Robbery, Malware, Copyright infringement, Theft, Crime, Larceny
'Raccoon Stealer' Scurries Back on the Scene After Hiatus
Researchers this week said they had observed criminals using a new and improved version of the prolific malware, barely three months after its authors announced they were quitting.
'Raccoon Stealer' Scurries Back on the Scene After Hiatus
Researchers this week said they had observed criminals using a new and improved version of the prolific malware, barely three months after its authors announced they were quitting.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and General News
Please click on:
Subscribe to Cybersecurity - General News
New Raccoon Stealer Campaign Underscores an Evolving Threat
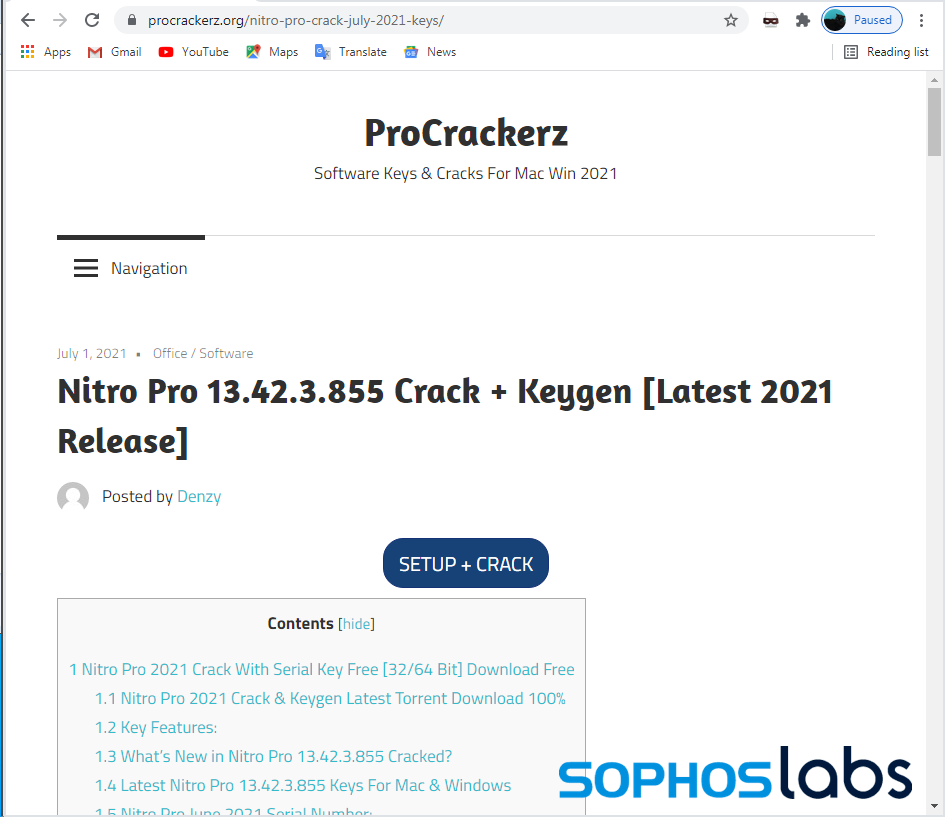
An information stealer disguised as pirated software targets cryptocurrencies and data while dropping malicious content on infected devices.
Malware droppers for hire targeting users on fake pirated software sites
Follow us on Twitter @HackRead
Seven Kinds of Malware, and all Arrive by Social Engineering
Naked Security outlines seven different categories of malware and describes how each of them through social engineering techniques can affect your organization.
Malware explained: Definition, examples, detection and recovery
Malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs attackers use to wreak destruction and gain access to sensitive ...
Researchers Spot New Cryptocurrency Stealing Malware Advertised Under a Subscription Model
All news about Bitcoin, technology blockchain and cryptocurrency. Financial technologies, startups.
Raccoon stealer-as-a-service will now try to grab your cryptocurrency
The malware has been upgraded to target even more financial information.
New BHUNT malware targets your crypto wallets and passwords
A novel modular crypto-wallet stealing malware dubbed 'BHUNT' has been spotted targeting cryptocurrency wallet contents, passwords, and security phrases.
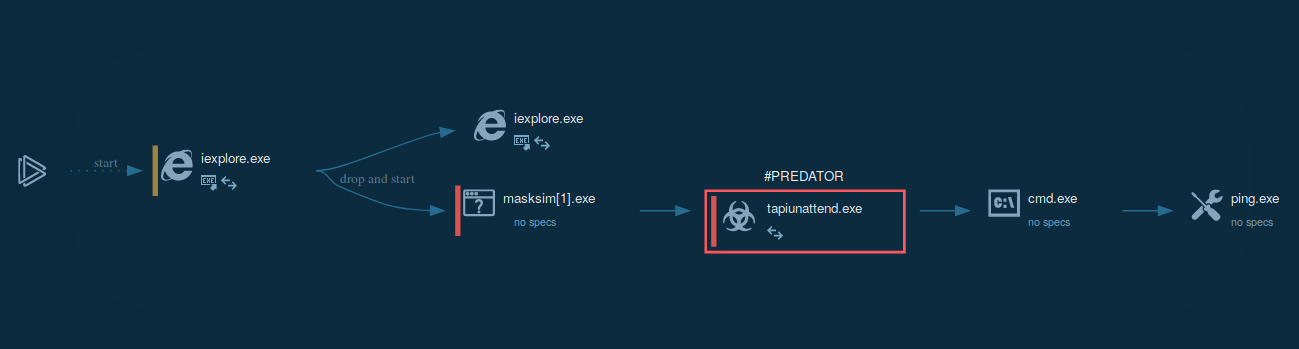
General description of Predator the Thief
Predator the Thief is an information stealer type malware used by attackers to collect information from infected machines. Follow live malware statistics of this trojan and get new reports, ...
Analysis of BlackGuard - a new info stealer malware being sold in a Russian hacking forum
In this blog, ThreatLabz analyzes BlackGuard, an emerging an info stealer malware being sold as a service on a Russian hacking forum.
CISA: Detections of LokiBot Info-Stealer Are Soaring
Widespread Trojan menace trips agency’s IDS alarms
Someone is passing around Valorant beta keys that are actually malware
Hackers are trying to exploit widespread interest in Valorant's close beta in an attempt to steal gamers’ username and password credentials.
To Disseminate Malware, Hackers are Increasingly Relying on DaaS Platforms
Malware authors are increasingly relying on DaaS platforms to distribute their malicious creations.
The Daily Ledger
Get The latest cybersecurity news from across the web delivered to your inbox each day.
Cheap Malware Behind Surge in Attacks on Cryptocurrency Wallets
Redline is just one example of malware being designed to steal cryptocurrency and there's a growing market in this space.
A new variant of the HawkEye data stealer emerges in the threat landscape as part of ongoing malware distribution campaigns.
A new variant of the HawkEye data stealer emerges in the threat landscape as part of ongoing malware distribution campaigns.
Trash Panda as a Service: Raccoon Stealer steals cookies, cryptocoins, and more
Cookie and credential stealing malware-as-a-service delivered by dropper-as-a-service now packs a “clipper” to steal crypto-transactions, and can drop other malware.
Experts Say Equifax Data Breach Was A Spy Job
Remember all that stolen Equifax data? Remember how all those names, addresses, dates of birth, Social Security and drivers’ license numbers and other information were stolen in September ...
Attacks Using Lokibot Information Stealer Surge
The U.S. Cybersecurity and Infrastructure Security Agency is warning of an uptick in attacks using Lokibot, an information stealer capable of sweeping up
France says hackers might go after supply chains after Airbus cyber assault
France has issued a new cyber threat advisory about targeted espionage operations directed at service providers and engineering firms.