Top news of the week: 25.09.2020.
#incidentresponse #stuffing #credential #deception #vuln #Google #GoogleCloud #data #threatintel #MSIgnite
Mitre Attack
Attackers Target Small Manufacturing Firms https://t.co/q43M2FMUKX ring Firms by @roblemos #credential #stuffing #vuln #deception
OpenAttackers Target Small Manufacturing Firms
The most common tactics include credential stuffing using valid accounts, various forms of deception, and vulnerabilities in third-party software, Rapid7 says in its latest quarterly threat ...
Google Cloud Debuts Threat-Detection Service
Lockdown economics are driving a threat-intelligence business boom. Chronicle Detect is Google's answer to monitoring so much log data created by the distributed workforce.
Threat actors could maintain their anonymity by using publicly available tools instead of custom malware.
Listen to our newest 'Eye on Security' episode to hear more observations from our #incidentresponse investigations: https://t.co/TRTSYa1oCD https://t.co/WvKTbPnDzq
OpenRansomware and Observations from Recent IR Investigations
One of our leading incident response experts, Charles Carmakal, joins us on this podcast to talk about ransomware and other threat impacting organizations today.
New Snort, ClamAV coverage strikes back against Cobalt Strike https://t.co/jl4hfFr6lS < good read
OpenNew Snort, ClamAV coverage strikes back against Cobalt Strike
A blog from the world class Intelligence Group, Talos, Cisco's Intelligence Group
RT @old_Red_f0x: While brushing up on my knowledge of ATT&CK I came across a blog post from @redcanaryco about using ATT&CK for threat hunting. Now on my Thursday reading list.https://t.co/nGe68cxi2P
OpenHow to use MITRE ATT&CK to mature your threat hunting program
Watch this on-demand webinar featuring experts from Red Canary, Carbon Black, and MITRE to learn how to mature your threat hunting program with ATT&CK.
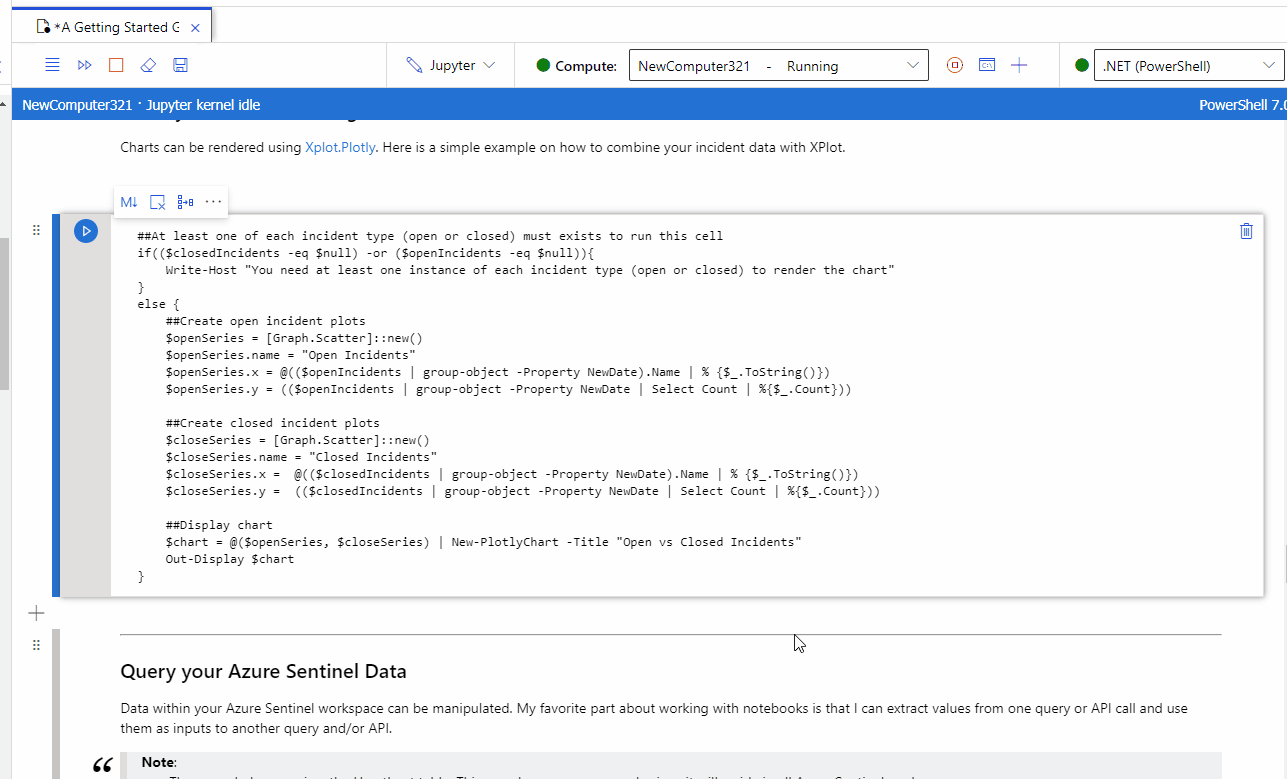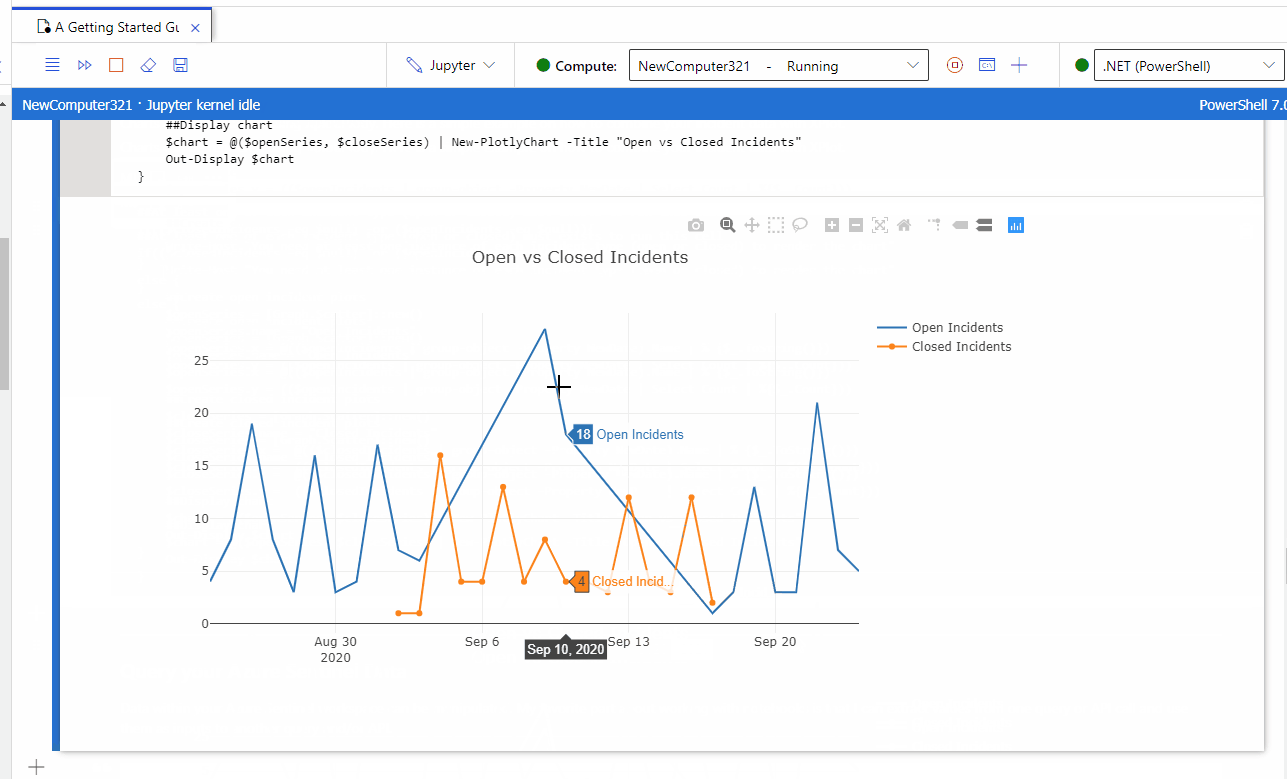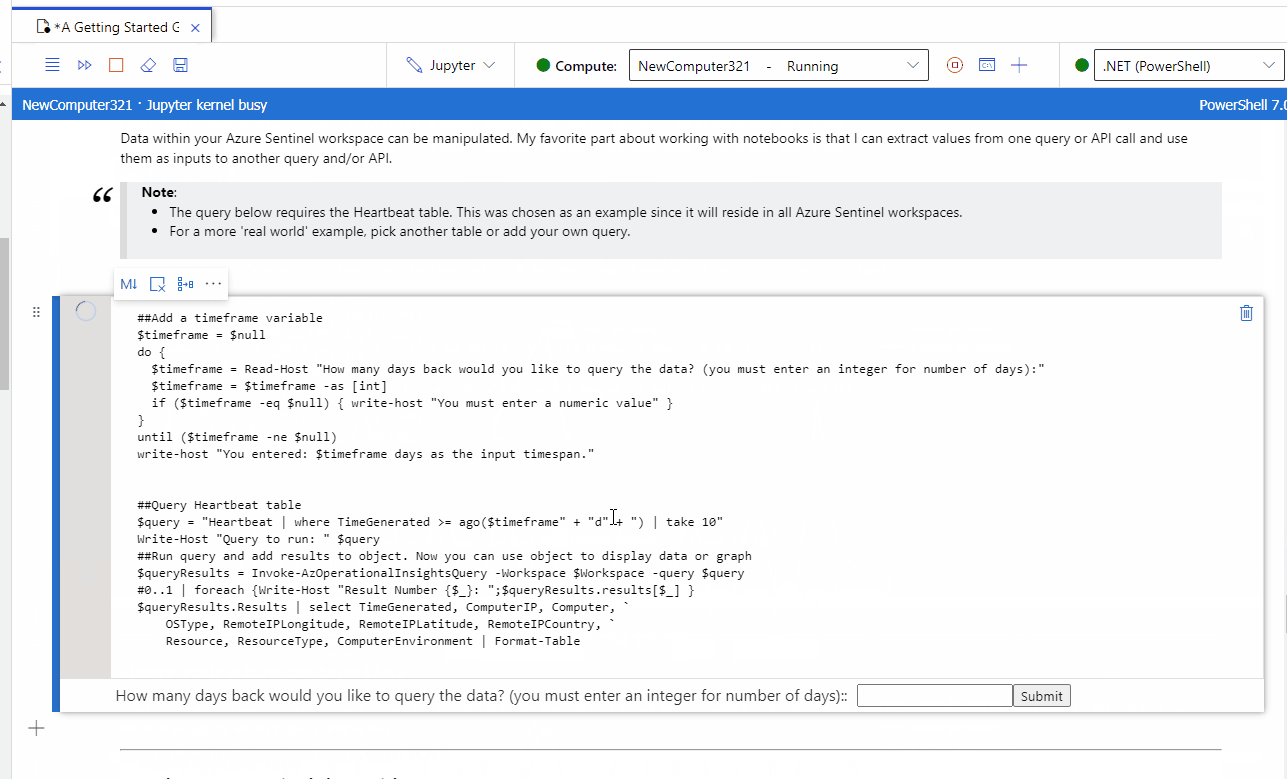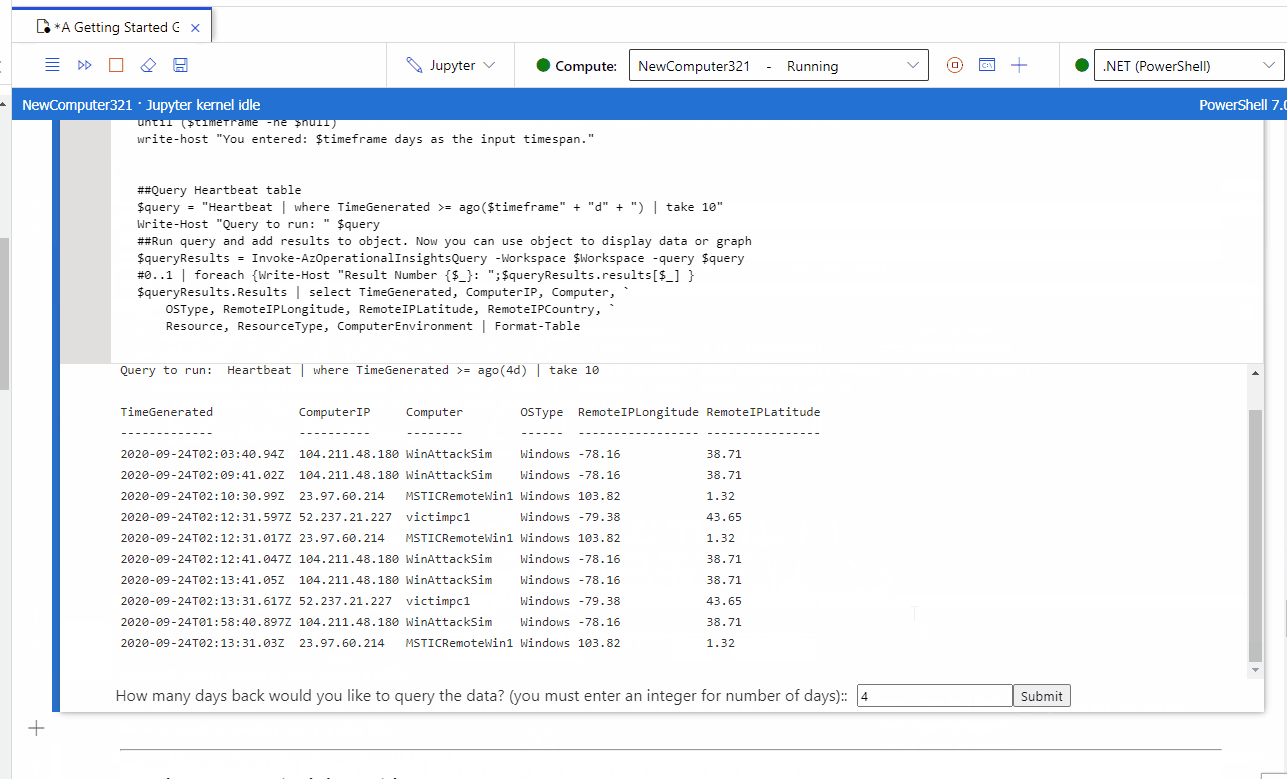
RT @jsnover: If you watched my #MSIgnite sessions, you know how WILDLY optimistic I am about Jupyter notebooks.
Here is a great example of the sort of thing I'm excited about.
https://t.co/5ukiyEiMzr
OpenPowerShell+Azure Sentinel notebooks to supercharge your threat hunting and investigations!
For those interested in security and security analytics, we recently published an article on how you can now enable PowerShell Jupyter notebooks via .Net Interactive Public Preview for use ...
FERC, NERC Conduct Study on Cyber Incident Response at Electric Utilities https://t.co/hnJGNLmwDC
OpenFERC, NERC Conduct Study on Cyber Incident Response at Electric Utilities
U.S. FERC and NERC release a report outlining cyber incident response and recovery best practices for electric utilities
"Tools such as Mimikatz, a legitimate authentication and credentials management system, come in third place -- as weaponized software turned toward credential stuffing attacks." ?!?
Who is doing PR for Mimikatz? They deserve a raise.
CC @campuscodi
https://t.co/x5MDQPLStj https://t.co/pSSqyJjlQW
OpenCode execution, defense evasion are top tactics used in critical attacks against corporate endpoints
Cisco examines MITRE ATT&CK data to suggest the threat vectors enterprise security staff should focus their efforts on.