Top news of the week: 17.07.2020.
#ThreatHunting #GRIMMCon #cybersecurity #incidentresponse #BHUSA #cyberattack #securitythreat #vulnerabilities #IANSLA
Mitre Attack
RT @fierytermite: I wrote a piece about how @33root and I started with #ThreatHunting using @redcanaryco Atomic Red Team, both in English (https://t.co/QRCeeU8y96) and Spanish (https://t.co/Eu8pFWflih)!
I hope it helps anyone wanting to give their first steps as a threat hunter!😊
OpenAtomic Hunting with Atomic Red Team: Starting Your Threat Hunting Journey
By Valentina Palacin
RT @ChloeMessdaghi: Does it feel like no matter how much sleep you get, it's never enough? Does it feel like you can easily get angry, frustrated, or sad? Does it take hours or days to respond to an email? Then check out my burnout talk at #GRIMMcon this Wednesday!
Details: https://t.co/nWZAlHrK00 https://t.co/VUqrpyhaCK
OpenA Paramedic's Lessons for Cybersecurity Pros
A paramedic turned cybersecurity expert shares his experiences in both fields, highlights their similarities, and explains how they can learn from each other.
Major Flaws Open the Edge to Attack https://t.co/nRsPGgE1tW by @roblemos #vulnerabilities #cyberattack #securitythreat
OpenMajor Flaws Open the Edge to Attack
Attackers are using critical exploits for flaws in VPN appliances, app-delivery services, and other network-edge hardware and software to punch through corporate perimeters. What can ...
RT @IANS_Security: Join us on Tues 8/11 with Faculty member @HackingDave for the #IANSLA Virtual Symposium "Effectively Leveraging @MITREattack" -- More info and registration: https://t.co/x0uR9dR6vl
Open2020 Los Angeles Virtual Symposium
IANS has run multiple workshops on threat hunting, purple teaming and tool selection, but MITRE ATT&CK has opened up a new range of possibilities for how to approach these areas.
RT @professorbike: ~409 Windows security events mapped to audit policies and monitoring recommendations. cc: @christophetd @Cyb3rWard0g @SBousseaden @olafhartong
https://t.co/q9EGs9zkw6
OpenMapping Windows Event IDs, Policies, and Monitoring Recommendations
I attempted to map Windows Security Event IDs to their audit polices, Microsoft recommendations, and other third-party forwarding guidance. Mitre ATT&CK, event volume, and event ...
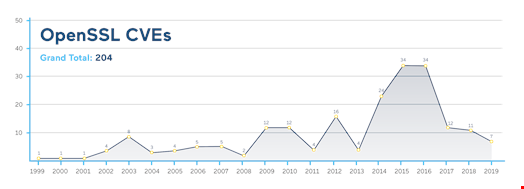
Patching OpenSSL and GNU C Libraries Without Service Restarts
Organizations in all industries must ensure they are promptly mitigating vulnerabilities to prevent exploitation
In the first half of 2020, Falcon OverWatch tracked more intrusions than in all of 2019. This blog takes a deep dive into the types of targeted intrusions being observed in the manufacturing industry. https://t.co/xcewgWYwTI #cybersecurity https://t.co/4H7TuzsiZH
OpenManufacturing Industry in the Adversaries’ Crosshairs
Attacks against the manufacturing industry in the first half of 2020 tripled what we saw last year. Follow along as we break down the types of threats observed.