Top news of the week: 12.01.2022.
Innovations And Trends
iProov Announces $70M Investment from Sumeru Equity Partners
iProov, the world leader in online biometric face authentication, today announced a $70 million growth investment from Sumeru Equity Partners
Your Guide to Cybersecurity Frameworks
There are three main categories of security frameworks: Control Frameworks, Program Frameworks, and Risk Frameworks. Here we explore their differences.
What is the “Living off the Land”(LotL) Attack Tactic in Cybersecurity?
Picture a mouse that enters a house when the door is left open.
3 Outside-the-box Questions to Ask During a Cybersecurity Interview
When interviewing, I initially used the popular lists you find via Google. This led to asking questions that candidates that made selection even more difficult.
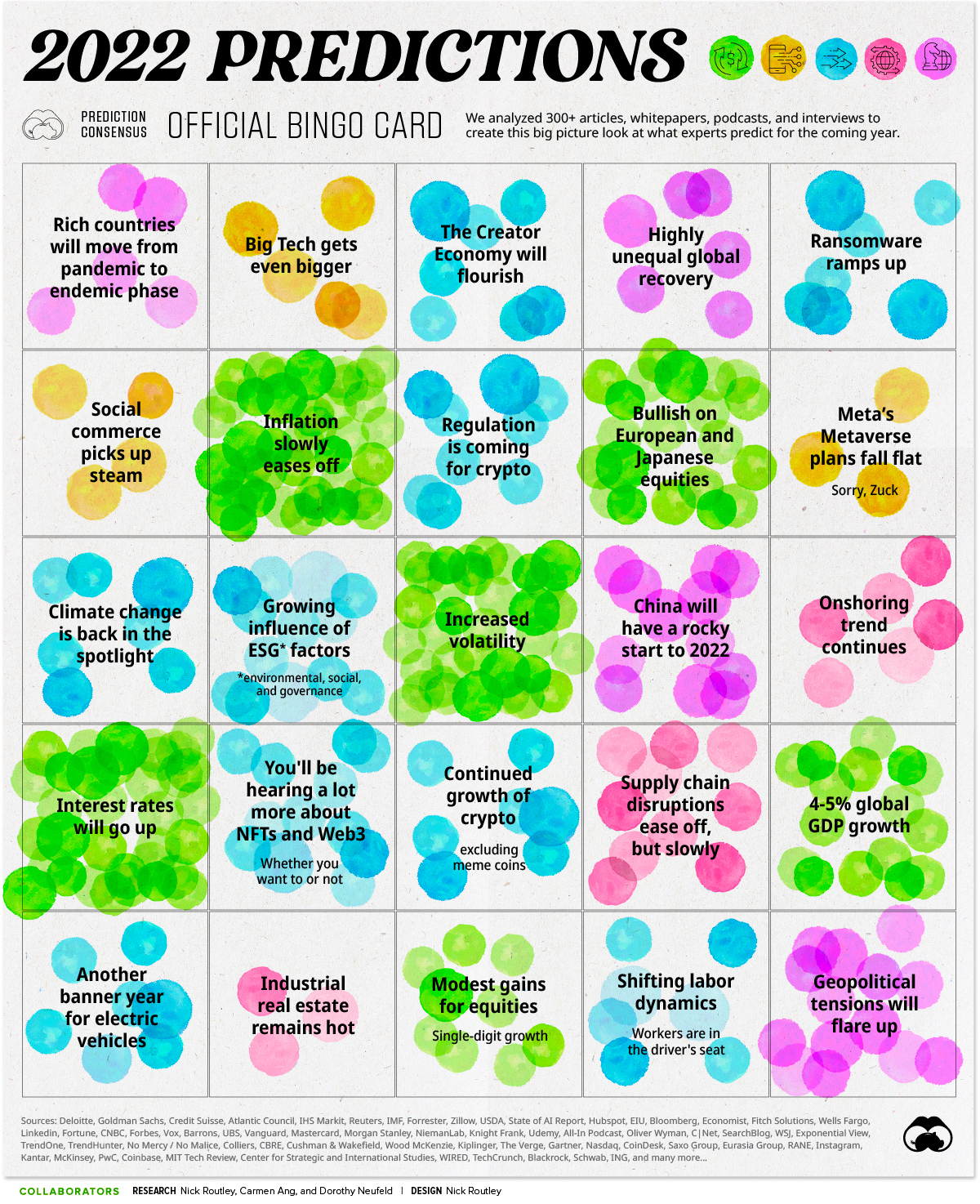
Prediction Consensus: What the Experts See Coming in 2022
We analyzed 300+ articles, reports, and interviews to answer the question: is there any consensus on 2022 predictions? Here are the results.
Ransomware warning: Cyber criminals are mailing out USB drives that install malware
Don't insert USB drives from unknown sources, even if they're addressed to you in the post.
Automatically Scan Your Project Dependencies for Vulnerabilities Using Docker, Jenkins (Part 1/2)
Find out how to automatically check your software projects for potential vulnerabilities caused by 3rd party code.
Who Should the CISO Report to?
Should the CEO be the sole decision-maker for a CISO's plans?