Top news of the week: 15.01.2021.
Mitre Attack
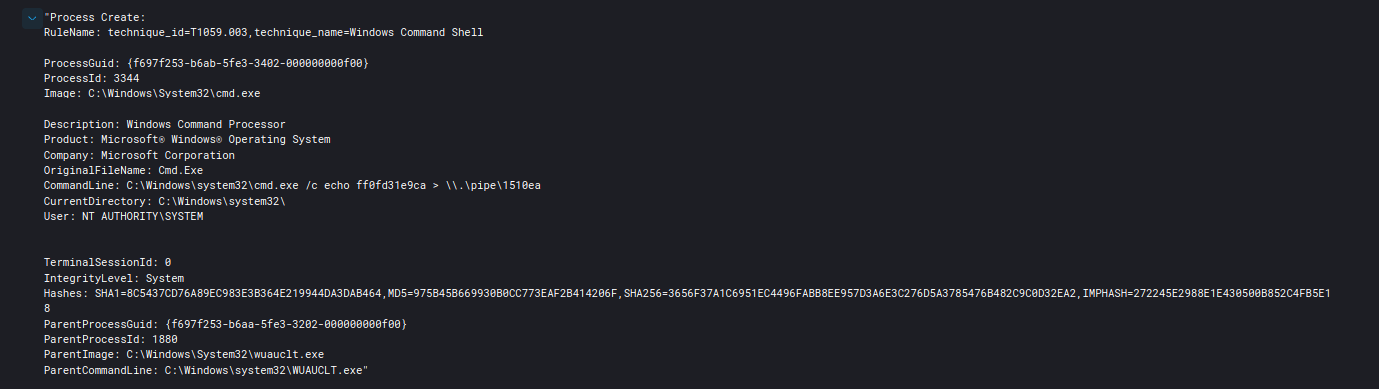
Trickbot Still Alive and Well
The Trickbot threat actors used Cobalt Strike to pivot through-out the domain, dumping lsass and ntds.dit as they went. They used tools such as AdFind, Nltest, Net, Bloodhound, and ...
SUNSPOT: An Implant in the Build Process
In this blog, we offer a technical analysis of SUNSPOT, malware that was deployed into the build environment to inject this backdoor into the SolarWinds Orion platform.
CISA: Hackers bypassed MFA to access cloud service accounts
The US Cybersecurity and Infrastructure Security Agency (CISA) said today that threat actors bypassed multi-factor authentication (MFA) authentication protocols to compromise cloud service ...
Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks
Following the recent attack on the U.S. Capitol, where a parade of people stormed the building and gained access to unprotected computers, industry professionals share thoughts on what they ...
CISA Warns Organizations About Attacks on Cloud Services
The agency says poor cyber hygiene practices lead to compromise via cloud services.
Kaspersky Connects SolarWinds Attack Code to Known Russian APT Group
Researchers have found some similarities between the Sunburst malware used in the SolarWinds attack and Kazuar, a backdoor attributed to the Russia-linked cyber-espionage group Turla.
Increasing resilience against Solorigate and other sophisticated attacks with Microsoft Defender
This blog is a guide for security administrators using Microsoft 365 Defender and Azure Defender to identify and implement security configuration and posture improvements that harden ...
Translating TTPs into Actionable Countermeasures with Virustotal & MITRE ATT&CK
Ismael Valenzuela (McAfee/SANS) and Vicente Diaz (Threat Intel Strategist at Virustotal)What are the best practices to make TTPs actionable? How can blue te...