#IBM #incidentresponse #webinar
Computer forensics, Computer security, Information security, Security, Reverse engineering, Forensic science
Solving the Incident Response (IR) Data Problem
Join Cybereason’s Jim Hung and IBM’s Head of Research for X-Force John Dwyer, as they discuss the current state of Incident Response (IR), and demonstrate how a combination of IBM X-Force’s expertise paired with Cybereason’s cutting edge security tools and DFIR capabilities deliver a ...
Solving the Incident Response (IR) Data Problem
Join Cybereason’s Jim Hung and IBM’s Head of Research for X-Force John Dwyer, as they discuss the current state of Incident Response (IR), and demonstrate how a combination of IBM X-Force’s ...
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Mitre ATT&CK
Please click on:
Subscribe to Cybersecurity - Mitre ATT&CK
Solving the Incident Response (IR) Data Problem
About the Webinar Join Cybereason’s Jim Hung and IBM’s Head of Research for X-Force John Dwyer, as they discuss the current state of Incident Response (IR), and demonstrate how a ...
Solving the Data Problem Within Incident Response
Discover what's needed in your incident response technology to overcome the IR data problem.
SANS Women in Cybersecurity Forum
We've reached the registration limit for the Live Online version of this event. To be notified when the archived recording is available, please email [email protected] would be ...
Revamped Anchor Malware Targets Windows Systems
Researchers believe that attackers behind the Anchor malware, the Trickbot gang, have ceased Trickbot operations are instead focusing on deploying stealthier versions of other malware ...
Work From Home Is Complicating Cybersecurity Investigations
Coronavirus distancing has meant remote investigations, virtual coordinating and a lag in response time, experts say.
ARU CSNRG, OWASP Cambridge, BCS Cybercrime Forensics “Cyber Threat Intellig...
ARU CSNRG, OWASP Cambridge, BCS Cybercrime Forensics “Cyber Threat Intelligence Workshop” 2019 Thursday 24th January 2019 10:00 – 15:30, Coslett Building (COS313), Anglia Ruskin University, ...
TrickBot malware now crashes researchers’ devices to evade analysis
Follow us on Twitter @HackRead - Facebook @ /HackRead
Digital Forensics Investigator: A Road Few Have Traveled
Hunting and finding evil is an incredibly important, fascinating, and equally challenging career path. Perhaps you’ve considered it at one…
Cyberwarfare Report, Vol. 5, No. 4: Hostile Nation-State Threats Sweep The Globe
Diary of international cyber aggression Sponsored by INTRUSION
Come See FireEye at RSA Conference 2019
See what FireEye is up to at RSA Conference 2019.
IBM X-Force Incident Response and Intelligence Services
Proactively manage your security threats with the expertise, skills and people of IBM X-Force incident response and intelligence services.
Best Incident Response Tools for MSPs and MSSPs in 2022
Cybersecurity will continue to be a major issue in 2022. Here are 18 incident response vendors MSPs can partner with.
Adopting more tools doesn’t necessarily improve security response efforts
Security response efforts are hindered by the use of too many security tools, as well as a lack of specific playbooks for common attack types.
Is Your Ransomware Incident Response Plan Future-Proof?
Even amongst organizations that have built a formal cybersecurity incident response plan, only about a third have playbooks for specific types of attacks
The Cybersecurity 202 Network:\
Experts from across government, the private sector and security research community will vote on the most pressing issues in the field.
Module 8: DevSecOps
Join the experts from AWS and DevOps Institute to learn about integrating DevSecOps practices, processes, and technology into each phase of your software delivery workflows.
NICE 2019 Spring eNewsletter
| Featured Article | Academic Spotlight | Industry Spotlight | Government Spotlight | Affiliated Program Updates |...
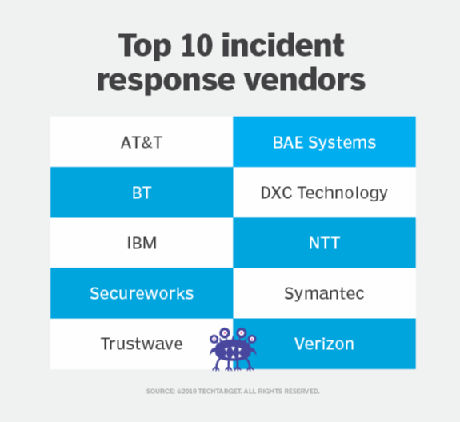
Top 10 incident response vendors for 2019
Learn how managed security services from leading incident response vendors -- including AT&T, BAE Systems, BT, DXC Technology, IBM, NTT, Secureworks, Symantec, Trustwave and Verizon -- ...
Automation and ML, essential tools for the public sector
Organizations that invest in automation have far lower costs caused by data breaches for those that don’t. Discover the tools that everyone should adopt!