Top news of the week: 10.03.2022.
Mitre Attack
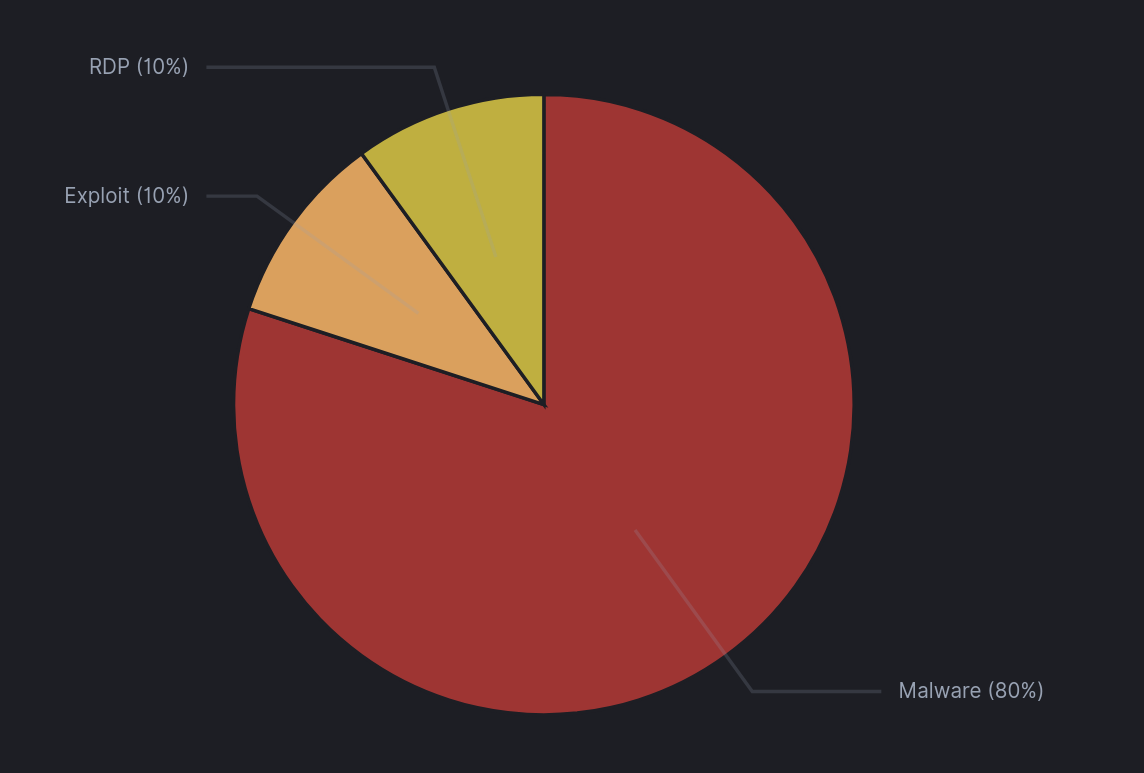
2021 Year In Review
As we come to the end of the first quarter of 2022, we want to take some time to look back over our cases from 2021, in aggregate, and look at some of the top tactics, techniques and ...
Writing Your First Journal Article and Submitting to the Journal of Threat Intelligence and Incident Response
Learn to write and submit your first journal article to the Journal of Threat Intelligence and Incident Response
Operation Purple w/Tim Schulz
Attendees will start by learning the underlying methodologies that make purple teaming successful and metrics for success before diving into leveraging the ATT&CK framework to …
DeTT&CT : Mapping detection to MITRE ATT&CK
Introduction Building detection is a complex task, especially with a constantly increasing amount of data sources. Keeping track of these data sources and their appropriate detection rules ...
Threat Hunting: From LOLBins to Your Crown Jewels
In certain combinations, some chains of behavior represent an advantage to an attacker - your team must be able to differentiate between benign use vs. the abuse of legitimate tools and ...
Why the World Needs a Global Collective Cyber Defense
This sort of approach would enable cross-company and cross-sector threat information sharing, an effort that would allow companies to easily turn data into actionable insights.
Google to Buy Mandiant, Aims to Automate Security Response
In a deal worth $5.4 billion, Google would expand its security portfolio with managed detection and response (MDR) and threat intelligence, with an increasing focus on automation.
How attackers sidestep the cyber kill chain
Many of the most popular cyberattacks don't follow all the steps of the cyber kill chain, but you have other methods to detect threats.