Top news of the week: 29.05.2020.
#ransomware #data #consumer #ZeroTrust #cybercrime #infosec #strategy #MITRE #SecOps #datasecurity
Mitre Attack
Former Salesforce Execs Launch Data Protection Startup
Cloud-based API service stores and manages sensitive consumer data with a zero-trust, database-as-a service approach.
Say you’ve been hit with #ransomware and you’re weighing your options – here’s what you should do if you decide to pay the ransom, with thoughts from our @Mandiant SVP and Strategic Services CTO, Charles Carmakal. via @DarkReading https://t.co/wHMA6C9wW0
OpenHow to Pay a Ransom: A Step-By-Step Guide for Something You'd Never Do
Even prior to the COVID-19 pandemic, ransomware attacks were on the rise and becoming more expensive. Now your, um, friend's organization has fallen victim and is going to pay. Here's how ...
@wendyck @wendyck I guess judges may interpret legal privilege differently https://t.co/sH4lAh2fcA
OpenJudge rules Capital One must hand over Mandiant's forensic data breach report
A court has ruled that Capital One must allow plaintiffs to review a cybersecurity firm’s forensic report related the bank's 2019 data breach.
Securing the open source supply chain is an enormous task. Supply chain security is about the integrity of the entire software development and delivery ecosystem. In the past few years the open source supply chain experienced a variety of attacks. Read on! https://t.co/nue2NDyQyK
OpenThe Octopus Scanner Malware: Attacking the open source supply chain
This post details how an open source supply chain malware spread through build artifacts. 26 open source projects were backdoored by this malware and were actively serving backdoored code.
Download the Five Clear Steps to Enhance SecOps with #MITRE ATT&CK guide, and learn the process that empowers #SecOps to improve iteratively over time by leveraging their existing talent and tools. https://t.co/w7IBQpPAnD
OpenFive Clear steps to enhance secops with MITRE ATT&CK™
This white paper establishes a process that empowers SecOps to improve iteratively over time by leveraging their existing talent and tools.
Security & Trust Ratings Proliferate: Is That a Good Thing? https://t.co/Pw95l1AiKl by @roblemos #phishing #trust #ratings
OpenSecurity & Trust Ratings Proliferate: Is That a Good Thing?
Phishing ratings, security ratings, human-ness ratings -- we are looking at a future filled with grades of security and trustworthiness. But there is a downside.
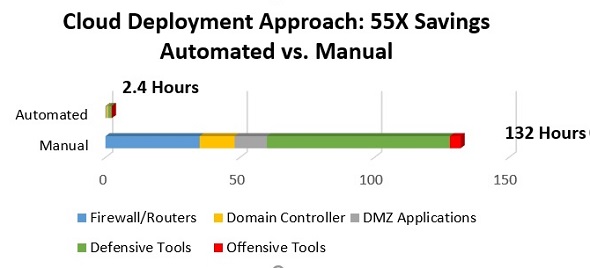
Benefits of a Cloud-Based, Automated Cyber Range https://t.co/oHnTr6qbjU by Rocky Yuan, Cybersecurity Engineer @BAESystemsInc
#cloud #automation #riskmanagement #ITsecurity
OpenBenefits of a Cloud-Based, Automated Cyber Range
A cyber range is an irreplaceable tool that allows cybersecurity professionals to improve their response capabilities as well as their ability to identify risks.
Standing Privilege: The Attacker's Advantage https://t.co/lkxydacQy0 by @tkeeler, founder and CEO @Remediant #cyberattack #credentials #datasecurity
OpenStanding Privilege: The Attacker's Advantage
The credential is a commodity and will continue to be breached. As a result, focus and spending must shift toward the access that the credentials provide.