#infosec #AI #cybersecurity
Computer insecurity, Risk, Security, Phishing, Computer security, Information security
Cybersecurity Threats: Issues And Technology Trends
Analyzing #cybersecurity threat trends including #AI, cross-site scripting attacks, supply chain breaches and more https://t.co/bSYP04SwWu @VerdictUK #infosec https://t.co/36HpqxT1Vz
OpenCybersecurity is vital. As technology develops, from mobile to cloud to the IoT, the level of complexity needed o maintain a cyber-aware stance increases.
Analyzing #cybersecurity threat trends including #AI, cross-site scripting attacks, supply chain breaches and more https://t.co/bSYP04SwWu @VerdictUK #infosec https://t.co/36HpqxT1Vz
OpenCybersecurity Threats: Issues And Technology Trends
Cybersecurity is vital. As technology develops, from mobile to cloud to the IoT, the level of complexity needed o maintain a cyber-aware stance increases.
We are sorry, we could not find the related article
If you are curious about Cybersecurity Essentials and Threats and Attacks
Please click on:
Or signup to our newsletters
2019 Security Predictions
Jon Fielding, Managing Director, EMEA at Apricorn: “Whatever the future holds in term of new and advancing technologies, the questions we need to answer are the same: what are the security ...
DeepLocker: How AI Can Power a Stealthy New Breed of Malware
DeepLocker has changed the game of malware evasion by taking a fundamentally different approach from any other current evasive and targeted malware. Here's what you need to know.
The Coronavirus & Cybersecurity: 3 Areas of Exploitation
Criminal, political, and strategic factors are combining to create a perfect storm of cyber infections that target the global supply chain.
The Ponemon 2019 State of Cybersecurity for SMBs Report
Latest study from Ponemon Institute indicates cyber attacks on SMBs are again on the rise and the new attacks appear to be focusing on SMBs in specific regions, with U.S. getting the worst ...
Cyberattacks and Your Small Business: A Primer for Cybersecurity
Hackers, scammers and other digital malcontents aim to do your SMB harm. With this cybersecurity guide, you can stand as a bulwark against cyberattacks.
Beware of these Application Security Threats!
Understanding the current application security threats and available countermeasures provides users and developers with the much-needed app safety knowledge.
35+ Powerful Cybersecurity Statistics to Know in 2019
Cyberattacks are the fastest growing crime in the United States. Learn more about the importance of guarding your business against cyberattacks with these 35+ cybersecurity statistics!
Week in review: Pentagon data breach, cybersecurity workforce gap, who gets spear phished?
Here's an overview of some of last week's most interesting news and articles: Who gets spear phished, and why? Spear phishing is one of the most
10 Basic And Easy Cybersecurity Steps
No industry is immune to the growing cost of cybercrime.
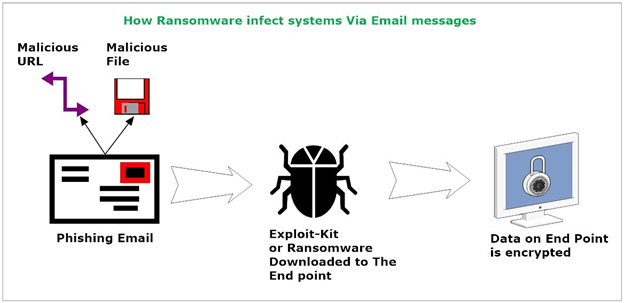
Ransomware: Attack Techniques and Countermeasures
Learn more about ransomware attack techniques and countermeasures with infosec author Nihad Hassan.
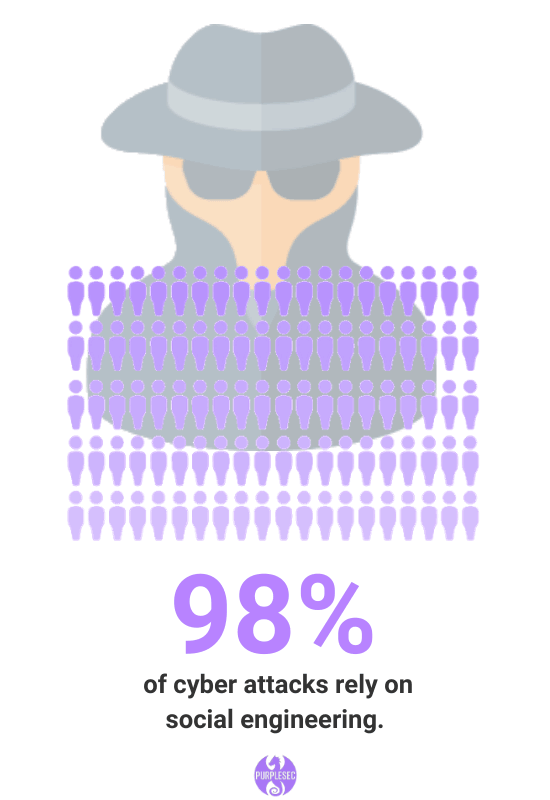
The Ultimate List Of Cyber Security Statistics For 2019
Hundreds of cyber security statistics and metrics including the top network vulnerabilities, social engineering, penetration testing, compliance and more.
These are the courses UK police are set to take in cybersecurity
Is the cybersecurity training due to roll out to thousands of police officers of value? ZDNet finds out.
Where are the weak links in your business’s cybersecurity?
How to find and plug the gaps in your company’s cyber security defences.