#MalOp #XDR #ZeroTrust #cybersecurity
Cloud computing, Computer security, Security, Information security, Default judgment, Access control
How Cybereason XDR Supports Zero Trust Initiatives
Cybereason XDR addresses the five core pillars of Zero Trust: device, identity, network, application workload and data...
How Cybereason XDR Supports Zero Trust Initiatives
Cybereason XDR addresses the five core pillars of Zero Trust: device, identity, network, application workload and data...
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Mitre ATT&CK
Please click on:
Subscribe to Cybersecurity - Mitre ATT&CK
Zero Trust Race is On: Do You Have the Right Engine?
The automated correlation capabilities within Cybereason Advanced XDR ensures identities, authentication and authorization to cloud accounts, endpoints and devices takes a Zero Trust ...
CrowdStrike Redefines True XDR With Humio Acquisition
Read about the acquisition of Humio here
Cross-Layered Detection and Response (XDR): A Welcome New Entry in the Cybersecurity Alphabet Soup
Cross-layered detection and response (XDR) takes security solutions to the next level by helping IT pros weed through the fog of more.
How agencies can make the shift to zero trust
Zero trust requires an integrated security platform that covers the endpoint, the cloud and every data point in between.
Open XDR - the Intelligent Next Gen Security Operations Platform
Open XDR security operations platform - automatically collects, normalizes and correlates all security data from multiple security products into a single platform.
Open XDR vs. SIEM
Matching Resources and Business Risk with the Right Solution Gaining visibility and responding to attacks across the entire enterprise infrastructure (endpoints, servers, applications, ...
Government IT decision makers worried about security risks related to cloud migration
Nearly 70% of U.S. government IT decision makers surveyed view security risks as the top barrier to the process of cloud migration.
A flaw in Microsoft OAuth authentication could lead Azure account takeover
A vulnerability in the Microsoft OAuth implementation exposes Azure cloud accounts to takeover. The vulnerability affects the way Microsoft applications use OAuth for authentication, these ...
Q&A: Heather Adkins, director of information security, Google
What follows is the transcript of a Security Conversations podcast interview with Google security leader Heather Adkins. We discuss her role at the search advertising giant, the ...
Cloud presents biggest vulnerability to ransomware
Veritas Technologies surveyed more than 2,000 global IT leaders whose organizations have undertaken pandemic-led digital transformation and found the majority are severely vulnerable to ...
Biden’s Cybersecurity Executive Order Puts Emphasis on the Wrong Issues
David Wolpoff, CTO at Randori, argues that rapid cloud transition Is a dangerous proposition: "Mistakes will be made, creating opportunities for our adversaries.
Microsoft and NIST collaborate on EO to drive Zero Trust adoption
Learn how Microsoft is helping federal agencies to implement standards-based cybersecurity technologies such as NIST and Zero Trust in the real world.
How to Simplify Zero Trust Adoption
By Bhavya Pathak, Product Marketing Manager, ColorTokens Gone are the days when an organization could trust everything within the four walls of its perimeter. Cloud computing, and ...
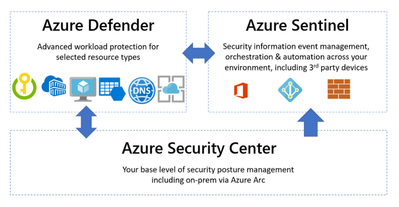
Meeting the Cybersecurity Executive Order requirements with Azure Security
In May 2021, the Biden Administration signed Executive Order (EO) 14028, placing cloud security at the forefront of national security. Federal agencies are at different stages in their ...
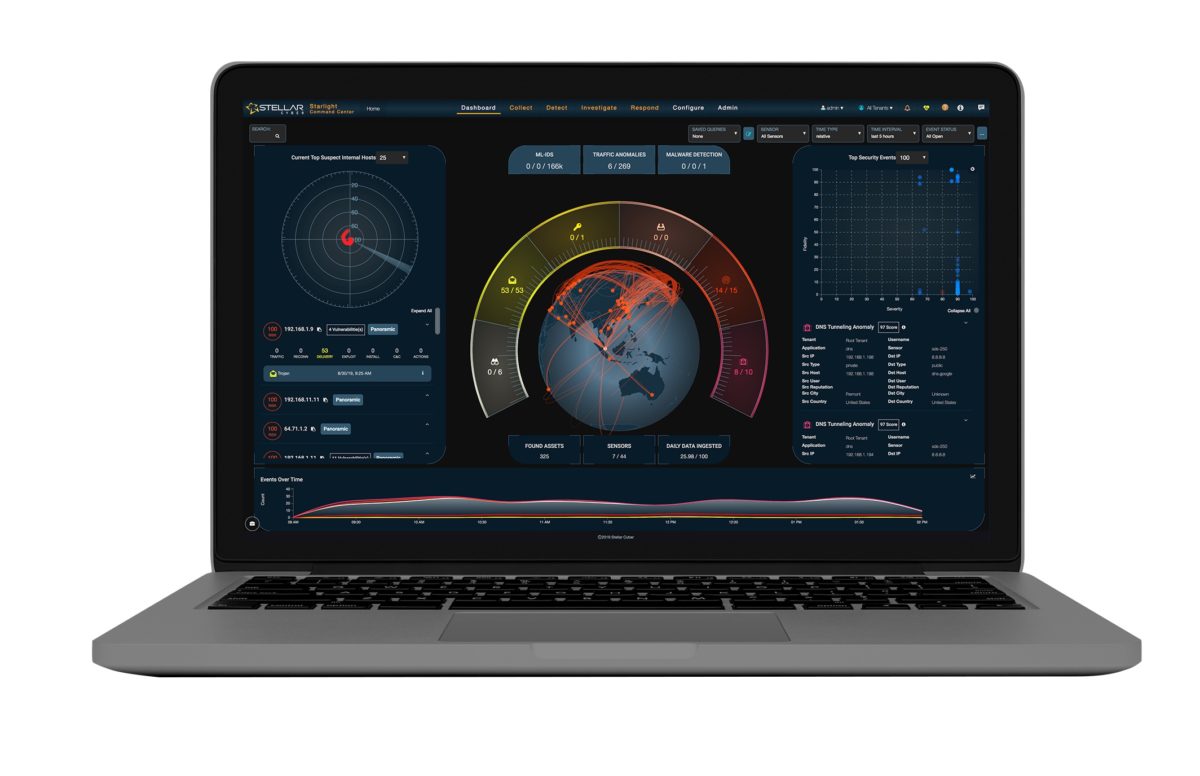
Stellar Cyber Intelligent Security Operations Platform
Open XDR is a cohesive security operations platform with many natively supported security tools while seamlessly integrating with third party tools. XDR
memcached (UDP/11211)
In this edition of our NICER Protocol Deep Dive blog series, we take a closer look at the internet exposure of memcached.
USDA Virtual Expo Series
By providing integration, automation, compliance, and performance at scale, Fortinet offers federal agencies world-class solutions for on-premises perimeter security, secure remote access, ...
Verizon DBIR 2021: "Winners" No Surprise, But All-round Vigilance Essential
Verizon's Data Breach Investigations Report (DBIR) covers 2020 -- a year like no other. Phishing, ransomware, and innovation caused big problems.
The demise of the perimeter and the rise of the security platform.
In this article we look at the challenges and solutions for organisations trying to cope with the seismic shift in enterprise networking.