Top news of the week: 20.05.2020.
#cybersecurity #SCA #StoryOfTheDay #Passwords #security #COVIDー19 #cyberattacks #IAM #regulation #creativity
Innovations And Trends
https://t.co/uHGnNLqJTx
🆕HACKER NOON TOP STORY >>Ten Underground Tech Masterminds You Probably Haven't Heard Enough About, by Carlo @carloocchiena.
#StoryOfTheDay https://t.co/FlXX09sbtt
OpenTen Underground Tech Masterminds You Probably Haven't Heard Enough About
The history of technology, intended here in a narrow sense as the history of information technology, rests on the shoulders of a small handful of giants.
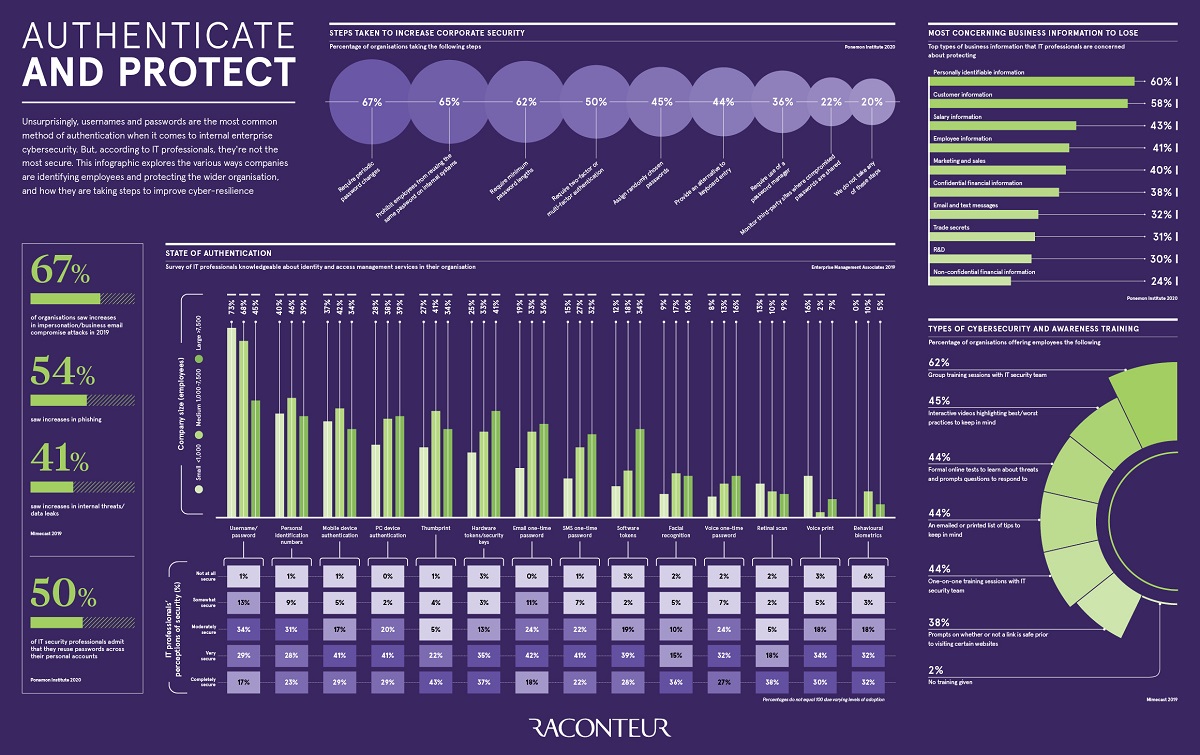
A report by @raconteur explores the various ways companies are identifying employees and protecting the wider organization, and how they are taking steps to improve cyber-resilience. https://t.co/AS8xIkBAtR @antgrasso_IT #IAM #CyberSecurity #Passwords https://t.co/0e48KHMNgg
OpenAuthenticate and Protect
Unsurprisingly, usernames and passwords are the most common method of authentication when it comes to internal enterprise cybersecurity. But, according to IT professionals, …
RT @Hope012015: Law Firm Hackers Claim to Have Dirt on Donald Trump, Up Data Ransom to $42M https://t.co/Yj6YFiuWA3 via @variety
OpenLaw Firm Hackers Claim to Have Dirt on Donald Trump, Up Data Ransom to $42M
UPDATED: The cyber-extortionists who stole a trove of private data from entertainment law firm Grubman Shire Meiselas & Sacks now have a new target in their sights: President Donald Trump. ...
RT @recruiter4u: FBI, DHS warn of China #cyberattacks on US organizations doing coronavirus research #security #cybersecurity #COVIDー19 https://t.co/1I6eeQLuof https://t.co/pjkhFRkAYH
OpenFBI, DHS accuse China of cyberattacks on US organizations doing coronavirus research
The FBI and Department of Homeland Security on Wednesday accused the Chinese government of targeting organizations conducting coronavirus research with cyberattacks, and warned that such ...
CNN: US officially warns China is launching cyberattacks to steal coronavirus research.
https://t.co/ucv8osYwe8
OpenUS officially warns China is launching cyberattacks to steal coronavirus research
The US Department of Homeland Security and the FBI issued a "public service announcement" Wednesday warning that China is likely launching cyberattacks to steal coronavirus data related to ...
Tim Ayling, VP EMEA, buguroo, discusses the potential consequences of delays to payment services #regulation due to the COVID-19 crisis https://t.co/m7hsG134U2 #SCA https://t.co/aS9DB1xmQp
OpenThe effects of coronavirus on SCA implementation
Tim Ayling, VP EMEA, buguroo, discusses the potential consequences of delays to payment services regulation due to the COVID-19 crisis Changes in consumer behaviour have been …
RT @HeartInternet: Is #creativity at the heart of #cybersecurity? @ElishevaMarcus chats with @KVoellmer, founder of @DeflectSecurity https://t.co/Vv2654mhNj via @hackernoon https://t.co/6QxDZyDhNe
OpenCreativity is the Heart of Cybersecurity
Insights from a Q&A with Deflect’s Founder, Kevin Voellmer
Each approach to Innovation strikes a different balance between disruptive and non-disruptive creation to achieve growth. Link >> https://t.co/D41pMfbJfA @mitsmr via @antgrasso #Innovation #CEO #CIO #Strategy https://t.co/RgdjP8txZa
OpenNondisruptive Creation: Rethinking Innovation and Growth
It’s time to embrace the idea that companies can create without destroying.