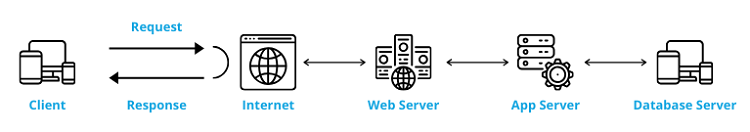
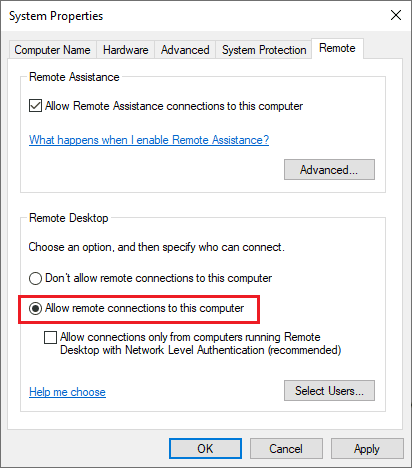
Personal computer, Web 2.0, Web development, Remote desktop, Windows NT, ASP.NET
Blue Mockingbird Is Mining Cryptocurrency
“If you have public-facing web servers you should be concerned about this." @ForensicITGuy spoke to @InfosecMag about the Blue Mockingbird cryptominer. https://t.co/vvlUblzeaa
OpenNew cyber-threat spotted deploying Monero cryptocurrency-mining payloads on Windows machines
“If you have public-facing web servers you should be concerned about this." @ForensicITGuy spoke to @InfosecMag about the Blue Mockingbird cryptominer. https://t.co/vvlUblzeaa
OpenBlue Mockingbird Is Mining Cryptocurrency
New cyber-threat spotted deploying Monero cryptocurrency-mining payloads on Windows machines
We are sorry, we could not find the related article
If you are curious about Cybersecurity Essentials and Mitre ATT&CK
Please click on:
Or signup to our newsletters
Blue Mockingbird Monero-Mining Campaign Exploits Web Apps
The cybercriminals are using a deserialization vulnerability, CVE-2019-18935, to achieve remote code execution before moving laterally through the enterprise.
Intelligence Agencies Share Web Shell Detection Techniques
The NSA and Australian Signals Directorate issued a joint Cybersecurity Information Sheet (CSI) that provides details on vulnerabilities exploited by threat actors to install web shell ...
Ghost in the shell: Investigating web shell attacks
Web shell attacks allow adversaries to run commands and steal data from an Internet-facing server or use the server as launch pad for further attacks against the affected organization.
5 techniques that will help you check web application security
5 techniques that will help you check web application security
Web shell malware continues to evade many security tools
Cyber attackers are increasingly leveraging web shell malware to get persistent remote access to compromised networks, the NSA and the ASD warn.
Types of Web Application Firewalls (WAFs) — How to Choose a WAF?
Note: This is a guest post written by Adam Dawson Web Application Firewall — or WAF — is a specialized firewall for web apps that protects your public-facing applications from a wide array ...
Microsoft Warns of New Wormable RDP Flaw
Three months after BlueKeep, there's a new set of RDP vulnerabilities in town—and this time, they affect Windows 10.
Microsoft Issues Patches for Pair of Wormable Flaws Similar to BlueKeep
Two wormable flaws have been discovered in the remote desktop services function of multiple Microsoft Windows platforms, which could be remotely exploited by a hacker to launch malicious ...
Microsoft Patch Tuesday addresses dangerous RDS flaw that opens to WannaCry-like attacks
Microsoft Patch Tuesday updates for May 2019 address nearly 80 vulnerabilities, including an RDS flaw allowing WannaCry-Like attacks. Microsoft Patch Tuesday updates for May 2019 address ...
What is the latest RDP client for Windows 10 and its alternatives
Are you looking for the latest RDP client for Windows 10? Check out some updates and some of its ideal alternatives! Read More
Continuous Deployment on Azure with Visual Studio 2019 and GitHub
To understand these concepts quickly and easily, we will carry out the process of continuous implementation of a web application whose development is carried out from Visual Studio 2019, ...