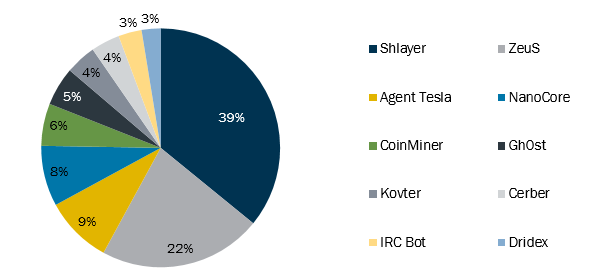
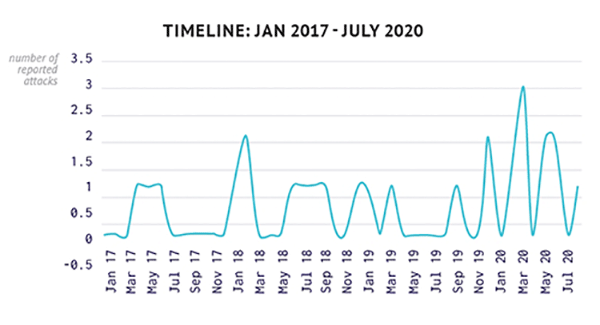
#Cybersecurity #Cyberattack #research
Secunia, Computer insecurity, Security, Computer security, Information security, Risk
Data Center Infrastructure Management (DCIM) Software: Prime Cyberattack Target?
Many organizations are prone to cyberattacks across their DCIM (Data Center Infrastructure Management) software, according to Cyble research.
Data Center Infrastructure Management (DCIM) Software: Prime Cyberattack Target?
Many organizations are prone to cyberattacks across their DCIM (Data Center Infrastructure Management) software, according to Cyble research.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Threats & Attacks
Please click on:
Subscribe to Cybersecurity - Threats & Attacks
Over 20,000 data center management systems exposed to hackers
Researchers have found over 20,000 instances of publicly exposed data center infrastructure management (DCIM) software that monitor devices, HVAC control systems, and power distribution ...
Week in review: Pentagon data breach, cybersecurity workforce gap, who gets spear phished?
Here's an overview of some of last week's most interesting news and articles: Who gets spear phished, and why? Spear phishing is one of the most
For the Average Hacker, Your Small Business Is an Ideal Target
You're not too big to be hacked. Here's how to avoid becoming a statistic.
Endpoint Security
Endpoint security refers to the strategies and technologies for preventing, containing, mitigating, and remediating threats to endpoints. In this glossary post, we will explore endpoint ...
Data Privacy Day: 10 experts give advice for protecting your business
Data Privacy Day is dedicated to achieving sound privacy practices to protect businesses and customers. Learn insights from 10 experts in the field to help safeguard your company.
As Cyber Attacks Become More Prevalent, Here’s Why Your Small Business is at Risk
While many cybersecurity attacks and breaches happen at major enterprise organizations, the reality is cybercriminals don’t discriminate by size and the aftermath of an attack can devastate ...
Cybersecurity in 2022 – A Fresh Look at Some Very Alarming Stats
The past two years has seen a rapid shift of work to remote and hybrid offices. The statistics show that hackers welcomed that shift and took advantage of the vulnerabilities and gaps in ...
What Is Cybersecurity? Definition, Importance, Threats, and Best Practices
Cybersecurity involves the protection of people, devices, processes, and technologies from malicious attacks and unintentional damage. Click here to understand cybersecurity, its ...
The List of Known SolarWinds Breach Victims Grows, as Do Attack Vectors
Concerns mount that SolarWinds may not have been the only IT vendor used to build backdoors into enterprise networks.
Almost three quarters of retailers have been victims of cyberattack
Some 72 percent of retailers globally have experienced a cyberattack, with 61 percent experiencing one in the last year, yet 50 percent don't have a response plan in place to deal with data ...
The Impact of Data Breaches and Cyberattacks on SMB’s and Their Employees
It is critical to focus on the impact of data breaches on SMB's and the importance ofsecuring your employee's data.
Live Webinar: JumpStart Guide for Endpoint Security in AWS
Read the Full Column by Danelle Au Live Webinar: JumpStart Guide for Endpoint Security in AWS Join this webcast and gain practical knowledge on how to evaluate and select an effective ...
Cyber Actors Target K-12 Distance Learning Education to Cause Disruptions and Steal Data
This Joint Cybersecurity Advisory was coauthored by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information ...
PASSWORDS ARE AND HAVE ALWAYS BEEN AN ACHILLES HEEL IN CYBERSECURITY
“I’m afraid people will remain the weakest link in security, and the vast majority of cybercriminals go after this lowest hanging fruit. It’s the least effort for the most reward.”…
How to Secure Your Corporation
This guide is meant to provide a foundation for decision makers and employees on the cybersecurity issues surrounding the platforms we use and the products we make.
How to Stay Safe from Cybersecurity Threats
The National Cyber Security Alliance found that more than 70% of companies that encounter a cyberattack are small businesses.
As COVID-19 vaccine research revs up, so do cyberattacks: report
A new report on the biopharma industry by cybersecurity firm Bluevoyant LLC found that the eight most prominent players in the race for a COVID-19 vaccine faced the highest volume of ...