Strategic management, Risk, Organization, Information security, Security, Physical information security
6 Things Every CISO Should Do the First 90 Days on the Job
A CISO's responsibilities have evolved immensely in recent years, so their first three months on the job should look a different today than they might have several years ago.
6 Things Every CISO Should Do the First 90 Days on the Job
A CISO's responsibilities have evolved immensely in recent years, so their first three months on the job should look a different today than they might have several years ago.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Threats & Attacks
Please click on:
Subscribe to Cybersecurity - Threats & Attacks
C-Suite Shuffle: The CISO’s Evolving Role and Reporting Structure
In 1994, Steve Katz became the world’s first chief information security officer (CISO) after Citicorp endured a string of cyberbreaches at the hands of Russian hackers. Katz is an ...
Many Executives Lack Confidence in Healthcare IoT Security, Privacy
Only 37 percent of healthcare executives are “very confident” that they are building sufficient security and privacy controls into their healthcare IoT deployments.
Top 5 cybersecurity challenges for CISOs
As the scope of their responsibilities grows, CISOs are in a more prominent position in many organizations now than in the past, the report noted, working regularly with other members of ...
A CIO guide to building a dashboard for cybersecurity
KPIs, metrics and other must-haves hospitals should track continuously to protect medical and patient data.
Organizations seldom prioritize cybersecurity over business outcomes
55% of large companies are not effectively stopping cyberattacks, finding and fixing breaches quickly, or reducing the impact of breaches.
SANS Cybersecurity Management Curriculum
Summary of SANS Cybersecurity Management Curriculum which is developing cyber security managers and leaders worldwide.
5 Key Ways CISOs Can Accelerate The Business
Today’s security leader is also a business executive. Here’s how to thrive in both roles.
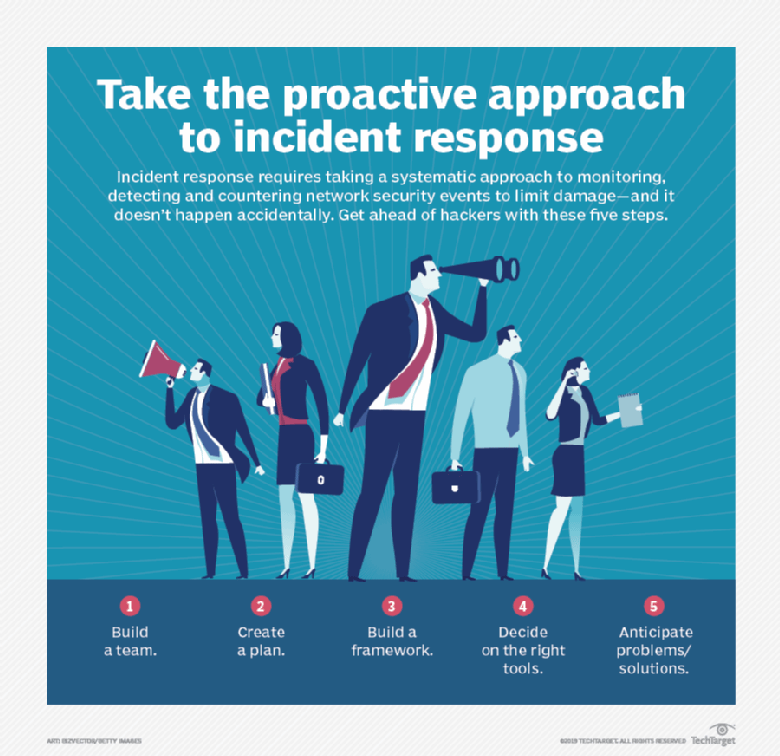
Ultimate guide to cybersecurity incident response
This comprehensive cybersecurity incident response guide tells how to create an IR plan, build an IR team and choose technology and tools to keep your organization's data safe. It explains ...
What is a virtual CISO?
This blog was written by a third party author. Organization’s today host a wide range of information that, due to its external value to competitors, nation-states, or cybercriminals, needs ...
The ultimate guide to cybersecurity planning for businesses
In this comprehensive guide to cybersecurity planning in businesses, you'll learn why effective cybersecurity is important to organizations, its business benefits, the challenges that ...
On the Rise: The Enemy From Within
Today’s economic climate exacerbates risks of insider threats, as pending furloughs or pay cuts may tempt employees to exfiltrate data to secure a new job, make up for income losses, etc.
2019 OISC Call for Presentations
Web survey powered by SurveyMonkey.com. Create your own online survey now with SurveyMonkey's expert certified FREE templates.
How cybersecurity supports digital transformation in healthcare
As hospitals have gone digital they are now more vulnerable to cyberattacks. A ransomware incident earlier this fall forced many of the George Washington
Despite Breaches, Many Organizations Struggle to Quantify Cyber-Risks to Business
Enterprises are struggling with familiar old security challenges as a result, new survey shows.
"Know thyself". Ten Commandments for Cyber Resilience Strategy.
The Ancient Greek aphorism "know thyself" (Greek: γνῶθι σεαυτόν, transliterated: gnōthi seauton; also ..
9 Critical InfoSec Tips That Every Internal Auditor Should Master
Cybersecurity is top of mind for most executives and board members, as well as to internal audit. While the information security team may be in charge of measurably reducing cyber risk ...
Zero trust: The trusted model for secure data-driven business
Zero trust doesn't count anyone out as a threat. It's about verifying and mitigating threats both internally and externally.
Starting with strategy – A multi-part series on building a robust cybersecurity program
[ This article was originally published here ]Introduction Today, many organizations look at information security and governance as a baker would icing on a cake. Something you apply at the ...