Top news of the week: 15.09.2022.
How Katie Nickels helped transform how we talk about cyber defense
Nickels possesses "superpowers" when it comes to explaining complex subjects in cybersecurity, according to members of the security community.
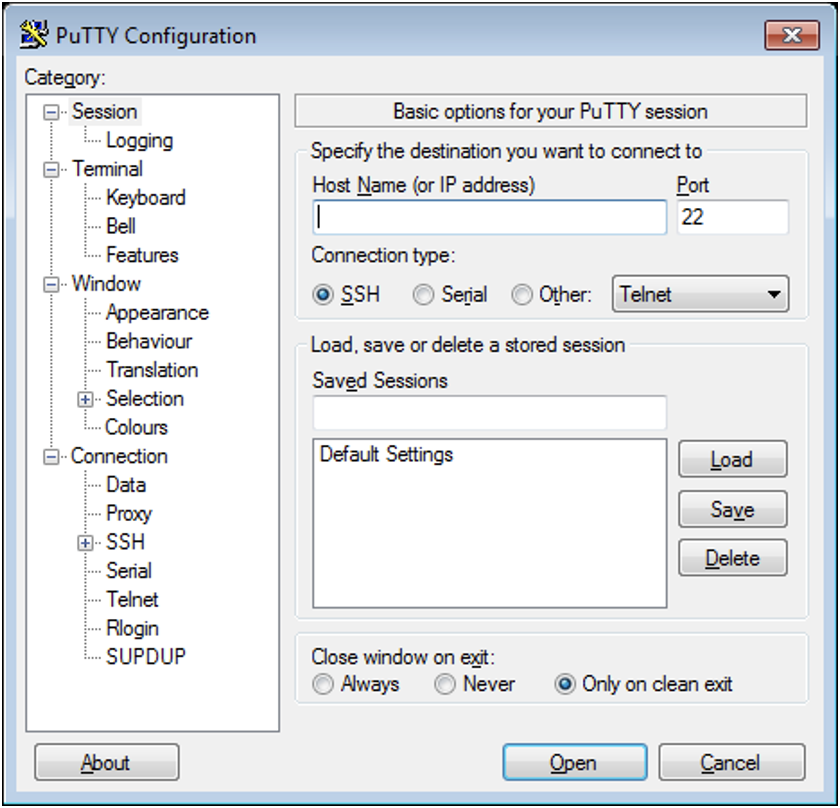
It's Time to PuTTY! DPRK Job Opportunity Phishing via WhatsApp
The Managed Defense Threat Hunting Mindset One of the cornerstones of the Mandiant Managed Defense service offering is its proactive threat hunting program that protects our …
Google Completes Acquisition of Mandiant
5 mins read MOUNTAIN VIEW, Calif. and RESTON, Va. (September 12, 2022)—Google LLC today announced the completion of its acquisition of Mandiant, Inc. (NASDAQ: MNDT), a recognized …
Google Completes Mandiant Acquisition To ‘Reinvent Security’
Google acquires Mandiant for a $5.4 billion cybersecurity buy to significantly boost its security around threat intelligence and cyber attacks, says CEOs Thomas Kurian and Kevin Mandia.
North Korean state-sponsored hacker group Lazarus adds new RAT to its malware toolset
Lazarus has used the new remote access Trojan in campaigns that exploit the Log4Shell vulnerability and target energy companies.
2022 Falcon OverWatch Threat Hunting Report
In this report, the CrowdStrike's threat hunting team provides an exclusive look into the adversary tradecraft and tooling they observed this year.
Restoring a software and services provider’s cloud environment after a breach
A threat actor brought a software and services provider’s business to a halt by locking it out of its network and deleting its entire cloud environment, including email. That’s when the ...
How Your Team’s Culture Determines the Value of Your Tabletop Exercise
TrustedSec's blog is an expert source of information on information security trends and best practices for strategic risk management.