#security #securitynews #cybersecurity #infosecurity #CISO #itsecurity
Access control, Physical security, Security, Risk, Information security, Computer security
Removing the blind spots that allow lateral movement
There are critical blind spots in most security solutions today that make it difficult to detect and prevent lateral movement attacks.
Removing the blind spots that allow lateral movement
There are critical blind spots in most security solutions today that make it difficult to detect and prevent lateral movement attacks.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Threats & Attacks
Please click on:
Subscribe to Cybersecurity - Threats & Attacks
How Zero Trust architecture improves the organization’s network security
This blog was written by an independent guest blogger. In the cybersecurity field, Zero Trust is becoming a widely used model. Data breaches taught organizations to stay cautious ...
Build cyber resiliency into the enterprise
DXC Technology experts share how cyber resiliency enables organizations to survive attacks, maintain operations and continue to execute their strategy in the face of evolving threats.
What is IAM? Identity and access management explained
IAM products provide IT managers with tools and technologies for controlling user access to critical information within an organization.
Security Product Innovations Run the Gamut at RSAC 2022
The annual RSA Conference spotlights the latest product innovations from security vendors. We’ve rounded up notable releases from Cisco, VMware, Fortinet, and many others.
Hindsight #5: Exclude admin tools with a scalpel, not a sledgehammer
Actions breach victims wish they had taken sooner
Profile of the Post-Pandemic CISO
Age Gender Full names Date of birth Spouse names Email address Phone numbers Home addresses Health conditions Citizenship status Social security number Social media accounts Username and ...
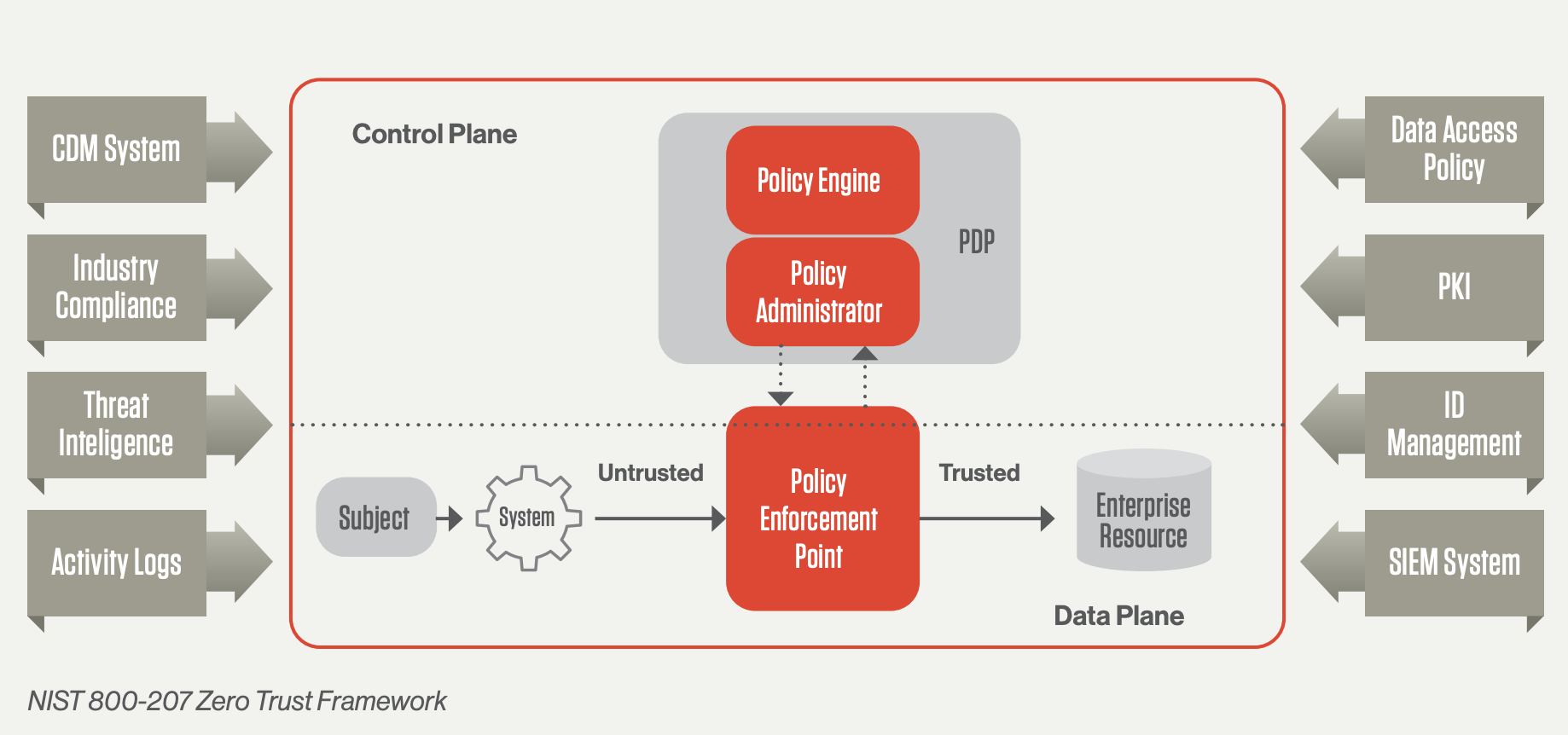
What is Zero Trust Security?
Zero Trust is a security concept that requires all users to be authenticated and authorized before being granted access to applications and data.
Network Security Trends and Acronyms that You Must Know
Network security and management is a complex and ever-evolving field. Here are key trends shaping the sector.
Why User Names and Passwords Are Not Enough
Multi-factor authentication requires several elements for identity verification, making it one of the best ways to prevent unauthorized users from accessing sensitive data and moving ...
Five Cybersecurity Best Practices to Adapt to Geopolitical Crises
Prepare now to address cybersecurity in the aftermath of the Ukraine crisis.
How to Communicate the Identity Security Imperative to Your Board
Despite numerous business-level issues jockeying for space on the board agenda, there isn’t an executive team on the planet that isn’t talking about cybersecurity today. The SolarWinds ...
Breaking News:
How the privacy and security of video meeting apps compare More White House Releases National Strategy for 5G Security More Tokyo Olympics Postponed, But 5G Security Lessons Shine More ...
Keynote Speakers
Regardless of whether organizations’ use of MFA requires SMS messages, authentication applications, or hardware-based security keys, Accenture Cyber Threat Intelligence (ACTI) is observing ...
NY AG Warns Credential Stuff Compromised 1.1M Accounts
New York Attorney General Letitia James has put 17 companies on notice that 1.1 million online accounts have been compromised by cyberattacks involving
Cybersecurity incident response: Lessons learned from 2021
SecureWorks announced the themes and trends of cybersecurity incidents recorded in 2021 so you can better protect your business in 2022.
Examining threats to device security in the hybrid workplace
As employees split their time between office and off-site work, there’s a much greater potential for company devices and data to fall into the wrong hands.
The Daily Ledger
Get The latest cybersecurity news from across the web delivered to your inbox each day.
17 IT leaders on why your organization needs zero trust, with tips on implementation
Top Business Tech shares the insight from 6 IT leaders on why organizations of all sizes need to implement Zero trust, with tips on how to do so.
The security gaps that can be exposed by cybersecurity asset management
Cybersecurity asset management is transforming the way in which enterprises manage and protect their assets.