Top news of the week: 15.12.2022.
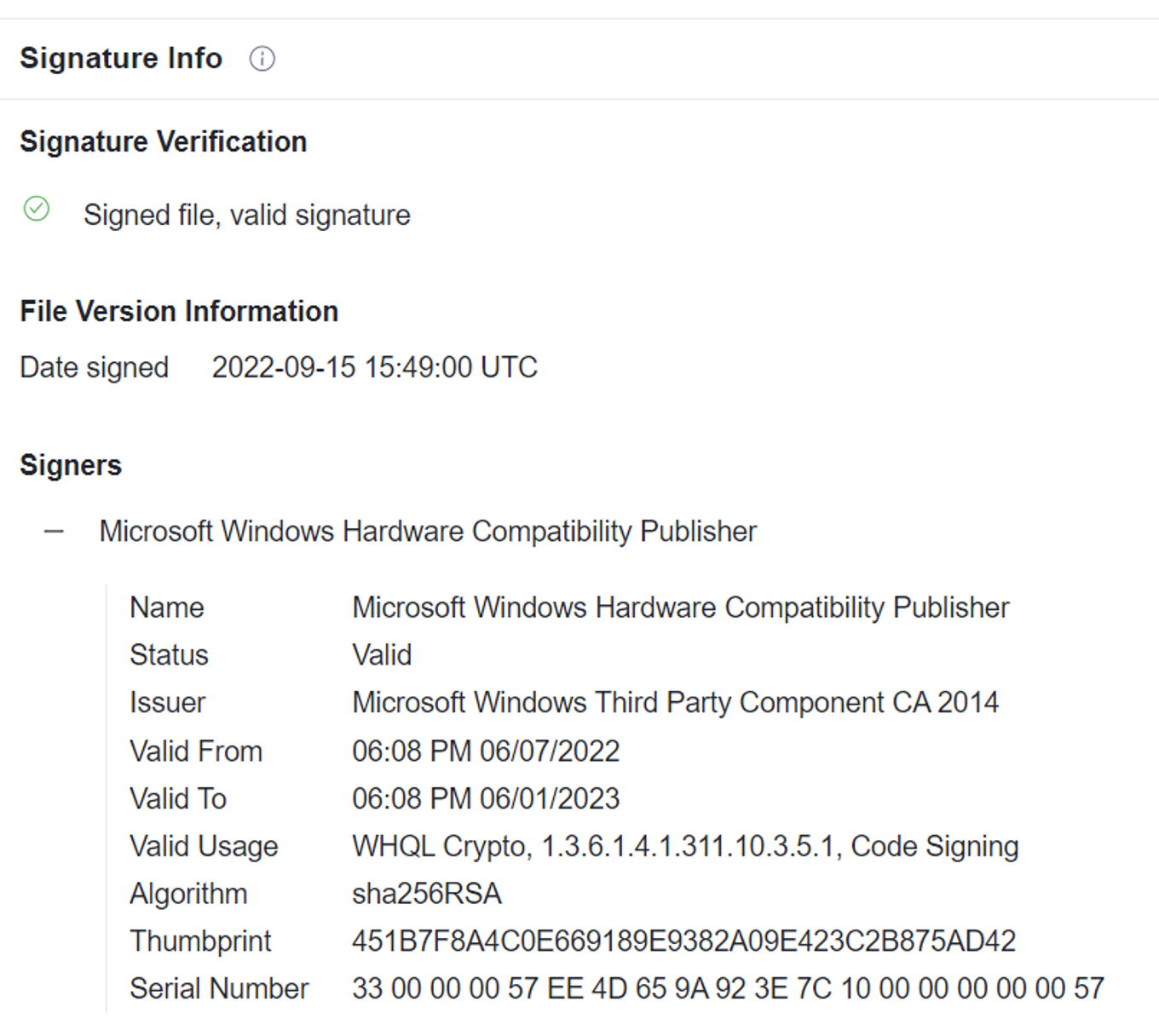
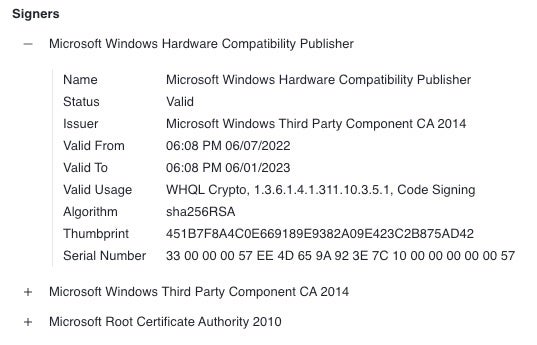
I Solemnly Swear My Driver Is Up to No Good: Hunting for Attestation Signed Malware
Certificate Subject Common Name 2022-06-02 10:09:08 20220811 13:27:00 10f3679384a03cb487bda9621ceb5f90 Zhuhai liancheng Technology Co., Ltd. 2022-06-02 10:09:08 …
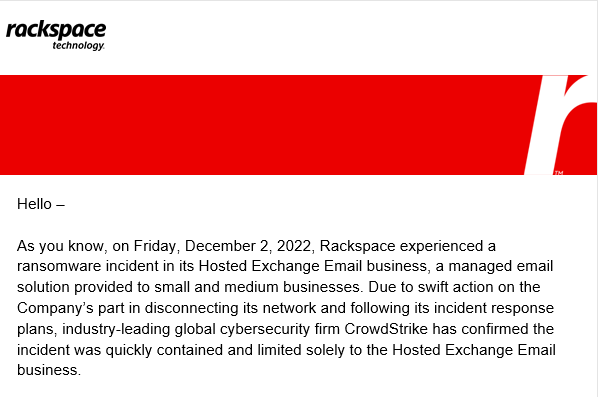
Amid Outrage, Rackspace Sends Users Email Touting Its Incident Response
More than 10 days after a ransomware attack, affected Rackspace customers are being told the incident had a "limited impact," and have been invited to a webinar for additional details.
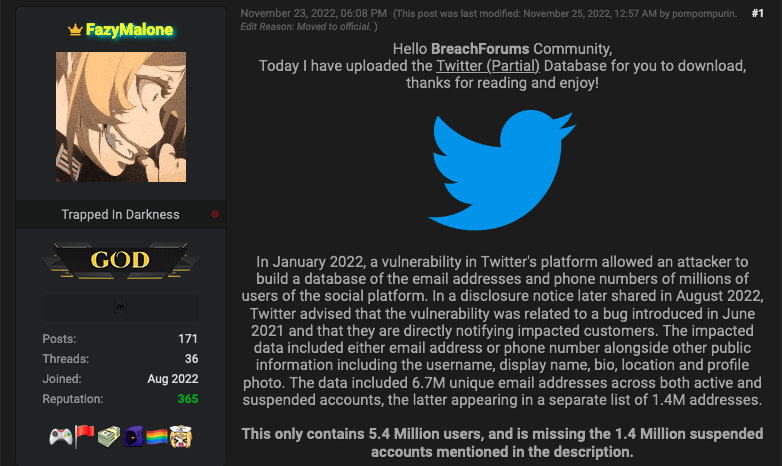
Twitter Responds to Recent Data Leak Reports
Twitter has responded to recent data leak reports, confirming that the exposed information is the same as the one leaked earlier this year.
Government to Fund Security Studies for Hundreds of Students
Latest move shows need to nurture skills pipeline
Driving Through Defenses | Targeted Attacks Leverage Signed Malicious Microsoft Drivers
Threat actors are abusing legitimately signed Microsoft drivers in active intrusions into telecommunication, BPO, MSSP, and financial services businesses.
Iranian APT Targets US With Drokbk Spyware via GitHub
The custom malware used by the state-backed Iranian threat group Drokbk has so far flown under the radar by using GitHub as a "dead-drop resolver" to more easily evade detection.
Why Managed Threat Hunting Should Top Every CISO’s Holiday Wish List
This blog examines the value an organization can derive from effective threat hunting operations. Read to learn more!
Breaking the silence - Recent Truebot activity
Since August 2022, we have seen an increase in infections of Truebot (aka Silence.Downloader) malware. Truebot was first identified in 2017 and researchers have linked it to a threat actor ...