Cloud computing, Access control, Authentication, Risk, Security, Computer security
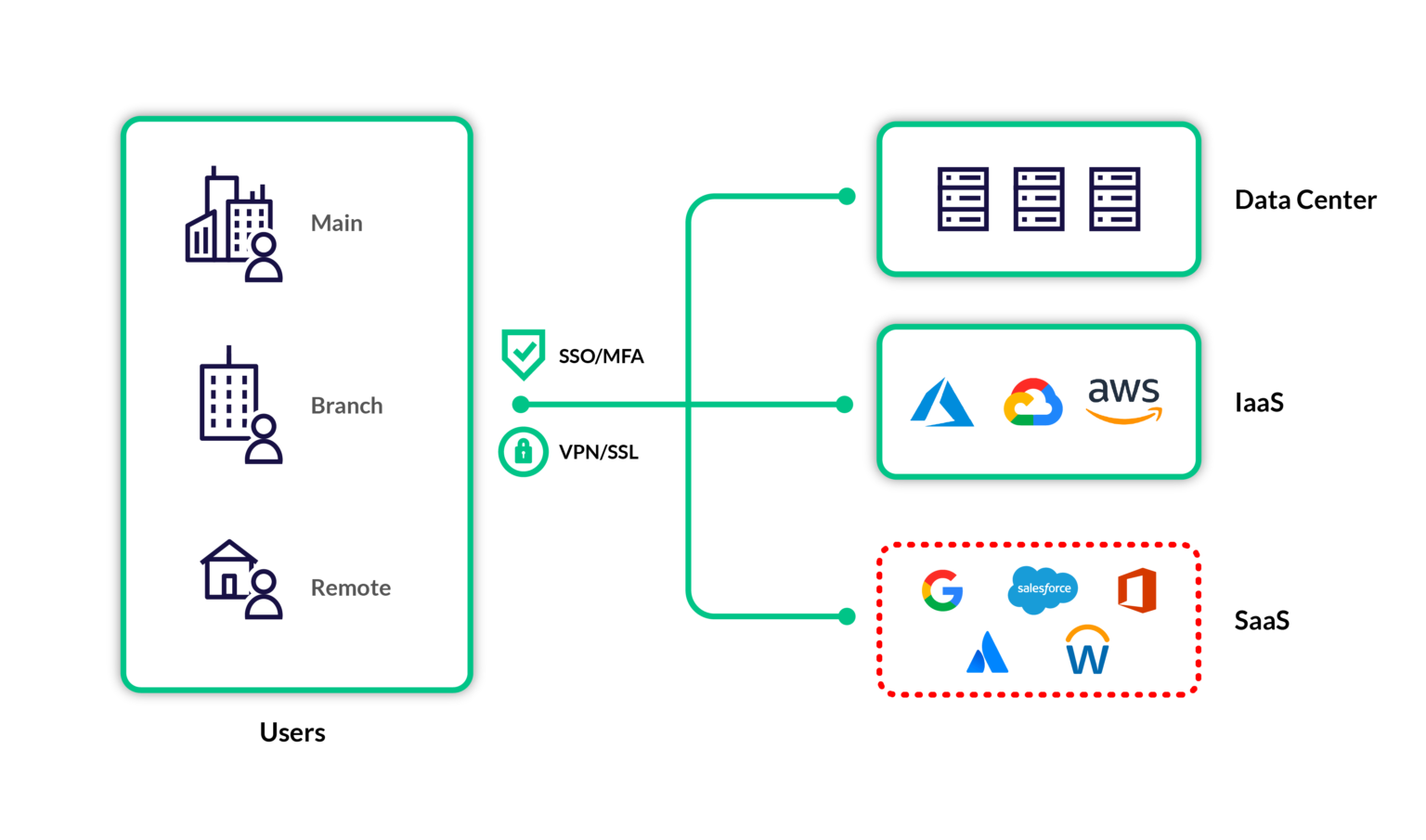
Extending Zero Trust to Your SaaS Applications
It’s been over a decade since former Forrester analyst John Kindervag helped popularize the term “zero trust,” and while the underlying principles aren’t new, the model of “never trust, always verify” has never been more relevant. ...
Extending Zero Trust to Your SaaS Applications
It’s been over a decade since former Forrester analyst John Kindervag helped popularize the term “zero trust,” and while the underlying principles aren’t new, the model of “never trust, ...
We are sorry, we could not find the related article
If you are curious about Artificial Intelligence and General News
Please click on:
Subscribe to Artificial Intelligence - General News
Shifting to a zero trust security model
With cyberattacks such as ransomware becoming more brazen, we can no longer afford to assume that everything behind the corporate security parameters is
Federal Zero Trust Strategy
Read and comment on the U.S. government's draft Federal Zero Trust Strategy. This strategy is intended to accelerate federal agencies towards a shared baseline of early zero trust maturity.
Microsoft Zero Trust deployment guide for your applications
Leverage Microsoft Cloud App Security to secure your digital transformation, by protecting all your apps and resources with the principles of Zero Trust.
Build a Secure Well-Architected Cloud Environment
Explore the Security pillar of the AWS and Azure Well-Architected Framework and be guided through the fundamental security controls for Cloud Architects.
Five steps to securing your identity infrastructure
This document outlines a list of important actions administrators should implement to help them secure their organization using Azure AD capabilities
PKI as the Foundation for Zero Trust
PKI in A Zero-Trust network requires verification of every access request by default. In a network of “never trust,” strong digital identities that can be verified are key to building a ...
Infrastructure + Security: Noteworthy News (October, 2018)
Windows Server What’s new in Active Directory Federation Services (AD FS) in Windows Server 2019 (Ignite video) Active Directory Federation Services (AD FS) continues to be the #1 ...
Vulnerability Summary for the Week of March 8, 2021
The division of high, medium, and low severities correspond to the following scores: High: vulnerabilities with a CVSS base score of 7.0–10.0 Medium: vulnerabilities with a CVSS base score ...
Top Challenges When Securing Cloud Services Today
There are many unique challenges involved with securing cloud services. First, data and applications in the cloud are distributed across many services and platforms; each with its own ...
About Deep Security Smart Check
Deep Security Smart Check also includes an administrator console that provides: a dashboard (system-wide summary of scan information, including metrics) user management registry ...
Fill gaps in your cybersecurity tech stack to meet today’s challenges
Fill gaps in your cybersecurity tech stack to meet today’s challenges How would you feel if you were in charge of IT when a hacker stole $2 million? What would your reaction be if a ...
EXCLUSIVE! Making Zero Trust Government a Reality – OpenGov Asia | #government | #hacking | #cyberattack
“Singapore has moved from preventing cyber threats to assuming breaches have occurred”, said Josephine Teo, Minister for Communications and Information, Singapore. When Minister Josephine ...
The Journey to Zero Trust Begins with Identity
Identity is the fabric that ties the zero trust framework together
Why security pros should care about making zero trust frictionless
Forrester’s zero trust concept has grown in acceptance as we come out of the pandemic. Today’s columnist, Narendran Vaideeswaran of CrowdStrike, writes how AI-powered platforms help ...
Top 100 Cybersecurity Startups to Look Out for in 2021
The increase in the intervention of technology in our life has raised the need for cybersecurity solutions. The Top 100 cybersecurity start-ups listed by Analytics Insight have exclusive ...
Achieving Cyber Vigilance with Zero Trust
Federal government agencies are facing a cyber insurgency. The past year underscored the systemic vulnerability of our government. Security teams are facing increasingly sophisticated ...