Top news of the week: 12.06.2020.
#certifications #careers #forensics #businessanalysis #networksecurity #ITcareers #pandemic #cybersecurity #AWS #softwaresecurity
Mitre Attack
RT @craiu: Today we release KTAE, the Kaspersky Threat Attribution Engine. I wrote a small blog describing how this went from an idea to a product: "Looking at big threats using code similarity - part 1": https://t.co/sZvMiFhODI
OpenLooking at Big Threats Using Code Similarity. Part 1
Big Threats Using Code Similarity. Part 1 Today, we are announcing the release of KTAE, the Kaspersky Threat Attribution Engine. This code attribution technology, developed initially for ...
14 IT certifications that will survive and thrive in the pandemic
These tech certifications not only have high value now, but employers will continue to value them as the coronavirus continues.
Red Canary's 2020 Threat Detection Report includes detection strategies for Scheduled Task and other prevalent @MITREattack techniques. https://t.co/WHtj1cjOd3
OpenMITRE ATT&CK® Technique T1053: Scheduled Task - Red Canary
Scheduled Task (MITRE ATT&CK Technique T1053) is a highly prevalent threat, thanks to TrickBot. Here's how to detect malicious use of Windows Task Scheduler and more.
This week's show is up. Tune in to hear me repeatedly tell @Cloudflare to eat a bag of d**ks.
https://t.co/ZfZb3uukZG
OpenRisky Business #587 -- Full scale of Indian hacking-for-hire revealed
Risky Business #587 -- Full scale of Indian hacking-for-hire revealed
On May 26, I told city officials in Florence, Ala. their networks were hacked by a ransomware gang. Thanks, they said. We dodged a bullet. On Jun 5, ransomware was deployed. The city now says it'll pay ~$300k ransom to keep its citizens' data off the Web. https://t.co/xCe5htE0jh https://t.co/dEd05ATRBL
OpenFlorence, Ala. Hit By Ransomware 12 Days After Being Alerted by KrebsOnSecurity
In late May, KrebsOnSecurity alerted numerous officials in Florence, Ala. that their information technology systems had been infiltrated by hackers who specialize in deploying …
🖥 “IT is hammered for uptime and availability, and some of the things that [Security] might want to do impacts that.” Read more insights from top CIOs and CISOs in this commissioned @forrester Consulting Spotlight: https://t.co/dY6nxosgqy https://t.co/wVJvjuGmGM
OpenSecurity As A Team Sport: A Forrester Spotlight On The Growing Role Of IT In Security Tasks
Security and IT teams are aware of the need for increased collaboration to avoid working against themselves. But is this a realistic goal?
This is huge - Capital One will have to hand over their IR report to plaintiffs in a case. I can't imagine the shift this is likely to cause in how reports are written.
https://t.co/GsjQy1solm
OpenHere's what that Capital One court decision means for corporate cybersecurity
When a judge ruled last month that Capital One must provide outsiders with a third-party incident response report detailing the circumstances around the bank’s massive data breach, the ...
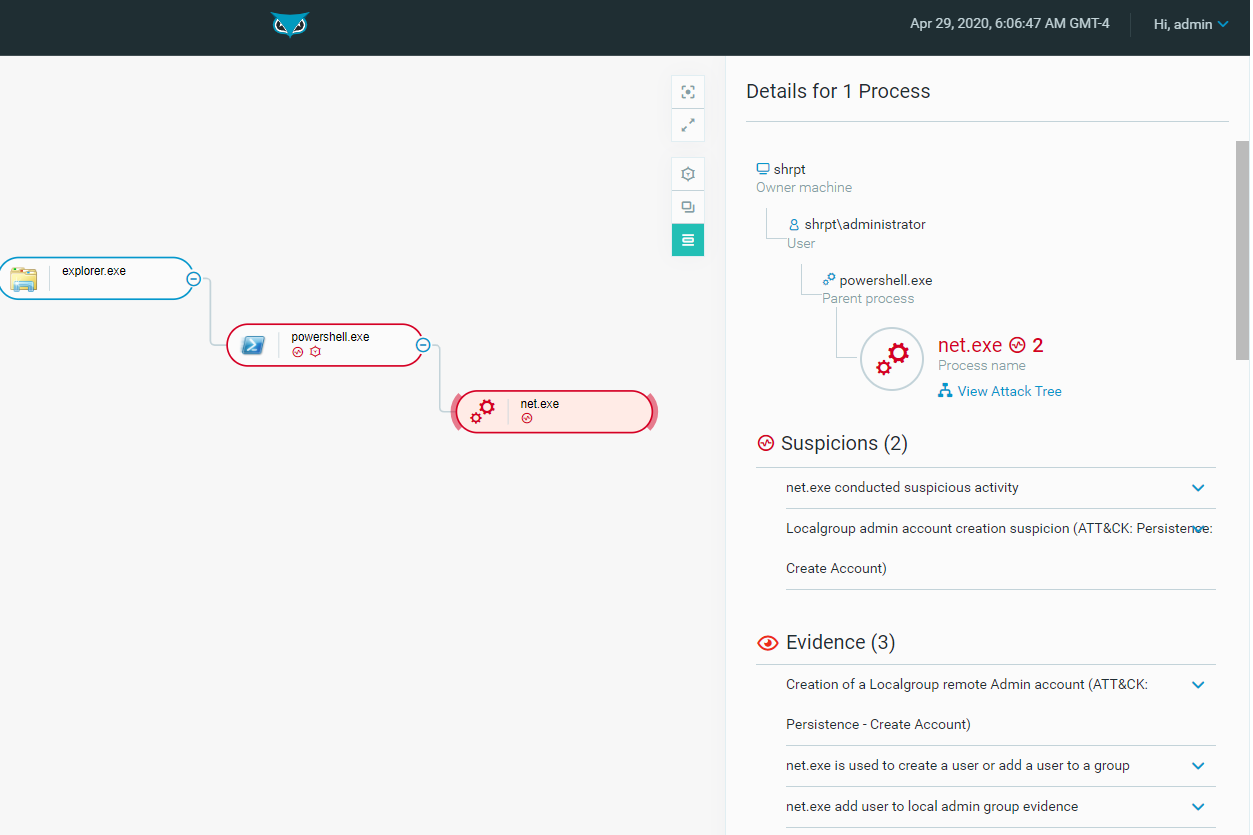
Threat Alert: Multi-Stage #Ransomware. We live in a world of insecurity where hackers have advantage over a majority of enterprises trying to protect computer networks. Learn why Cybereason's newest honeypot have critical infrastructure providers on alert https://t.co/rVWAkJSCh3
OpenCybereason’s Newest Honeypot Shows How Multistage Ransomware Attacks Should Have Critical Infrastructure Providers on High Alert
Earlier this year, Cybereason launched its latest honeypot to analyze the tactics, techniques, and procedures used by state-sponsored groups and cyber crime actors to target critical ...