Access control, Policy, Organization, Computer security, Authentication, Security
How an AI governance framework can strengthen security
Explore the essential elements of an AI governance framework, from risk assessment to incident response, and learn how they contribute to enterprise security.
How an AI governance framework can strengthen security
Explore the essential elements of an AI governance framework, from risk assessment to incident response, and learn how they contribute to enterprise security.
We are sorry, we could not find the related article
If you are curious about Cybersecurity and Companies and Services
Please click on:
Subscribe to Cybersecurity - Companies and Services
SAP Security Insights
Introduction As companies increasingly rely on SAP for their ERP system, safeguarding critical assets and sensitive data within the SAP landscape becomes a top priority. This article ...
8 ways to cope with cybersecurity budget cuts
When budget cuts hit cybersecurity teams, businesses often find themselves exposed to significant risk. Learn how security leaders can do more with less.
Top Reasons State and Local Governments Are Targeted in Cyberattacks
Strengthening your defense starts with understanding the top reasons why threat actors choose to target state and local governments. Then, implement the latest technologies and best ...
Searching For Cybersecurity’s Silver Bullet: The Rise Of Zero Trust
Zero trust can’t be implemented as a standalone security product; instead, it is a holistic strategy that relies on a layered approach.
From Zero Trust To Secure Access: The Evolution of Cloud Security
This article covers cloud security evolution, Zero Trust adoption, best practices, and the future impact of AI, with a focus on continuous monitoring.
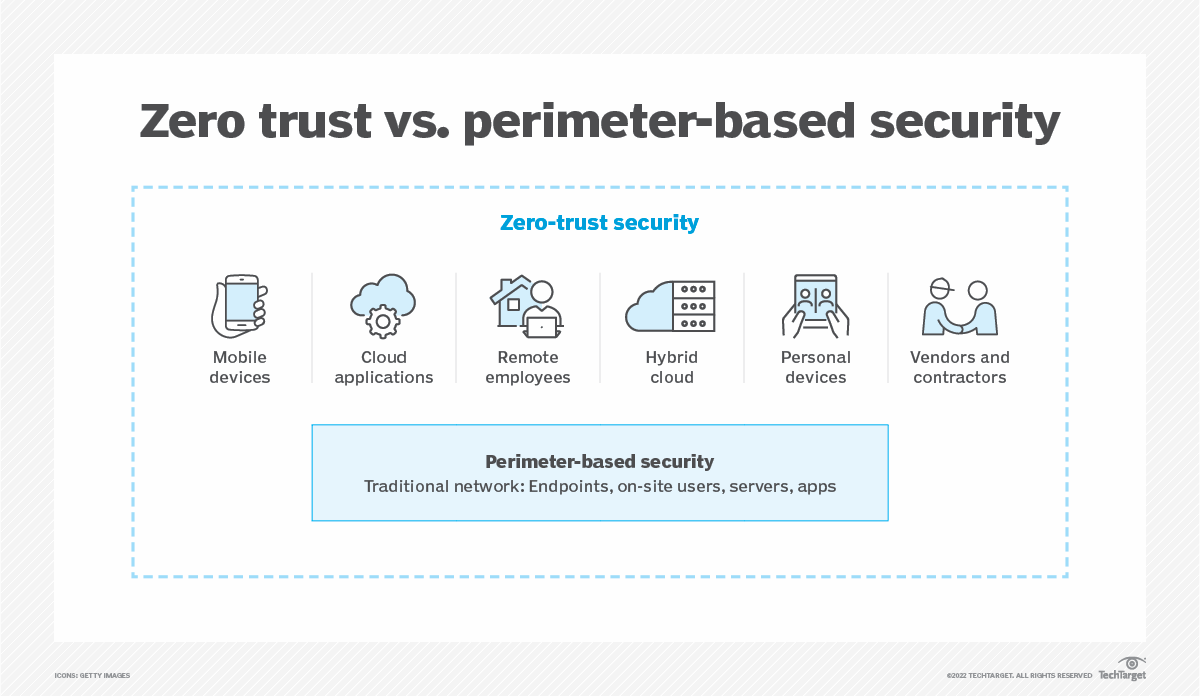
What is zero trust? A model for more effective security
As the security model becomes the preferred security strategy, it’s worth looking at what it is and what it takes to achieve.
MapleSEC: How infosec pros can make their organizations safe for AI
Artificial intelligence applications are a two-edged sword: They can be used by employees to improve productivity and make better products and services, and they can be used by attackers to ...
Good, Perfect, Best: how the analyst can enhance penetration testing results
What is the analyst on a penetration testing team, what role they perform at Kaspersky, and why is their job vital to the success of the project?
Privacera's State Of AI and Data Security Governance Survey: Majority of Businesses (57%) Plan to Utilize a Data Security Platform to Secure Generative AI Models
Privacera announced the results of its latest survey on generative AI data security trends, revealing that an overwhelming majority of business leaders have either implemented or are ...
What to include in an SD-WAN security checklist
An SD-WAN security checklist should cover four important areas: how SD-WAN secures the WAN, SD-WAN security functions, how the SD-WAN platform protects itself and how SD-WAN integrates into ...
Network segmentation takes center stage in new TSA cybersecurity amendment for airport, aircraft operators
Network segmentation takes center stage in US Transportation Security Administration cybersecurity amendment for airport, aircraft operators.
Your Guide to IAM – and IAM Security in the Cloud
As user credentials become a coveted target for attackers, IAM technologies are gaining popularity. But is IAM security enough to protect cloud identities?
The Safety Mandates Every Enterprise Needs – Even with a Secured Cloud Offering
How to take ownership of your data’s security as part of your cloud strategy
Application Security vs. API Security: What is the difference?
Don't confuse application security with API security! Learn the key differences in our latest article.
Building an effective security operations center framework
Organizations with a comprehensive security operations center framework are more likely than others to detect incursions and protect their operations. Learn how to build an effective ...
How Do Security Controls Help Implement a Corporate Security Policy?
A corporate security policy is the cornerstone document of a company’s risk management. Does your business have the appropriate security controls in place to implement the policy, or is the ...
Zero Trust Demystified: 5 Essential and Elusive Questions Answered
Embracing a Zero Trust approach offers a powerful method to strengthening an organization's cybersecurity posture.
Data protection demands AI-specific security strategies
Adoption of AI tools is high across organizations, however many are concerned about the impacts AI will have on their data security strategy.