Top news of the week: 09.03.2021.
Mitre Attack
Detecting HAFNIUM Exchange Server Zero-Day Activity in Splunk
This blog discusses how to detect HAFNIUM activity around the recent CVEs released affecting Exchange Server using Splunk and Splunk Enterprise Security.
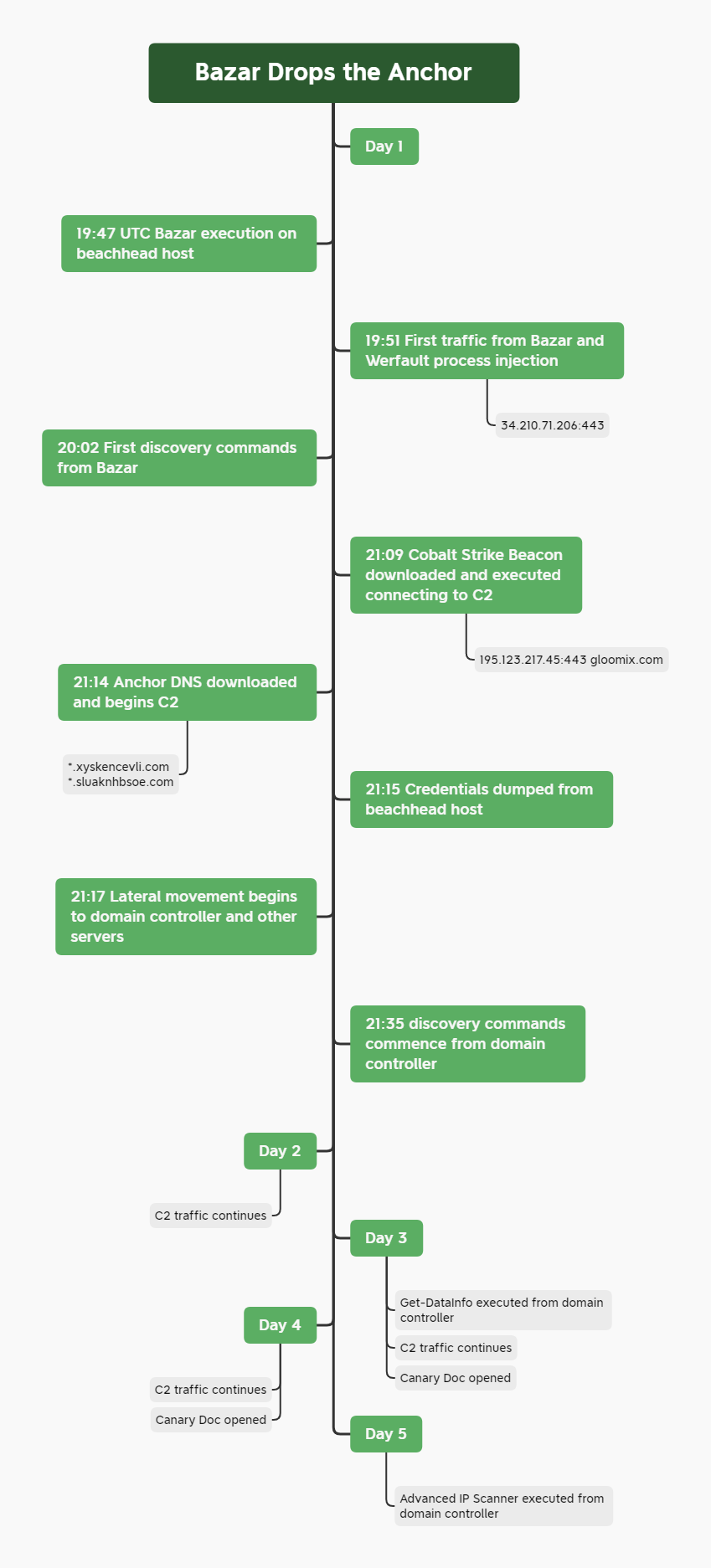
Bazar Drops the Anchor
Intro The malware identified as Anchor first entered the scene in late 2018 and has been linked to the same group as Trickbot, due to similarities in code and usage … Read More
Multiple Airlines Impacted by Data Breach at Aviation IT Firm SITA
A data breach at SITA, a company that specializes in air transport communications and IT, has impacted multiple airlines and hundreds of thousands of their customers.
Microsoft Shares Additional Mitigations for Exchange Server Vulnerabilities Under Attack
Microsoft released alternative mitigation measures for organizations using Exchange Server who have not been able to immediately apply emergency out-of-band patches.
Ransomware is a multi-billion industry and it keeps growing
An analysis from global cybersecurity company Group-IB reveals that ransomware attacks more than doubled last year and increased in both scale and sophistication.
SEC505: Securing Windows and PowerShell Automation
Designed for security operations team members, SEC505 teaches students how to secure Windows Server and Windows 10 with PowerShell automation.
Trust in Tech - How advanced hackers operate
Mi., 7. Apr. 2021, 18:00: You read about it in the news all the time, company X got breached by advanced hackers, hackers gained full control of customer x.How do they manage to get in? How ...