Top news of the week: 11.11.2022.
Several Cyber Attacks Observed Leveraging IPFS Decentralized Network
A number of phishing campaigns using the decentralized Interplanetary Filesystem (IPFS) network to host malware, phishing kit infrastructure and facil
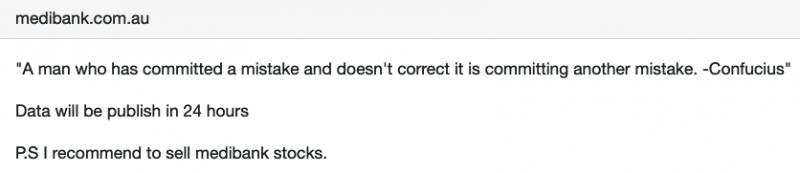
Ransomware Gang Threatens to Publish Medibank Customer Information
The BlogXX/REvil ransomware gang has threatened to publish stolen Medibank customer information shortly after the insurer said it will not pay a ransom.
Cloud9 Malware Offers a Paradise of Cyberattack Methods
The Swiss Army knife-like browser extension is heaven for attackers — and can be hell for enterprise users.
Ransomware Gang Offers to Sell Files Stolen From Continental for $50 Million
A ransomware group is offering stolen Continental data for $50 million after the car parts giant confirms theft of files.
Cybersecurity threats: what awaits us in 2023?
We invited notable experts to share their insights and unbiased opinions on what we should expect from cybersecurity in the following year.
Six ways healthcare organizations can improve connected device security
In its Cyber Insecurity in Healthcare: The Cost and Impact on Patient Safety and Care study for security company Proofpoint, the Ponemon Institute found that most hospitals …
What Ukraine’s cyber defence tactics can teach other nations
Security experts are surprised that Russia’s attacks have not been more effective
Iranian actors targeting healthcare via spear-phishing, vulnerability exploit
The insights detail the three phases of an attack, as well as the aftermath for providers to review. The report also contains a list of commonly exploited vulnerabilities that should be ...