#cspm #compliance
Cloud computing, Security guard, Risk, Information security, Computer security, Security
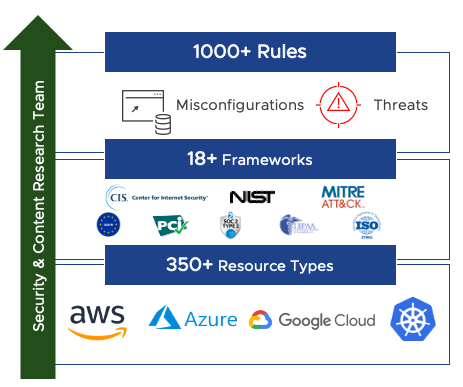
Falcon Horizon CSPM
CrowdStrike Horizon streamlines cloud security posture management enabling you to deploy applications in the cloud with speed & efficiency. Learn more here!
Falcon Horizon CSPM
CrowdStrike Horizon streamlines cloud security posture management enabling you to deploy applications in the cloud with speed & efficiency. Learn more here!
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Mitre ATT&CK
Please click on:
Subscribe to Cybersecurity - Mitre ATT&CK
Runtime Protection: The Secret Weapon for Stopping Breaches in the Cloud
Runtime protection via cloud workload protection works with CSPM tools to enhance cloud security. Learn how to build a better defense.
Top 100 Cybersecurity Startups to Look Out for in 2021
The increase in the intervention of technology in our life has raised the need for cybersecurity solutions. The Top 100 cybersecurity start-ups listed by Analytics Insight have exclusive ...
Cybersecurity experts ponder looming 2019 threats
CISOs may not agree on what the challenges are but all agree they must be proactive
These are the Top Network Security Companies in America (2021)
This article showcases our top picks for the best America based Network Security companies. These startups and companies are taking a variety of approaches to innovating the Network ...
A Brief Introduction to Red Hat Advanced Cluster Security for Kubernetes
In this blog post, we will discuss the OpenShift security use cases that Red Hat Advanced Cluster Security for Kubernetes addresses and identify the benefits of taking a Kubernetes-native ...
Mitigating Security Risk in the Cloud(s)
Is your Cloud Security Posture keeping you awake at night?
VMware Future-Ready Workforce Solutions Announced
VMware Future-Ready Workforce solutions provide great workforce experiences, end-to-end Zero Trust security controls & simplified management
RSA Conference 2020: Product Announcement Summary (Day 2)
SecurityWeek's daily digest summarizing product and service announcements made on Day 2 (Tuesday) of the 2020 RSA Conference.
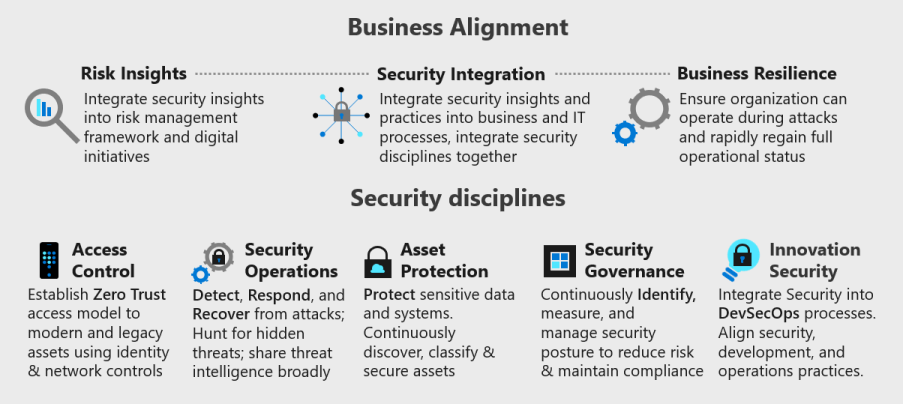
Security in the Microsoft Cloud Adoption Framework for Azure
Use the Cloud Adoption Framework for Azure to learn how to integrate security throughout your cloud adoption journey.
3 Major Benefits of Cloud Migration: Automation
Learn more about how automated security controls, policies, and scans can simplify security with your migration to the cloud.
Managed Cloud Security Starts at Level 1 with AWS Level 1 MSSP Competency Partners
A Managed Security Service Provider (MSSP) can integrate, join forces with, and work alongside in-house security teams, or provide full outsourcing for AWS security operations. To help ...
JupiterOne Automates Asset Management, Security, Compliance
JupiterOne tackles asset management with automation, a graph database to understand the connections, visualizations and a tool to build and enforce security and compliance policy.
Why Effective Security Operations Is the Key Defense Against Ransomware
MSSPs & MSPs need to partner with someone that can automatically & continuously map, profile, and classify assets on a network -- to see and protect the attack surface, Arctic Wolf asserts.
Overcoming security metrics challenges to measure what matters
While many organizations may realize they can’t entirely eliminate cyber risk, they still need to quantify their security efforts and set thresholds to show whether they’re trending ...
9 strategic cybersecurity outcomes CISOs should focus on
Here are nine strategies that have surfaced recently in interviews with cybersecurity pros that you can put to work to achieve cyber resilience.
Cybersecurity Courses & Certifications
SANS offers over 50 hands-on, cyber security courses taught by expert instructors. We offer live courses at training events throughout the world as well as virtual training options ...
What Does Cloud-Native Mean for Security?
The best cloud-native security tools provide real-time detection of rogue instances, unauthorized access, and cyber attackers within the perimeter.
PCI Compliance.
The most complete, accurate, and efficient solution to achieve PCI compliance.
Cybersecurity Engineer, Mid
Cybersecurity Engineer, MidThe Challenge:Everyone knows security needs to be “baked in” to a system architecture, but you actually know how to bake it in. You can identify and implement ...