#IncidentResponse #ransomware
Attack, Malware, Biometrics, Economics, Detection theory, 28 Days Later
Detections and Defensive Insights From the ContiLeaks
Learn more about Webinar - Detections and Defensive Insights From the ContiLeaks from TrustedSec, the leading US security consulting team.
Detections and Defensive Insights From the ContiLeaks
Learn more about Webinar - Detections and Defensive Insights From the ContiLeaks from TrustedSec, the leading US security consulting team.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Mitre ATT&CK
Please click on:
Subscribe to Cybersecurity - Mitre ATT&CK
Modern Ransomware’s Double Extortion Tactics and How to Protect Enterprises Against Them
Contents Modern Ransomware Case Study: Nefilim 13 Shifts in Criminal Business Models 5 Conclusion 52 Appendix 55 Published by Trend Micro Research Written by Mayra Fuentes, Feike ...
Click here to read the article
Category T2-T3 2020-2021 Key points in T3 2021 Overall threat detections +7.2% ↑ -16.0% Top threat: HTML/Phishing.Agent trojan Infostealers -15.2% ↓ N/A Rise in banking malware Ransomware ...
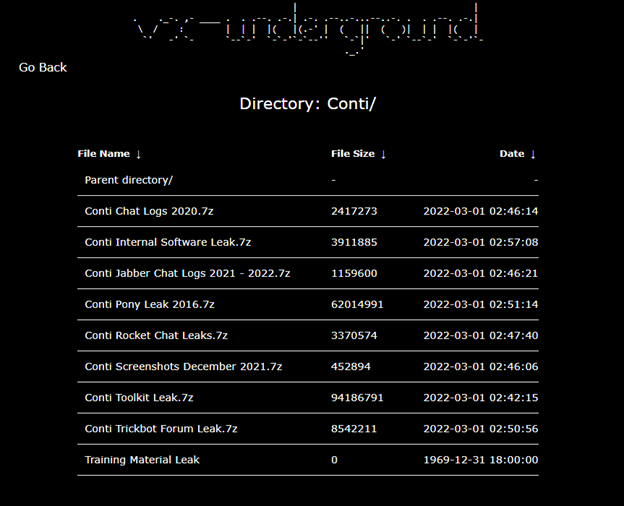
Conti Group Leaked!
The conflict in Ukraine has driven significant attention from the cybersecurity community, due in large part to the cyber attacks conducted against Ukraine infrastructure — including ...
Striking Back: Hunting Cobalt Strike using Sysmon and Sentinel
Striking Back: Hunting Cobalt Strike using Sysmon and Sentinel Wednesday, February 24 from 1-2pm EST Presented by Binary Defense and TrustedSec Cobalt Strike is a powerful adversary ...
Why You May Not Need to Monitor the Dark Web
To understand which industries can truly benefit from dark web monitoring we must first understand what it is – and what it isn’t.
Protect Your Organization From MosaicRegressor and Other UEFI Implants
The recent discovery of MosaicRegressor spyware is the latest in an ongoing trend of UEFI implants observed in the wild. Eclypsium detects these attacks, and shows you how to defend your ...
Cyberthreats to financial institutions 2020: Overview and predictions
Short overview of year's key events, analysis of forecasts for 2019 and our predictions about cyberthreats to financial institutions in 2020
‘Zombie’ Ryuk ransomware group returns from the grave
A prolific ransomware actor seemingly disappeared earlier this year. Now they're back with a vengeance, most recently linked to a string of hospital attacks.
Intelligence Insights: January 2022
Log4j target found in VMware Horizon, new BLISTER loader may contain Cobalt Strike beacons, and ManageEngine exploitation continues.
Cybersecurity : The Winner’s Game and The Loser’s Game
There is a seminal paper in finance by Charles Ellis called the The Loser’s Game which, in simple terms, foretells the move from active to passive investing and the reasons for it. My ...
What’s Next in the Evolution of Complex RansomOps?
Remember, the actual ransomware payload is the tail end of a RansomOps attack, so there are weeks or even months of detectable activity where a ransomware attack can be disrupted before ...