Top news of the week: 22.07.2021.
Mitre Attack
Critical Cloudflare CDN flaw allowed compromise of 12% of all sites
Cloudflare has fixed a critical vulnerability in its free and open-source CDNJS potentially impacting 12.7% of all websites on the internet. CDNJS serves millions of websites with over ...
The United States, Joined by Allies and Partners, Attributes Malicious Cyber Activity and Irresponsible State Behavior to the People’s Republic of China
The United States has long been concerned about the People’s Republic of China’s (PRC) irresponsible and destabilizing behavior in cyberspace. Today, the United States and our allies and ...
Everything Cybereason at the Black Hat 2021 Virtual Conference
Cybereason invites you join us at Black Hat 2021 on August 4th/5th - sessions with our SMEs will cover advanced RansomOps, how XDR leverages Indicators of Behavior to detect and remediate ...
MITRE Engenuity ATT&CK® Evaluations for ICS: Retrospective & Results
The MITRE Engenuity ATT&CK® Evaluations for Industrial Control Systems (ICS) is the first evaluation of the ICS threat detection market and simulates an attack against an operational ...
Ransomware resurgence: is your organisation prepared?
Ransomware is becoming an even greater problem. But organisations can defend against it
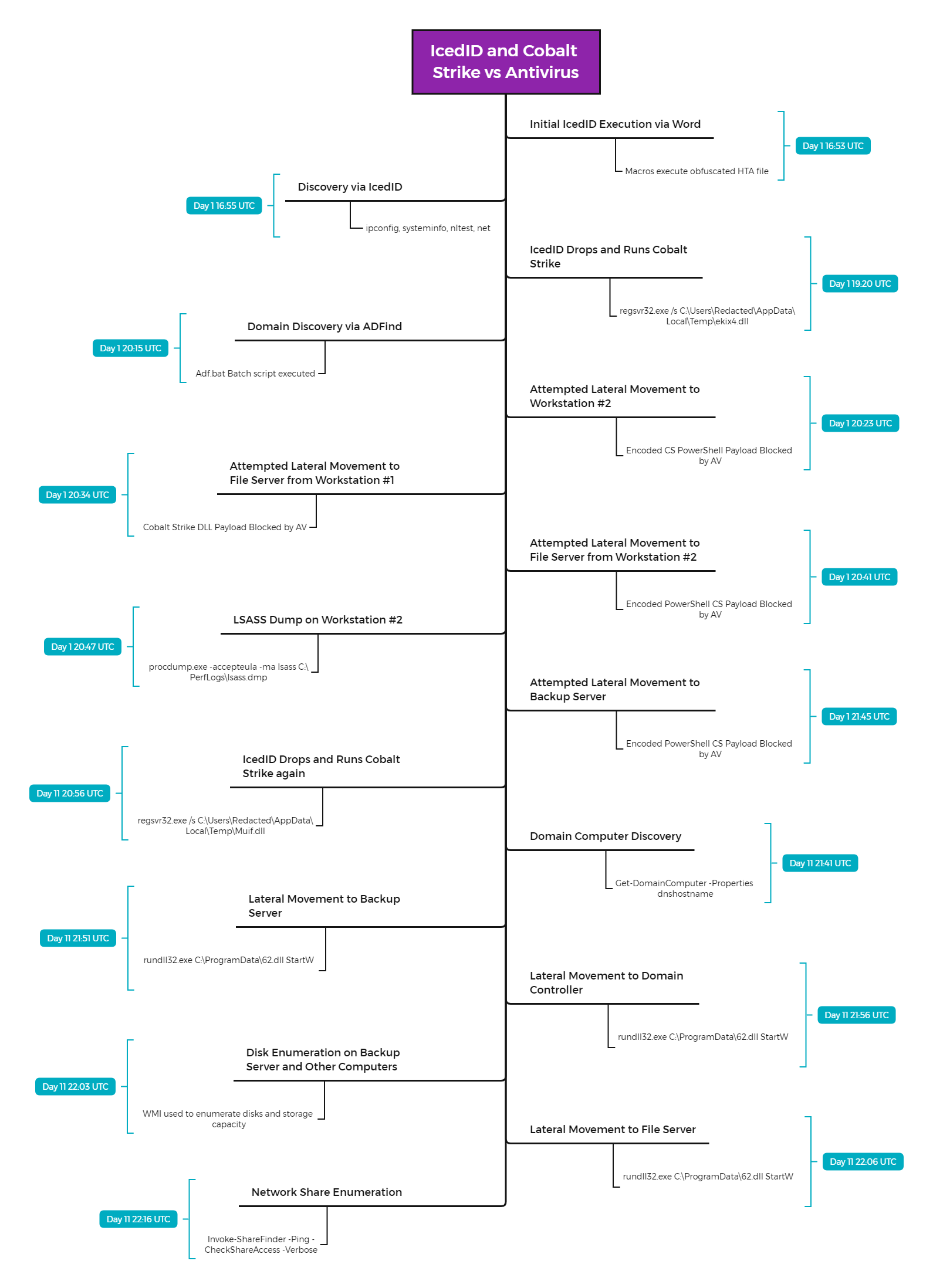
IcedID and Cobalt Strike vs Antivirus
In June, we saw another threat actor utilize IcedID to download Cobalt Strike (CS), which was used to pivot to other systems in the environment. Similar to the Sodinokibi case, anti-virus ...
Visibility in Incident Response: Don’t Chase Ghosts in Your IT Estate
By chasing down ghost systems and ensuring they are protected assets on your network, you'll dramatically improve your response to cybersecurity incidents.