Top news of the week: 05.05.2022.
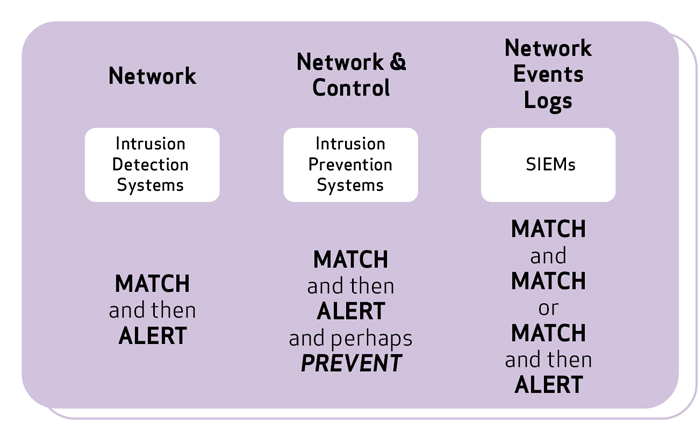
Mitre Attack
Security Stuff Happens: What Do You Do When It Hits the Fan?
Breaches can happen to anyone, but a well-oiled machine can internally manage and externally remediate in a way that won't lead to extensive damage to a company's bottom line. (Part 1 of a ...
Cybersecurity M&A Roundup: 37 Deals Announced in April 2022
37 cybersecurity-related merger and acquisition (M&A) deals were announced in April 2022.
Solving the Incident Response (IR) Data Problem
Join Cybereason’s Jim Hung and IBM’s Head of Research for X-Force John Dwyer, as they discuss the current state of Incident Response (IR), and demonstrate how a combination of IBM X-Force’s ...
Operation CuckooBees: Deep-Dive into Stealthy Winnti Techniques
Cybereason investigated multiple intrusions targeting technology and manufacturing companies located in Asia, Europe and North America. Based on the findings of our investigation, it ...
Why Intelligence Based Detections in ICS Fail
Threat intelligence plays an integral role in cybersecurity, but industrial control system (ICS) environments offer unique challenges. Let's dig into the basics of intelligence-based ...
Operation CuckooBees: A Winnti Malware Arsenal Deep-Dive
This research zeroes in on the Winnti malware arsenal and includes analysis of the observed malware and the complex Winnti infection chain, including evasive maneuvers and stealth ...
Old Services, New Tricks: Cloud Metadata Abuse by UNC2903
Mandiant identified exploitation of public-facing web applications by UNC2903 to harvest and abuse AWS credentials.
Cybersecurity Services
Intelligence-driven information security services and solutions to help organizations predict, prevent, detect and respond rapidly to cyberattacks.