Top news of the week: 02.02.2021.
Mitre Attack
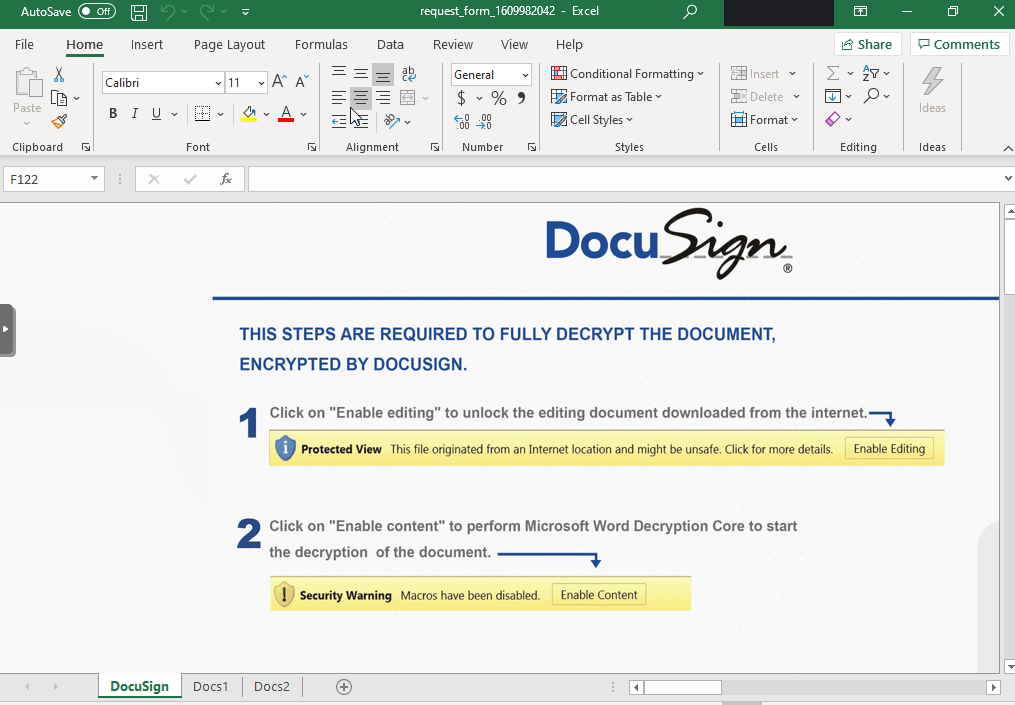
Bazar, No Ryuk?
In this case, we will describe how the threat actor went from a DocuSign themed, malicious document, to domain wide compromise, using Bazar (KEGTAP) and Cobalt Strike.
ZINC attacks against security researchers
In recent months, Microsoft has detected cyberattacks targeting security researchers by an actor we track as ZINC. Observed targeting includes pen testers, private offensive security ...
Cybereason Partners with Ensign to Provide Managed Detection and Response Services in APAC
Partnering with Ensign enables cyber defenders to take the fight directly to the adversary across endpoints, the enterprise and everywhere cyber battles are fought.
Applied Purple Teaming w/ Kent Ickler & Jordan Drysdale 4 Sessions – 4 Hour Classes
Students will have an opportunity to attack their own in-class Active Directory environment with Red Team tactics, implement Blue Team defensery, and manage an environment …
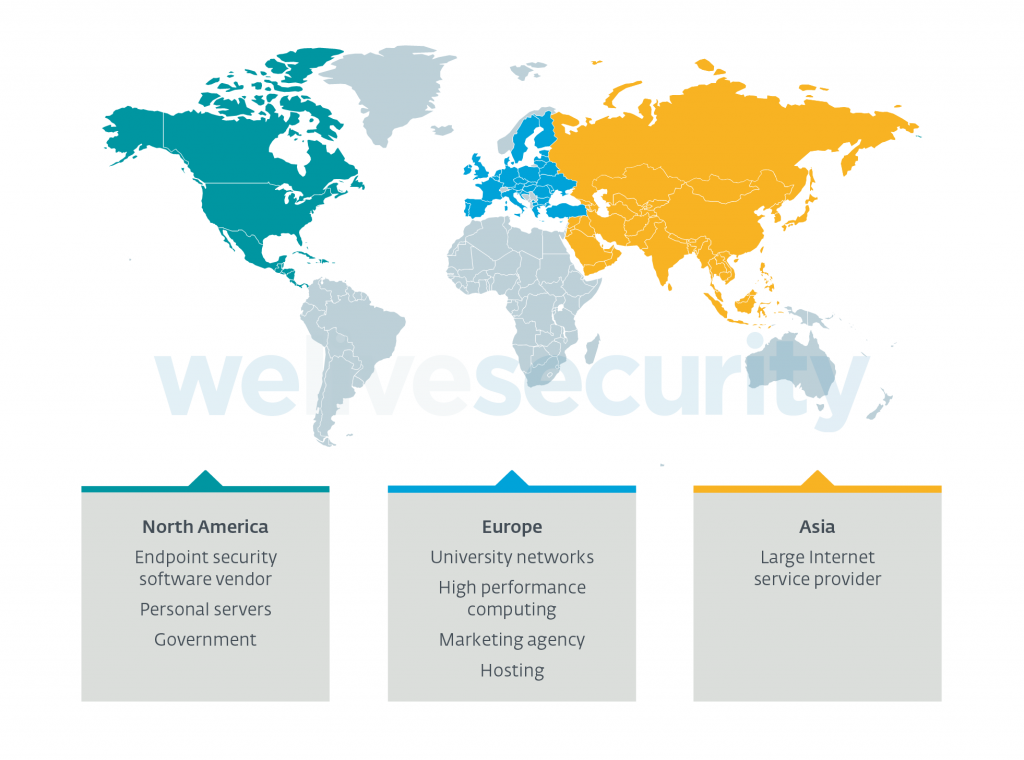
Kobalos – A complex Linux threat to high performance computing infrastructure
ESET uncovers previously unknown and complex multiplatform malware that goes after high performance computing (HPC) clusters and other high-profile targets.
How decision-making psychology can improve incident response
Challenging biases and engaging in regular drills can keep your incident response team sharper than once-a-year wargames.
Attack Emulation Tools: Atomic Red Team, CALDERA and More w/ Darin and Carrie Roberts 4 Sessions – 4 Hour Classes
Instructors: Darin and Carrie Roberts Includes: 16 hours of hands-on interactive learning Purple Team tracking and reporting with Vectr Interactive Exercises (Labs) Mitre ATT&CK …
Postal address
CIRCL provides a reliable and trusted single point of contact for any users, companies and organizations in Luxembourg. CIRCL is made of a team of experts, who react promptly and ...