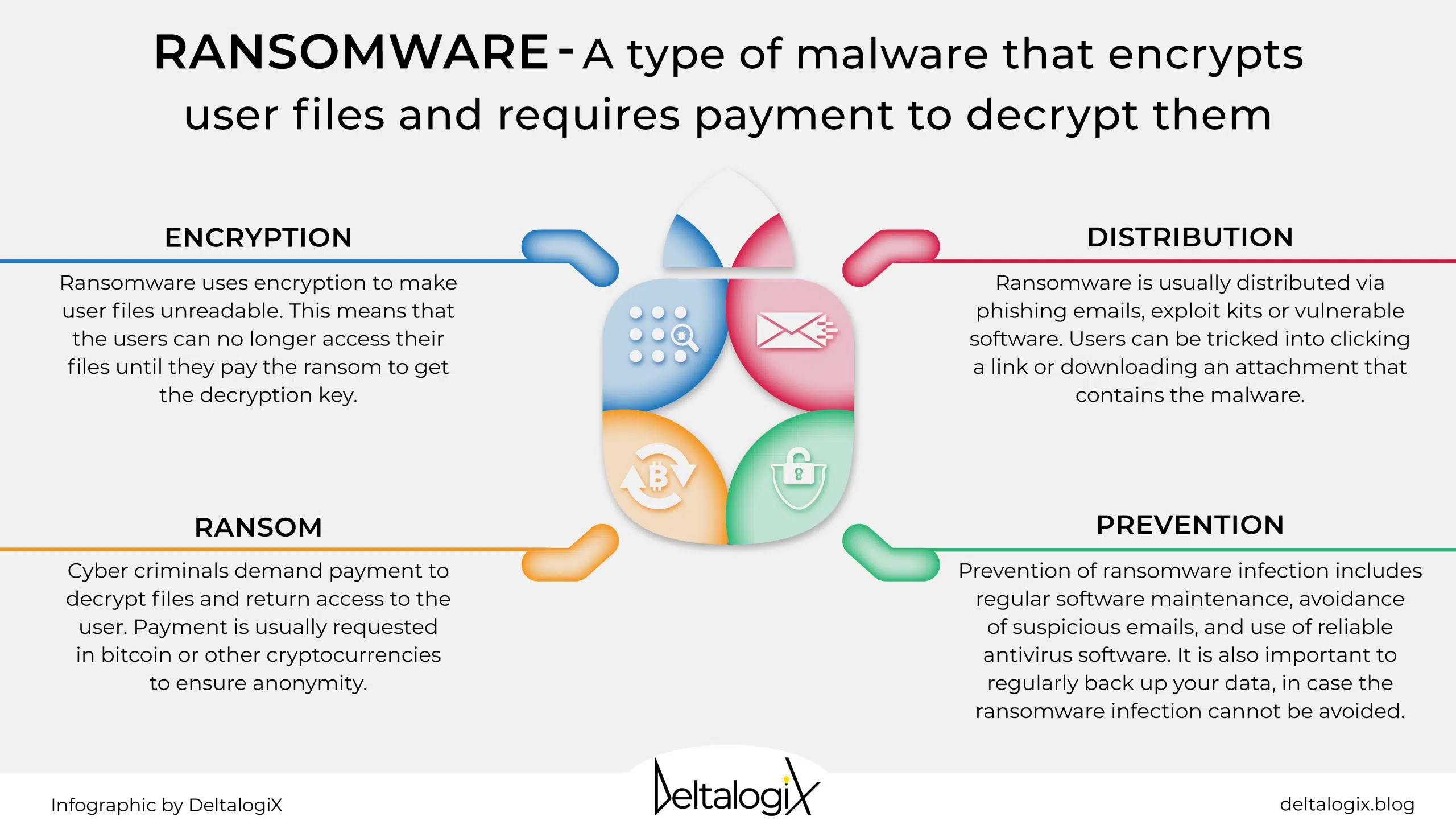
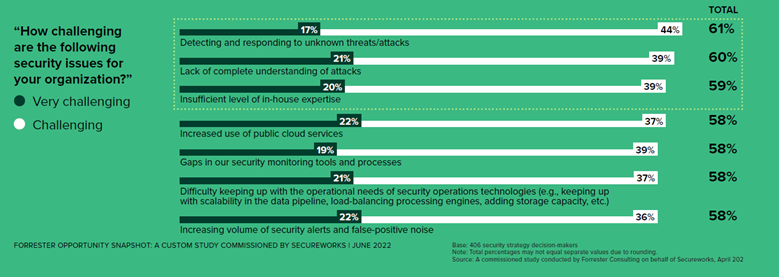
Organization, Phishing, Malware, Computer security, Extortion, Ransomware
Cybersecurity training for employees is the most popular IT investment among US companies this year
Cybersecurity training for employees, as well as the purchase of cybersecurity solutions/services (61% each), are the most popular IT investments among US businesses this year
Cybersecurity training for employees is the most popular IT investment among US companies this year
Cybersecurity training for employees, as well as the purchase of cybersecurity solutions/services (61% each), are the most popular IT investments among US businesses this year
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Companies and Services
Please click on:
Subscribe to Cybersecurity - Companies and Services
Cybersecurity is the most common IT expense - but are firms spending enough?
Cybersecurity is the most popular category of spending, survey finds
How SMBs Can Prepare for Identity-based Attacks in 2023
The cybersecurity threat to small- and medium-sized businesses (SMBs) continues to grow as cybercriminals recognize both how vulnerable
How to Build Ransomware Protection Packages That Clients Want
For the average small–to–mid-sized business, ransomware is a matter of life and death. Problem is, they may not know it.
Ransomware: an evolving cyber attack
Ransomware continues its evolution through sophisticated and deceptive attacks whose danger you need to know about to defend yourself
Cyber Apocalypse 2023: Is the World Heading For A “Catastrophic” Event?
As the 2023 annual meeting of the World Economic Forum wrapped up in Davos, Switzerland, it ended with a disturbing prediction from one of the leading voices.
Security Incidents Have Moved Beyond the Endpoint — Shouldn’t You?
Endpoint detection and response security is no longer keeping up with cyber threats. Here’s why it’s time to modernize your cybersecurity.
FBI and CISA Release Cybersecurity Advisory on Royal Ransomware Group
The FBI and CISA have released a joint Cybersecurity Advisory discussing the Royal ransomware group.
Celerium Compromise Defender detects and disrupts cyber compromise activity
As an integral part of Celerium's Cyber Defense Network, Compromise Defender provides early detection and defense of compromise activity.
Crackdown on ransomware gangs yet to show an impact: OpenText
Law enforcement triumphs over the Hive, Conti and REvil ransomware gangs in the last 12 months haven't blunted the use of the technology, says a new report from OpenText. "Despite these ...
Be Prepared: Top Ransomware Prevention Tips for 2023
Protect yourself from the rising threat of ransomware attacks in 2023. Learn the top prevention tips to keep your data and devices safe.
What, exactly, is cybersecurity? And why does it matter?
Cyberattacks steal data and cause millions in economic costs. Learn what cybersecurity professionals do and how to protect your data with our guide.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of the capabilities of the recently emerged Royal ransomware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of the capabilities of the recently emerged Royal ransomware. The human-operated Royal ransomware first appeared ...
Top 10 SaaS Cybersecurity Threats You Must Know in 2023
Be aware of the SaaS cybersecurity attacks before they result in data breaches. Here are the top 10 SaaS cybersecurity threats that you must know.
Why should cybersecurity become top priority for SMEs
Technology for MSMEs: SMEs can no longer delay investing in cybersecurity if they want to keep their business safe and operational. With the threats getting more sophisticated and intense, ...
Assessing Cybersecurity Risk in the C-Suite
In today's digital age, cybersecurity risks are a major concern for businesses of all sizes. With cyber attacks becoming more sophisticated and frequent, it is important for businesses to ...
Ransomware gangs force cybersecurity teams to reassess
In today’s threat climate with ransomware proliferating, companies need a more proactive approach to cybersecurity awareness.
US government warns Royal ransomware is targeting critical infrastructure
The federal advisory warns that the Royal ransomware is targeting critical infrastructure sectors across the United States.
Researcher create polymorphic Blackmamba malware with ChatGPT
Follow us on Twitter @Hackread ---Facebook @ /Hackread
What to Do After a Data Breach: Surviving the First 24 Hours
Today data breaches are a costly and ever-present danger for businesses in both the public and private sector. Each year, the total number of reported...