Top news of the week: 21.05.2020.
#Cybersecurity #security #infosec #risk #COVID19 #malware #Cybercrime #DPO #dataprotection #law
Threats And Attacks
British airline EasyJet said it had suffered a "sophisticated" cyber attack, uncovering names and travel details of about nine million customers amid raised concerns over coronavirus-fuelled Internet hacking https://t.co/1tuHWgVVcZ
OpenEasyJet Reveals Cyber Attack on Nine Million Clients
British airline EasyJet said it had suffered a "sophisticated" cyber attack, uncovering names and travel details of about nine million customers amid raised concerns over ...
Elexon, a company involved in managing the electricity market in the UK, reported being hit by a cyberattack that impacted its internal IT systems. https://t.co/OcFKVb0Szq
OpenUK Electricity Market Administrator Elexon Targeted by Hackers
Elexon, a company involved in managing the electricity market in the UK, reported being hit by a cyberattack that impacted its internal IT systems.
Innovations And Trends
RT @cybersecboardrm: This new, unusual Trojan promises victims COVID-19 tax relief #Cybersecurity #infosec #security https://t.co/EGpgmtb9px
OpenThis new, unusual Trojan promises victims COVID-19 tax relief
QNodeService’s codebase may have helped it avoid detection by traditional antivirus solutions.
Industrial Network Cybersecurity: Debunking the Myths and Adopting Best Practices https://t.co/gETFuF8wxm #Cybersecurity #Cybercrime https://t.co/O6hB7A4Ygt
OpenIndustrial Network Cybersecurity: Debunking the Myths and Adopting Best Practices
Why is cybersecurity so often overlooked by Operational Technology engineers? The answer can be traced to four common myths. Here, we explore why these four misconceptions are no longer ...
Data Privacy
RT @marktigheST: Tusla is first to be fined by Data Protection Commision over three GDPR breaches
https://t.co/mFiaCLGpQ7
OpenTusla fined by Data Protection Commision over three GDPR breaches
Tusla, the child and family agency, has become the first body to be fined in Ireland for a data protection breach using new powers given to the regulator following the introduction of the ...
RT @armstrongjp: Can a #compliance head be a #DPO under #GDPR? a recent Belgium decision suggests not https://t.co/LuqoJbkKXh #dataprotection #law #eudatap #privacy
OpenBelgian Regulator Imposes Euro 50,000 Fine for Non-Compliance with Data Protection Officer GDPR Requirements
Introduction Under the EU General Data Protection Regulation (“GDPR”), where certain conditions are met it is mandatory for an organisation to designate a Data Protection Officer (“DPO”). ...
Startups And Investments
https://t.co/uHGnNLqJTx
🆕HACKER NOON TOP STORY >>Ten Underground Tech Masterminds You Probably Haven't Heard Enough About, by Carlo @carloocchiena.
#StoryOfTheDay https://t.co/FlXX09sbtt
OpenTen Underground Tech Masterminds You Probably Haven't Heard Enough About
The history of technology, intended here in a narrow sense as the history of information technology, rests on the shoulders of a small handful of giants.
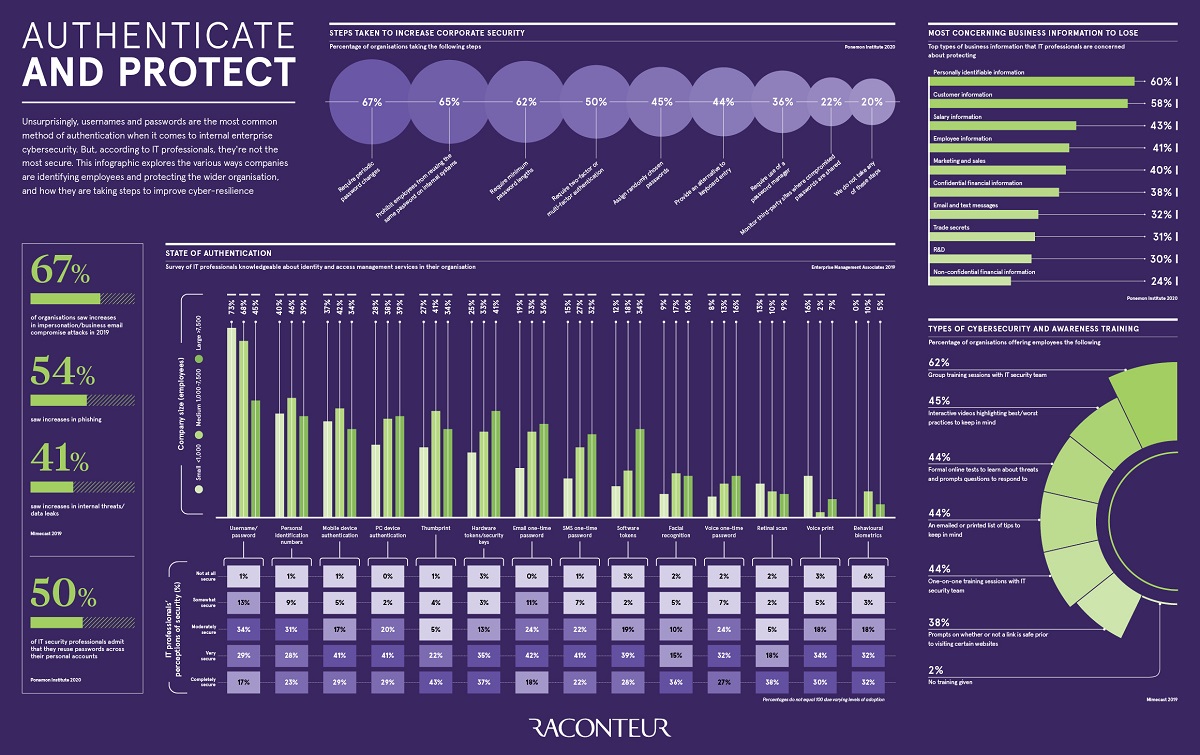
A report by @raconteur explores the various ways companies are identifying employees and protecting the wider organization, and how they are taking steps to improve cyber-resilience. https://t.co/AS8xIkBAtR @antgrasso_IT #IAM #CyberSecurity #Passwords https://t.co/0e48KHMNgg
OpenAuthenticate and Protect
Unsurprisingly, usernames and passwords are the most common method of authentication when it comes to internal …
Companies And Services
To adapt for the current crisis, security exceptions and changes were made. To navigate your #digital future, @steveschlarman shares why you need a plan for managing #risk more than ever: https://t.co/oHgYwjbX1V https://t.co/J4rGv0y7G5
OpenLay the Foundations of Digital Risk Management
Integrated risk management is now a critical measure of success.
RT @helpnetsecurity: CISOs are critical to thriving companies: Here's how to support their efforts - https://t.co/5cfJprUA9f - #securitynews #ITsecurity @teramindco #CISO #infosec #cybersecuritynews https://t.co/1rMl7ehkZb
OpenCISOs are critical to thriving companies: Here’s how to support their efforts
CISOs may be struggling, but they are immensely talented and uniquely important. It’s time to support their efforts in meaningful and tangible ways.
Business And Industries
What is the Zero Trust Framework in cybersecurity and 5 considerations for building a Zero Trust IT environment #Cybersecurity #security https://t.co/lb4p11e5X3
OpenWhat is the Zero Trust Framework in cybersecurity and 5 considerations for building a Zero Trust IT environment
What is Zero Trust? Zero Trust isn’t a product or service, and it’s certainly not just a buzzword. Rather, it’s a particular approach to cybersecurity. It
Cyberinsurance firms want to know more about you security practices, especially for remote workers, @JimRundle reports, as the #pandemic heightens cybersecurity risks https://t.co/W8BFmT1dI7 via @WSJ @WSJCyber
OpenCyber Insurers Get Tough on Risk Assessments Amid Coronavirus Pandemic
Cyber insurers, leery of security risks created by remote working and other effects of the coronavirus pandemic, are stepping up scrutiny of policyholders’ security arrangements. These ...