecurity. https://t.co/GIgBhHK35o
OpenHow do I select a mobile security solution for my business?
In order to select a suitable mobile security solution for your business, you need to consider a lot of factors. We talk to experts that can help.
RT @SecurityWeek: US Cybercom Virtual War Game Girds Against Increased Threats https://t.co/GkJTTrqAvo
OpenUS Cybercom Virtual War Game Girds Against Increased Threats
Cybercom accelerated development of a virtual training environment to better analyze ways to protect threats to critical infrastructure, including in energy and transportation systems.
Von der Leyen said #Chinese #cyberattacks on #EU #hospitals cannot be tolerated https://t.co/5r7gdCyQU8
OpenVon der Leyen said Chinese cyberattacks on EU hospitals cannot be tolerated
European Commission President Ursula von der Leyen called out China for launching cyberattacks EU hospitals and health care institutions during the COVID-19 pandemic. European Commission ...
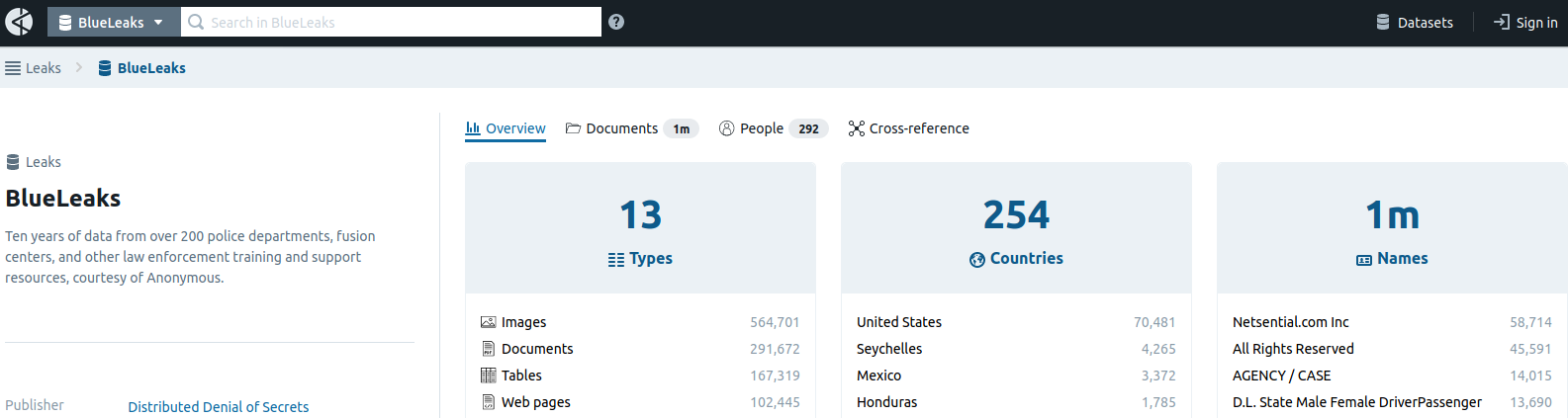
‘BlueLeaks’ Exposes Files from Hundreds of Police Departments
Hundreds of thousands of potentially sensitive files from police departments across the United States were leaked online last week. In a post on Twitter, DDoSecrets said the …
As telehealth grows more common, security experts address the privacy and security concerns of storing health data in the cloud. Read more in this Dark Reading article covering our newest research document on telehealth.
https://t.co/ryBveSMS2C
OpenCloud Security Alliance Offers Tips to Protect Telehealth Data
As telehealth grows more common, security experts address the privacy and security concerns of storing health data in the cloud.
EXPERT REACTION: Major cyber attacks on Aussie governments and business https://t.co/XpcIZkZeBF #cyberattacks
OpenEXPERT REACTION: Major cyber attacks on Aussie governments and business
EXPERT REACTION: Major cyber attacks on Aussie governments and business Prime Minister Scott Morrison has this morning announced Australian organisations, including governments and ...
@cyberdefensemag Publisher @miliefsky Sharing an important story about How to Secure IT And OT #cybersecurity #CYBER #SECURITY in this #CDM #EXCLUSIVE
https://t.co/LfOde6MsK8
by Christopher Dobrec @ArmisSecurity who we hope to see @BlackHatEvents 2020 #CDM https://t.co/JSJ550ULF4
OpenHow to Secure IT And OT In Industrial and Manufacturing Environments
By Christopher Dobrec, Vice President of Product Marketing at Armis Operational Technology (OT) systems, which include critical infrastructure, are increasingly becoming more exposed to ...
Lucifer Malware Aims to Become Broad Platform for Attacks https://t.co/n9RJxejMr2 viay @roblemos #Lucifer #DDoS #cryptomining
OpenLucifer Malware Aims to Become Broad Platform for Attacks
The recent spread of the distributed denial-of-service tool attempts to exploit a dozen web-framework flaws, uses credential stuffing, and is intended to work against a variety of operating ...