Top news of the week: 10.05.2022.
Innovations And Trends
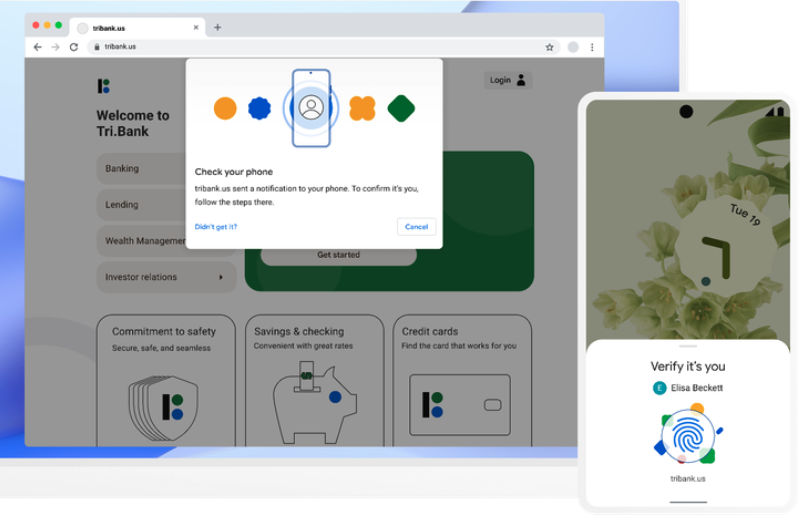
Your Phone May Soon Replace Many of Your Passwords
Apple, Google and Microsoft announced this week they will soon support an approach to authentication that avoids passwords altogether, and instead requires users to merely unlock …
Cybersecurity in the IoT World: How Telcos Can Secure Critical Infrastructure Against New Threats Featured
Over the last year, threat actors have launched a series of major attacks on critical infrastructure, an industry fast becoming one of the most targeted by threat actors.
Google, Apple, Microsoft make a new commitment for a "passwordless future"
Passwords may soon be a thing of the past now that these major tech companies have extended support for passwordless FIDO sign-in standards.
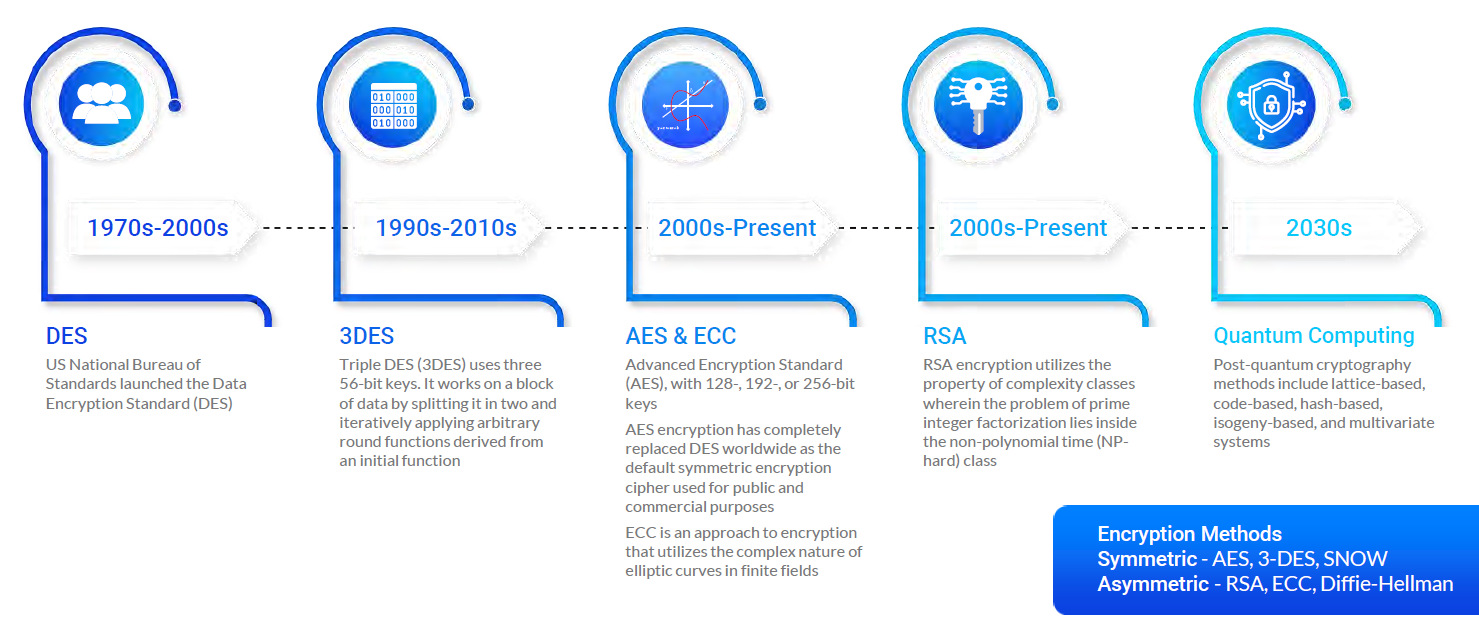
Post-Quantum Cryptography Set to Replace RSA, ECC
In the next 10 years, public-key encryption needs to be replaced by post-quantum techniques that can stand up to the new challenges.
Chinese hackers took trillions in intellectual property from about 30 multinational companies
"We're talking about Blueprint diagrams of fighter jets, helicopters, and missiles," Cybereason CEO Lior Div told CBS News.
Researchers discovered a sophisticated malware framework, dubbed NetDooka, distributed via a pay-per-install (PPI) malware service known as PrivateLoader.
Researchers discovered a sophisticated malware framework, dubbed NetDooka, distributed via a pay-per-install (PPI) malware service known as PrivateLoader. Trend Micro researchers uncovered ...
Is the password passé this World Password Day?
For tech experts, World Password Day highlights the importance of identity security and leveraging that to practice what the industry calls zero trust.
Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations
Table D-3: Objective 3 – Implementation milestones to position the enterprise as an industry leader in C-SCRM …