Top news of the week: 30.11.2022.
3 Cybersecurity Tips- How To Secure Critical Assets and Data
Cybercriminals also target organizations’ data in attempts to hold the businesses and organizations to ransom—more or less like an “I’ve got my hands on your data, or I now have …
Policies for SaaS Apps, Shadow IT Prove Difficult to Manage
Despite spending up to 10% of their revenue on SaaS applications, organizations lack policies to not only manage them but to manage shadow IT as well.
Helen Yu’s Post
Cybersecurity Ventures predicts that by 2031, ransomware will cost victims $265 billion annually, and it will attack a business, consumer, or device every... 10 comments on LinkedIn
Trio of new vulnerabilities allow code manipulation, denial of service (and worse) for industrial controllers
The bugs allow for logic manipulation and denial of service, primarily impacting products from two major German vendors: Festo automated controllers and CODESYS runtime.
How APAC organisations are hiring cyber security pros
Hiring managers in cyber security are turning to existing employees in non-IT roles and providing professional development for junior-level staff to plug the talent gap
Attackers target vulnerable financial customers, rather than the institutions themselves
A new report from Akamai also found a massive 257% increase in the number of web applications and API attacks against the financial services sector in the past year.
CTA Webinar - When What Didn’t Happen Is More Interesting
2022 was the year when what didn’t happen was more interesting than what did happen. Despite the Russian invasion of Ukraine, widespread cyber attacks outside of the immediate combat zone ...
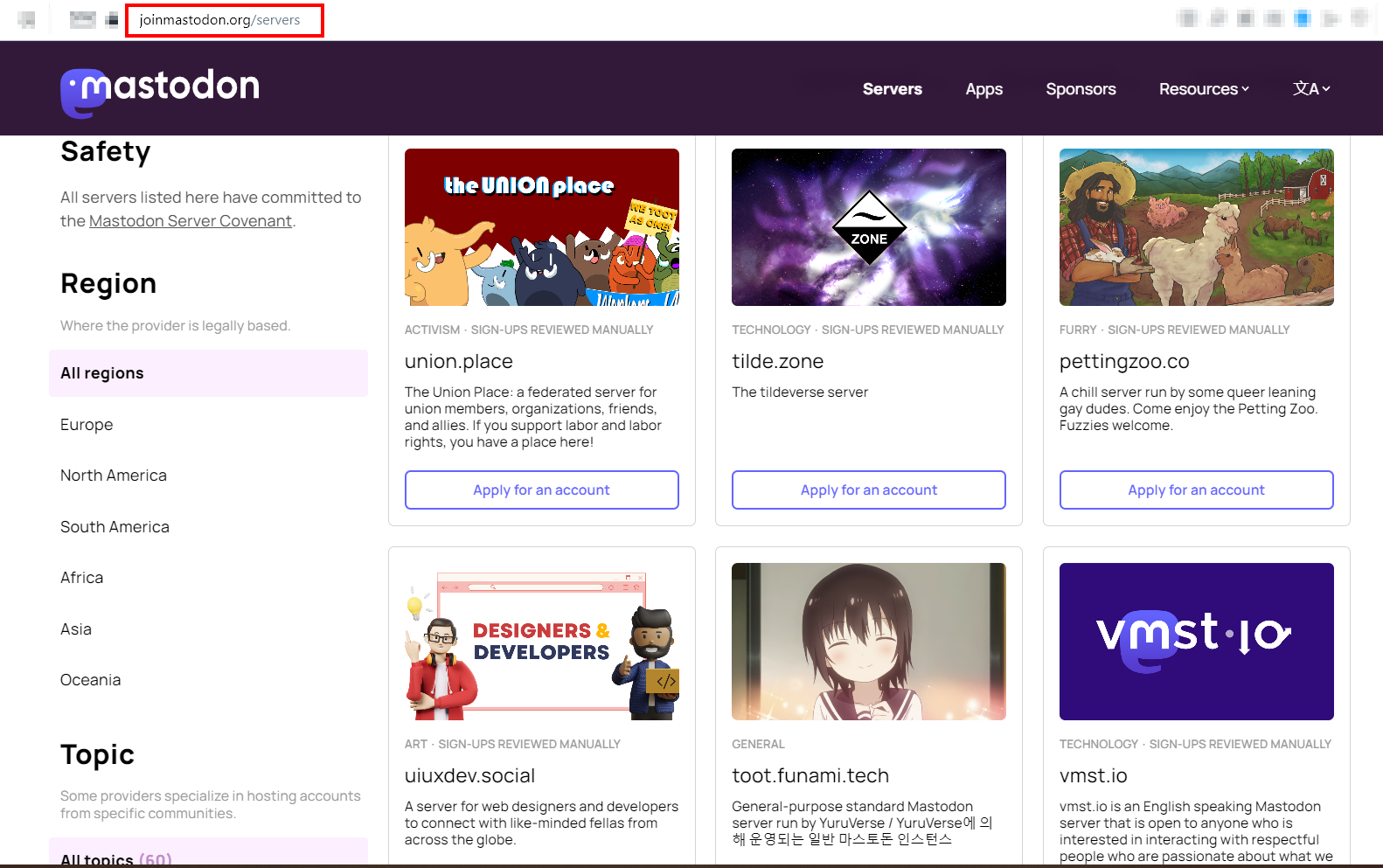
Mastodon OSINT: A Comprehensive Introduction
Part one in our series on Mastodon, focused on gathering OSINT from the platform's users, instances and network.