VMware, Windows Vista, Computer virus, Malware, Microsoft Windows, Forensic science
A Practical Approach To Malware Analysis, Hunting And Memory Forensics
A hands-on training to understand the behavior and characteristics of malware by combining, malware analysis and memory forensics techniques.
A Practical Approach To Malware Analysis, Hunting And Memory Forensics
A hands-on training to understand the behavior and characteristics of malware by combining, malware analysis and memory forensics techniques.
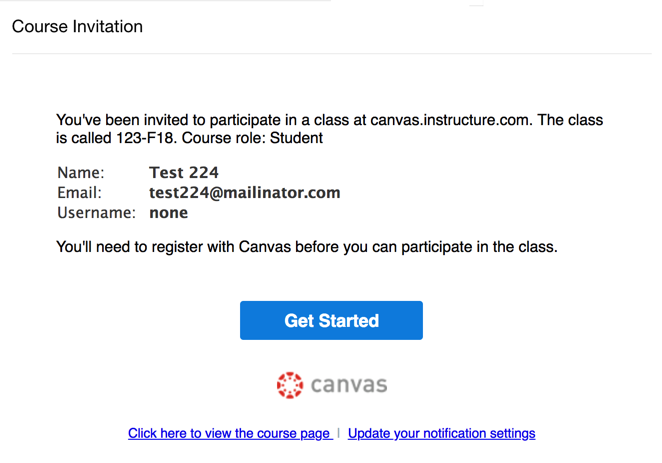
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Threats & Attacks
Please click on:
Subscribe to Cybersecurity - Threats & Attacks
A Practical Approach To Malware Analysis, Hunting And Memory Forensics [HITB2021AMS Virtual]
A hands-on training to understand the behavior and characteristics of malware by combining, malware analysis and memory forensics techniques.
3-DAY TRAINING 2 – A Practical Approach to Malware Analysis and Memory Forensics
DURATION: 3 DAYS CAPACITY: 20 pax SEATS AVAILABLE: 14 EUR2599 (early bird) EUR3199 (normal) Early bird registration rate ends on the 28th of February Overview This hands-on training ...
[HITB CYBERWEEK] A PRACTICAL APPROACH TO MALWARE ANALYSIS, HUNTING AND MEMORY FORENSICS
This hands-on training teaches concepts, techniques and tools to understand the behavior and characteristics of malware by combining two powerful techniques, malware analysis and memory ...
FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques
FOR610 teaches how to perform interactive behavioral analysis of malware, deobfuscate samples, circumvent anti-analysis capabilities, and review key aspects of malicious code for a deeper ...
CNIT 126: Practical Malware Analysis
Local Hosting Hypervisors VMs For VMware: Win2008Malware.7z Size: 2,073,173,278 bytes SHA-256: c2d59bb80d71cb73350fe436d2658eeb46c869edce66c950ce97268e2a2fa25a For VirtualBox: ...
CyberSecurity
(!!! Github shows less than 4000 lines, and more than 5000 lines is missing. Please download Readme.md and open it in markdown viewer to review the FULL version)[Draft]Awesome Cyber ...
Iranian Hacker training Roadmap #SANS once again and for years doing so
کلام آخر پس دوستانی که از مباحت کانال استفاده میکنند اطلاعات خیالشان راحت باشه که دارند سرفصل های دوره هایی همچون SANS رو بصورت FreeContinue reading
How You Can Start Learning Malware Analysis
Next, consider watching my Practical Malware Analysis Essentials talk, which will offer practical tips for analyzing Windows malware in your lab: In addition to watching this video, ...
New Betabot campaign under the microscope
In the past few weeks, the Cybereason SOC has detected multiple Betabot (aka Neurevt) infections in customer environments. This blog will look at the infection chain and delve into ...
Malware Analysis Series - Setting Up a Basic Malware Analysis Virtual Lab
Introduction: Since joining the Cyber Security and Intelligence community in 2016, I’ve always had a strong interest in malware analysis. The process of breaking something down, looking at ...
ServHelper (SSH Tunneling Variant) Analysis
James Quinn, Threat Researcher for Binary Defense Executive Summary Binary Defense Researchers discovered active Command and Control (C2) servers and a new version of ServHelper, a ...
Malware Analysis Using Memory Forensics
Malware analysis can be very simple or very complex. The goal of this article is to introduce a process of using free tools that entry-level analysts can use to collect data.
How to Build a Custom Malware Analysis Sandbox
Why do you need a malware sandbox? Learn How to Build a Custom Malware Analysis Sandbox
IT threat evolution Q2 2021
Targeted attacks and zero-day vulnerabilities, ransomware and banking Trojans – check out our review of Q2 2021
A lookback under the TA410 umbrella: Its cyberespionage TTPs and activity
ESET research reveals a detailed profile of TA410, a cyberespionage umbrella group that we believe consists of three different teams using different toolsets.
How to use Ghidra for malware analysis, reverse-engineering
Follow these steps to get started with Ghidra malware analysis and reverse-engineering using the open source tool from the NSA.

![A Practical Approach To Malware Analysis, Hunting And Memory Forensics [HITB2021AMS Virtual]](https://sectrain.hitb.org/wp-content/uploads/sites/5/2020/10/Speaker-photo-15-2048x2048.png)