Top news of the week: 11.09.2020.
Computer security, Vulnerability, Risk, Cloud computing, Need to know, Security police
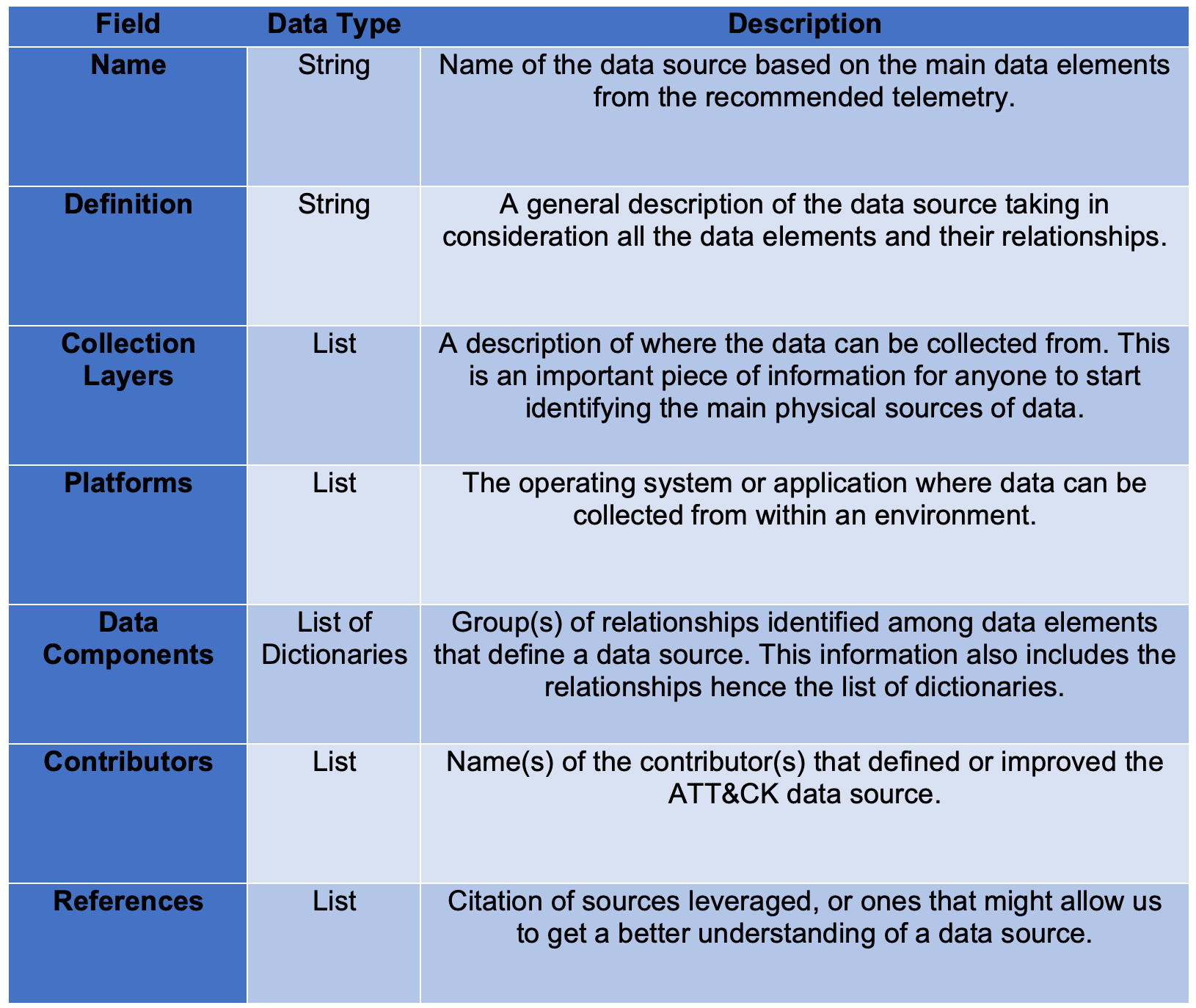
Mitre Attack
RT @MITREattack: Coinciding with @jamieantisocial's and his #ThreatHuntingSummit talk, we've just released part 1 of a blog series by ATT&CK team member @Cyb3rPandaH on a proposed method of enhancing an often overlooked part of ATT&CK, data sources. Check it out at
https://t.co/9Yh74So4Kf. https://t.co/uhy73oBhW4
OpenDefining ATT&CK Data Sources, Part I: Enhancing the Current State
Outlining a new methodology to extend the concepts around data sources
Five Eyes Cybersecurity Agencies Release Incident Response Guidance
Cybersecurity agencies in Australia, Canada, New Zealand, the United Kingdom, and the United States have published a joint advisory on detecting malicious activity and incident response
U.S. Unveils Cybersecurity Policies for Space Systems
A presidential memorandum made public on Friday by the White House details the cybersecurity principles that should govern space systems
RT @redcanaryco: After responding to a data breach enabled by an AutoIT worm, two of Red Canary’s incident handlers shared a page out of their defensive playbook with @BuiltInColorado. https://t.co/ALrrJDwkGl https://t.co/V4aOMmMpds
OpenBreaking down a breach with Red Canary’s incident handling team
Two Red Canary incident handlers share a page out of their defensive playbook after responding to a data breach enabled by an AutoIT worm.
How Self-Doubt Can Keep Your Security Team Sharp
A healthy dose of self-doubt can go a long way towards keeping us on our toes and continually improving the security posture of our respective organizations
Vulnerability Disclosure: Ethical Hackers Seek Best Practices
Cybersecurity researchers Brian Gorenc and Dustin Childs talk about the biggest vulnerability disclosure challenges in IoT and the industrial vertical.
RT @elastic: We’re teaming up with @sansinstitute for a webinar on best practices for improving visibility with #threathunting.
Join @malwarejake and #ElasticSecurity's @_devonkerr_ on Sept 10 to learn more. Register here → https://t.co/imyVVzYDMg https://t.co/Gr02DCodd6
OpenThreat Hunting for Visibility
Threat Hunting the proactive pursuit and elimination of adversaries before they cause damage and loss can help analysts and security teams better understand where important assets reside, ...
RT @MITREengenuity: If it feels like the MITRE Engenuity Center for Threat-Informed Defense has been a little quiet lately, it’s because we’ve been hard at work with our members on a wide variety of R&D projects. Here’s a look at what we’re planning and why it’s so vital. https://t.co/n8RYipQtpn
OpenAccelerating Threat-Informed Defense: A Collaborative Approach
Today’s cybersecurity challenges are bigger and broader than any given organization, industry sector or national government — that’s why…