Top news of the week: 20.05.2022.
Threats And Attacks
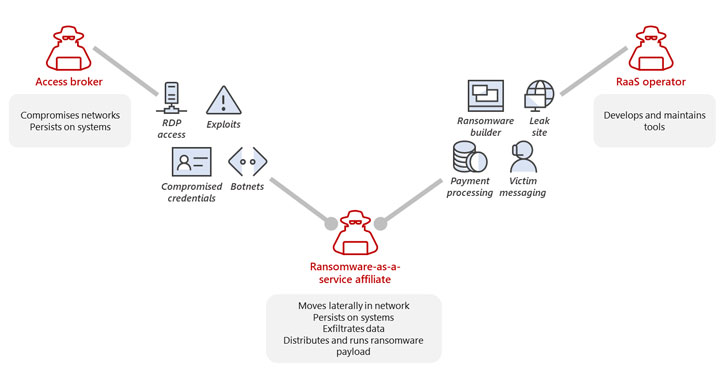
Control Environment Laboratory Resource (CELR)
The Control Environment Laboratory Resource (CELR) is an environment to experience the possible effects of kinetic cyber-physical attacks. CELR allows users to perform security research on ...
Russian Conti Ransomware Gang Threatens to Overthrow New Costa Rican Government
Russian-speaking Conti ransomware gang has threatened to overthrow the newly elected government of Costa Rica with a cyberattack.
The Vulnerable Maritime Supply Chain - a Threat to the Global Economy
An inside look at how merchant vessels and ports are extraordinarily vulnerable to increasingly sophisticated cyberattacks against unmanaged OT systems
Incident Response with Threat Intelligence
Learn everything you need to know to respond to advanced cybersecurity incidents through threat hunting using threat intelligence
How Threat Actors Are a Click Away From Becoming Quasi-APTs
As demonstrated in Ukraine and elsewhere, the battlefield for today's warriors extends to the virtual realm with cyber warfare.
Russian cyber attack on Eurovision foiled by Italian authorities
On Saturday, Italy hosted the Eurovision Song Contest in Turin to an estimated worldwide audience of nearly 200 million people as it was broadcast on TV and live-streamed online.
Are You Investing in Securing Your Data in the Cloud?
Gartner predicts that more than 95% of new digital workloads will continue to be deployed on cloud-native platforms by 2025.
6 Scary Tactics Used in Mobile App Attacks
Mobile attacks have been going on for many years, but the threat is rapidly evolving as more sophisticated malware families with novel features enter the scene.