Email, Organization, Cloud computing, Microsoft, Risk, Phishing
Palo Alto Networks: 80% of security exposures exist in cloud
Palo Alto Networks Attack Threat Surface Report determined that 80% of security exposures exist in cloud.
Palo Alto Networks: 80% of security exposures exist in cloud
Palo Alto Networks Attack Threat Surface Report determined that 80% of security exposures exist in cloud.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Companies and Services
Please click on:
Subscribe to Cybersecurity - Companies and Services
Week in review: Critical RCE in Palo Alto Networks firewalls, how to select a DRaaS solution
Here's an overview of some of last week's most interesting news, articles and interviews: Critical RCE in Palo Alto Networks (PAN) firewalls revealed,
Top 3 ransomware attack vectors and how to avoid them
Learn how to protect systems from the most common ransomware attack vectors: phishing, RDP and credential abuse, and exploitable software vulnerabilities.
Cyber Insights 2023 | Supply Chain Security
Development tools, languages and frameworks are being targeted by threat actors who understand the impact from software supply chain attacks.
10 Best Cloud Security Tools – 2023
Best Cloud Security Tools and software -1. Cloudflare 2. Zerospam 3. CrowdStrike Falcon 4. QualysSplunk Enterprise 5. Centrify 6. CyberArk
Winners | Cybersecurity 2023
19th Annual 2023 Globee® Cybersecurity Awards winners Grand Trophy Winners (Alphabetically) AttackIQBishop FoxCyberGRXEndaceIvantiLattice SemiconductorManageEngineOpenTextRevBitsStrikeReady ...
Hundreds of federal network devices fail new CISA security requirements
An attack surface analysis of more than 50 civilian agencies found widespread noncompliance with a recent Binding Operational Directive.
Cyber-Threat Detections Hit a Record-Breaking 146 billion in 2022
/PRNewswire/ -- Trend Micro Incorporated (TYO: 4704; TSE: 4704), a global cybersecurity leader, today announced a massive 55% increase in overall threat...
BeyondTrust PAM vs. DarkSide Ransomware
BeyondTrust’s Privileged Access Management platform protects your organization from unwanted remote access, stolen credentials, and misused privileges
10 Top Cloud Security Companies in 2023
Protecting the cloud is a top priority for organizations across all industries. In this article, you'll learn about the top cloud security companies.
Endpoint Security and Network Monitoring News for the Week of February 10; Skybox Security, PureSquare, Sonatype, and More
Solutions Review have curated this list of the most noteworthy endpoint security and network monitoring news for the week of February 10.
Notorious botnet starts spamming again after a three-month pause
Notorious botnet starts spamming again after a three-month pause
Modernize your cybersecurity environment with XDR and SIEM
As cloud computing grows more widespread and people, applications, data, and identities become more dispersed, security teams need a better way to increase visibility and track threats ...
Palo Alto Networks beats earnings forecast amid slower cybersecurity spending
Palo Alto Networks beats earnings forecast amid slower cybersecurity spending - SiliconANGLE
5 ways CISOs can prepare for generative AI’s security challenges and opportunities
An effective zero-trust framework can help reduce the blast radius of generative AI attacks and establish a first line of defense.
The Evolution Of Cybersecurity And How Businesses Can Prepare For The Future
Cybersecurity used to be a problem only for CISOs, but as the world becomes more remote and digital, I predict it will become an enterprise-wide priority.
QBot: Laying the Foundations for Black Basta Ransomware Activity
In this blog, a timeline of techniques in a real-world attack by Black Basta affiliates using the QBot banking trojan, plus how to protect yourself.
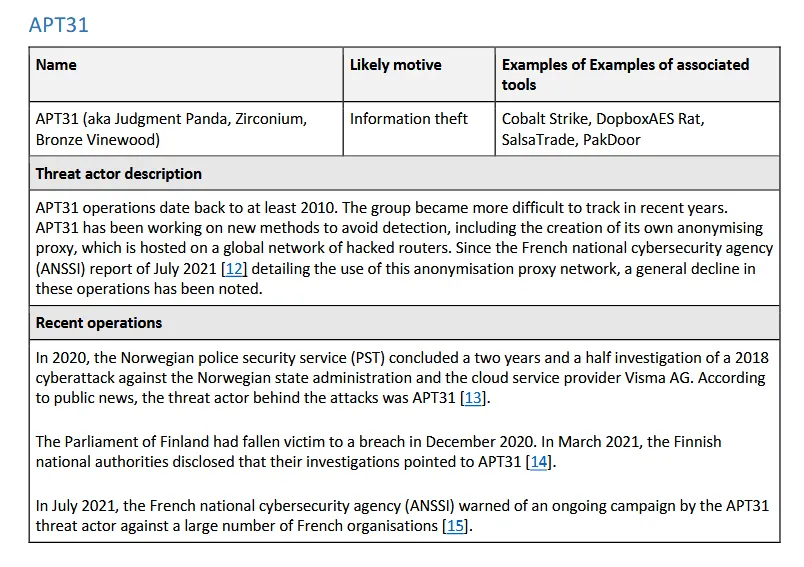
Risky Biz News: EU cybersecurity agencies warn of Chinese APT spying
In other news: Israeli company behind global election meddling campaigns; Atlassian confirms data leak; Belgium launches national vulnerability disclosure framework.
Attackers Took 5 Minutes to Start Scanning for Exchange Server Flaws
Research underscores the acceleration of attack activity and points to a growing concern that defenders can't keep pace.
Cloud CISO Perspectives: January 2023
In his January newsletter, Cloud CISO Phil Venables revisits two megatrends: the cloud as a digital immune system and software-defined infrastructure.
Malicious scans for at-risk systems start minutes after disclosure
New statistics collated by Palo Alto Networks reveal malicious actors begin scanning the internet for systems at risk of new CVEs within minutes