Top news of the week: 23.02.2021.
Mitre Attack
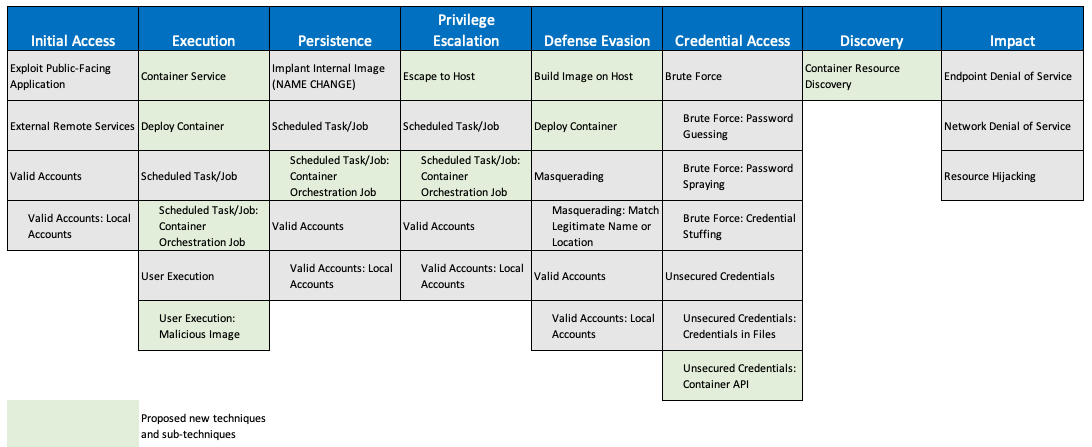
Update: Help Shape ATT&CK for Containers
Last December, we sent out a call to the community to help us shape ATT&CK for Containers as part of a Center for Threat-Informed Defense…
AppleJeus: Analysis of North Korea’s Cryptocurrency Malware
This Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques.
Mysterious Mac Malware Infected at Least 30,000 Devices Worldwide
Researchers uncover a new Mac malware that has infected at least 30,000 devices and which appears to be the first malware to abuse the macOS Installer JavaScript API.
How to select a DLP solution: 9 unusual considerations
Data loss prevention systems have become more complex, and each has evolved differently. Here’s how to select a DLP system based on required functionality and its real-life ability to ...
Chinese Hackers Cloned Equation Group Exploit Years Before Shadow Brokers Leak
APT31 managed to capture and clone the Equation Group’s exploit for CVE-2017-0005 three years before Shadow Brokers’ “Lost in Translation” leak.
New York issues cyber insurance framework as ransomware, SolarWinds costs mount
The state looks to protect one of its core industries, which is threatened by mounting and potentially "unsustainable" losses due to the SolarWinds and ransomware attacks.
HBCU Engineering Programs Use MITRE ATT&CK to Boost Cyber Defense Curriculum
MITRE’s partnership with Advancing Minorities’ Interest in Engineering (AMIE) is bringing the MITRE ATT&CK® cyber defense framework to Historically Black Colleges and Universities (HBCUs). ...
Enter The Hunt: Practical, Hands-On Threat Hunting For Everyone
Ever wondered what threat hunting is actually like and how it’s done? Assume at least some security controls implemented in the organization have failed at least once, allowing a …