Top news of the week: 13.10.2022.
We Can Save Security Teams From Crushing Workloads. Will We?
Today, the processing of mountain-high stacks of alarms is considered "security." That system is failing customers and the cybersecurity workforce.
Paul B.’s Post
This is Paul’s wife Keirsten. He passed away on 9/27/2022 in Brazil. I appreciate your patience as I deal with this sudden tragedy. FAQs: What happened? I… | 141 comments on LinkedIn
3 actions Latin American leaders must take to reduce risk of cyberattacks
Threat actors are targeting government and private sector organizations across Latin America, so business and political leaders must step up to meet the challenge.
Industry Reactions to Conviction of Former Uber CSO Joe Sullivan: Feedback Friday
Industry professionals react to the conviction of former Uber CSO Joe Sullivan over his role in covering up the data breach suffered by the ride sharing giant in 2016.
Proposed SEC Disclosure Rules Could Transform Cyber-Incident Response
It's not too early for firms to start preparing for change.
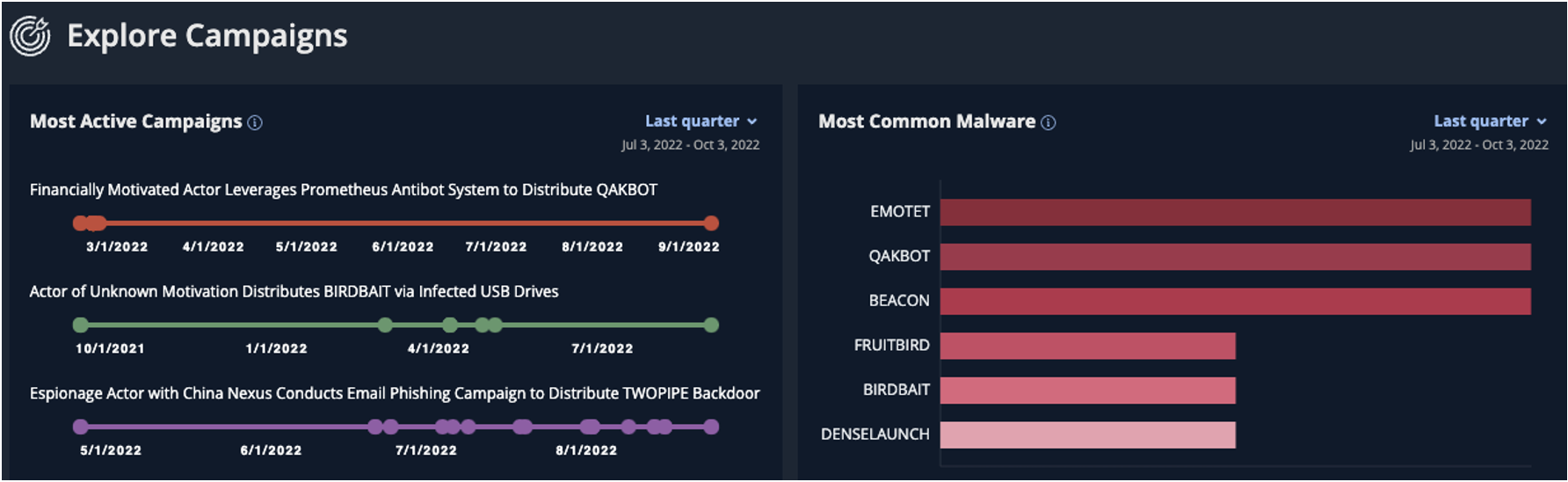
Gain Visibility Into Attacker Activity with Threat Campaigns
Individual and Global Campaigns The addition of Threat Campaigns builds upon the mission of Mandiant Advantage Threat Intelligence: to provide greater visibility into attacker …
Windows Management Instrumentation
Windows Management Instrumentation (WMI) is a technique leveraged for lateral movement and discovery. See detection strategies for T1047.
Gaining 360-Degree SecOps View to Trounce Cyber Threats with Cyber Fusion
Security teams have an uphill battle in today’s threat landscape as they struggle to gain sufficient visibility over their environment while defending a variety of distributed assets.